Intro to Android Mobile Reverse Engineering

Reverse Engineering Android Apps
Reverse engineering an Android application typically involves using specialized tools to decompile the application's compiled code and resources into a human-readable form. As we go through this blog post, we will discuss the various available tools and examples of how they can be used to find hardcoded data and potentially find static application vulnerabilities.
This process can be challenging, as it requires a certain level of familiarity with Android app development and knowledge of Java. However, with the right tools and expertise, it is possible to reverse engineer most Android applications successfully.
Watch our “Reverse Engineering on Android” webinar on-demand.
Android Reverse Engineering Tools
Several tools can be used for reverse engineering Android mobile applications. Some of the more popular ones include:
- APKtool: A powerful tool for reverse engineering APK files. It can decode application resources to their nearly original form and rebuild them after making code modifications.
- JADX: This is a command-line and graphical tool that can decompile DEX (Dalvik Executable) files and convert them to readable Java source code
- Dex2jar and JD-GUI: dex2jar is a tool used to convert DEX files to java JAR files and then using JD-GUI, which is a Java decompiler that can be used to view the Java source code
- Radare2 (also known as "r2"): This is a free and open-source reverse engineering framework that can analyze, modify, and decompile Android applications.
- Strings: A simple utility that extracts and displays printable strings from a binary file. It can pull strings from Android APK files and be a valuable tool for reverse-engineering Android applications.
It's worth noting that reverse engineering Android applications is a complex process that requires a good understanding of java and smali code. The above list of tools is not exhaustive; instead, many common tools are used to get started with Android reverse engineering.
Android APK Binary Analysis
For this blog post and examples, we will work with an Android vulnerable challenge application publicly available on GitHub, Cybergym- CyberGym GitHub.
Let’s start from the beginning when we have an APK file for deeper analysis. An Android application APK file is essentially a ZIP archive and can be extracted using APKtool from the above list of tools. You can unzip an APK file, but the ability to read all the binary contents will not be there.
Utilizing APKtool, you can run the following command (replacing the binary name if it differs for you).
apktool d com.cybergym.lab1.apk
Once you have decompiled the Android APK file, a folder with the same name will be created. The screenshot below will show an example of a decompiled Android application.
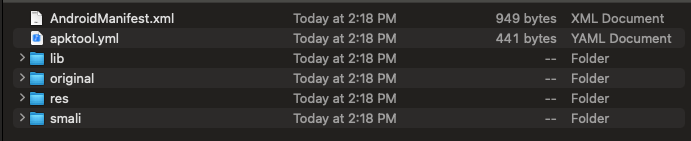
Now that we understand the Android file structure and how to decompile an Android application, we can look into reverse engineering tools and how they can be used to find vulnerabilities or solve application challenges.
CyberGym Level 1
We need to install the application to understand what is required to complete the challenge and use that information; we can use reverse engineering tools and techniques to solve the challenge.
Using a Corellium virtualized device, I installed and launched the CyberGym level one APK, as shown in the screenshot below.
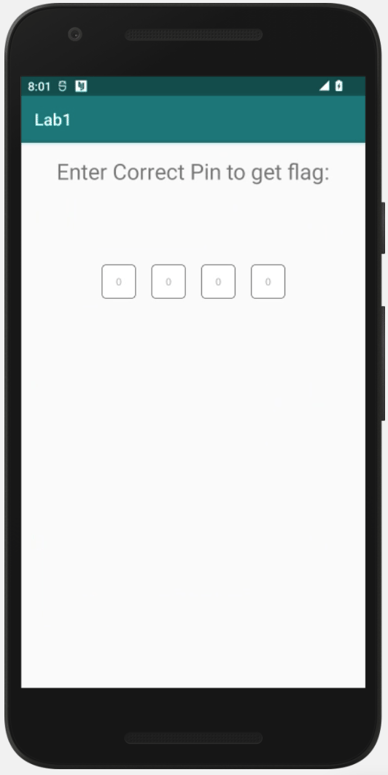
The application is looking for a 4-digit PIN. My first thought is to brute-force the pin because of the limited combinations it could be. When entering a pin to test, though, the application allows only three attempts and then requires time between guesses. All this means we should try to use Android reverse engineering tools to solve this.
Android Reverse Engineering with JADX
Above, we mentioned a couple of different reverse engineering tools. JADX leads the pack, allowing users to open an APK directly and decompile it into readable java code for analysis. Older tools like Dex2jar and JD-GUI work similarly but take a more extended approach.
We will start with using a JADX command to open the graphical interface, decompile the Android binary and allow us to perform more in-depth analysis.
jadx-gui com.cybergym.lab1.apk
On the left-hand side of the JADX application, you can see the APK file structure. We will start with the “MainActivity” to better understand the application and what is being done.
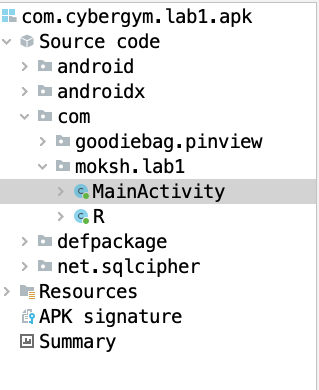
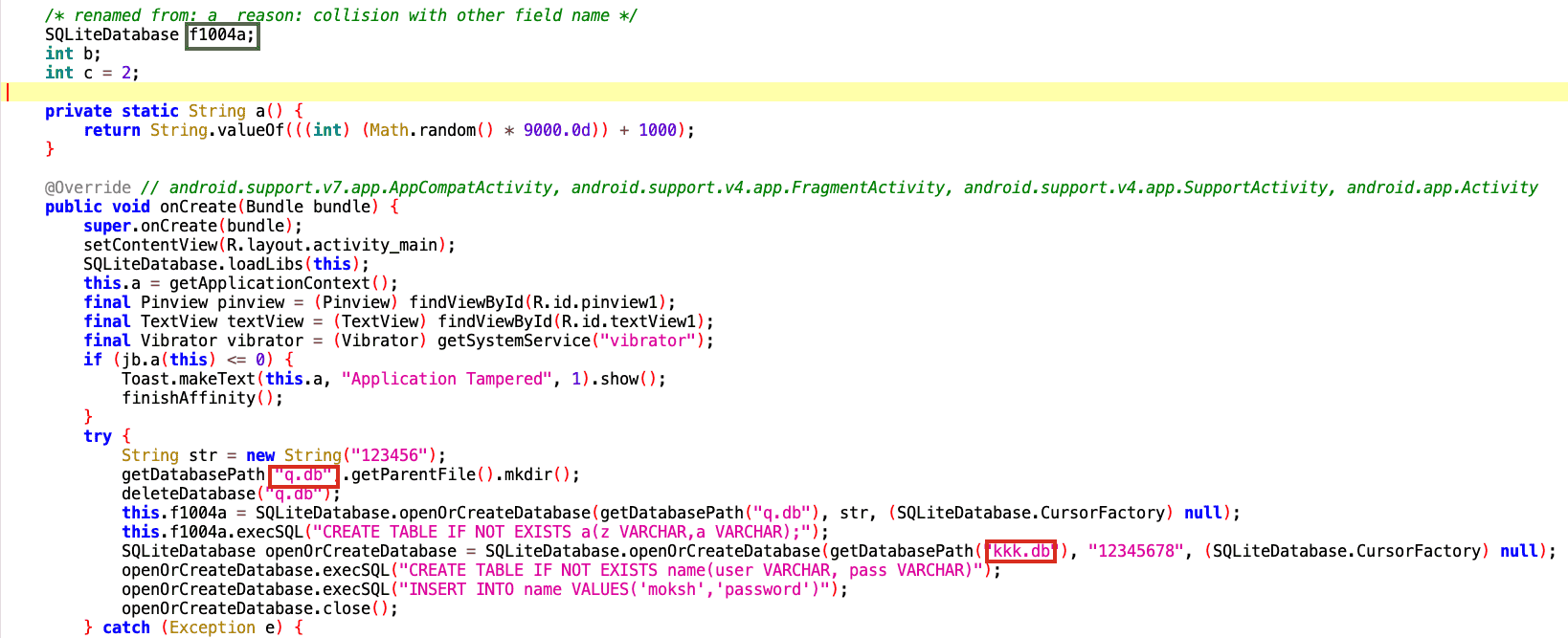
We notice some interesting things as we look into the MainActivity from this application.
- In the green box, you can see some obfuscation around the SQLite Database
- In the red boxes, you can see two database names getting created
- There is also a key of “12345678,” which will be interesting as we go through
Let's dig deeper into the code, starting with the kkk.db file.
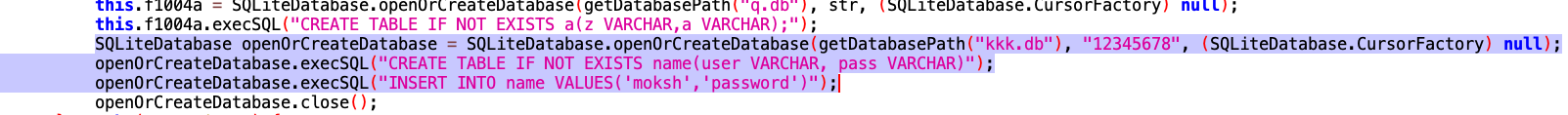
The highlighted code above creates a table with the name ‘name.’ Two columns are utilized within that table for ‘user’ and pass.’ Lastly, the values in those columns are ‘moksh’ and ‘password.’
Now let's look into the second DB and see what we can decipher:

As you can see in the above code, a table is created with the name ‘a’. Within that table, two columns are created: ‘z’ and ‘a’. The values being stored for ‘z’ and ‘a’ are random, which is generated by a random number function (see screenshot below).

We can understand what the application is doing from some quick reverse engineering and help us perform deeper analysis to solve this challenge.
We will now pull the application databases from the local Android files to see if we can identify some of the critical data that is being stored within these databases. Corellium makes it extremely easy to review local files and download them for analysis. For a full tutorial and explanation, check the blog post on local data stored for Android.

Now that we have the databases locally, we can open them up to see the contents. Once we do that, we are prompted with a password screen, meaning we must go back to the source code for additional analysis.
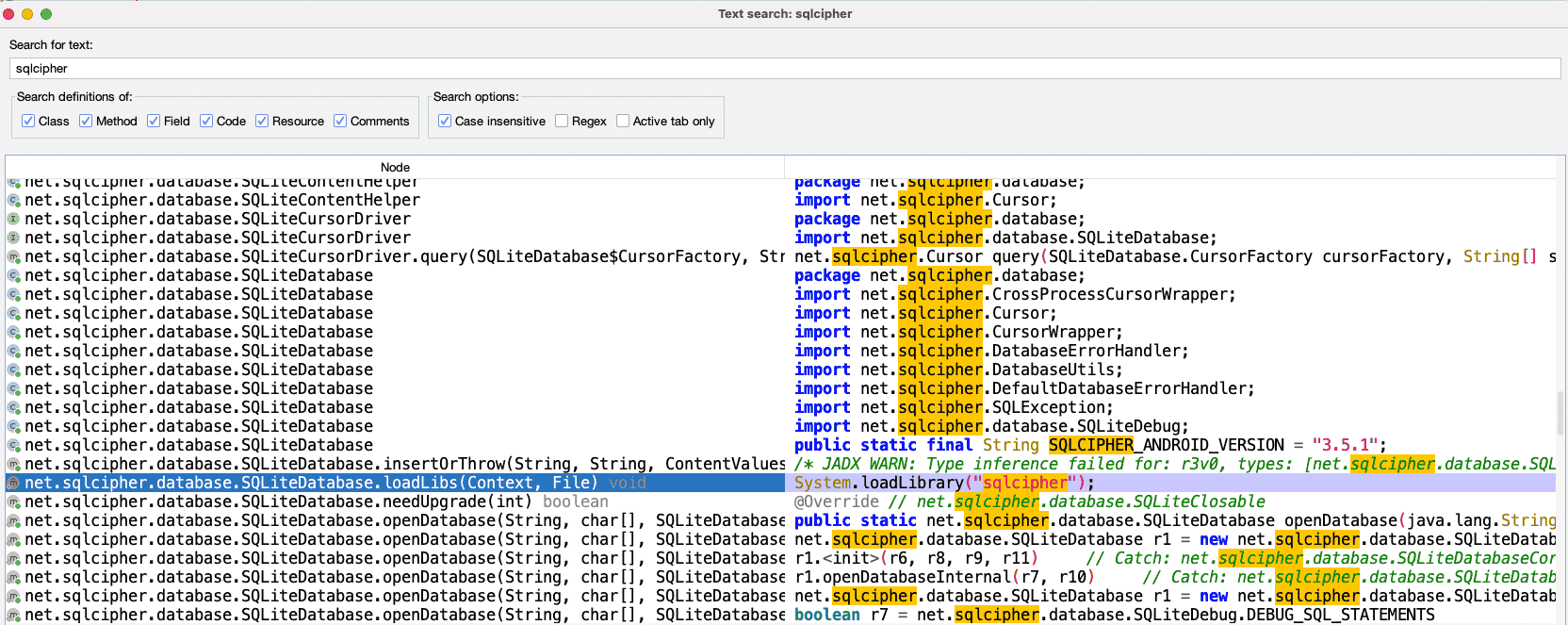
As I navigate through the code, I see many references to ‘sqlcipher,’ which is added encryption for SQLite databases. Using the advanced search functionality within JADX, I can find references to ‘sqlcipher’ to confirm that is what is being used for encryption.
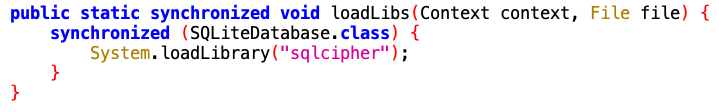
If you remember, initially, we found a key hardcoded in the ‘MainActivity’ early on in this activity, which turns out to be the PRAGMA key used for the database encryption.
To decrypt the database, we will need a command-line utility called ‘sqlcipher’. If you have a Mac, you can install it using the following command.
brew install sqlcipher
Once we have ‘sqlcipher’ installed, the databases available locally and the PRAGMA key, we are set to decrypt the contents and solve this challenge.
./sqlcipher q.db
>> PRAGMA Key = ‘123456’;
>> PRAGMA cipher_migrate;
>> SELECT * FROM a;
Using the above commands, you can load the encrypted database, enter the PRAGMA key, migrate the version (depending on your ‘sqlcipher’ version and then look at the results from the database.
This varies for everyone, but taking the results from the database and entering them in the challenge will give you the solution.
![Flag: cygym4[You_did_it_morty]](https://www.corellium.com/hs-fs/hubfs/Screen%20Shot%202023-01-01%20at%205.07.27%20PM.png?width=450&height=68&name=Screen%20Shot%202023-01-01%20at%205.07.27%20PM.png)
Reverse Engineer Android Apps with JADX and Advanced Tools
That shows some of the power behind tools like JADX for Android and the ability to take an APK file, perform analysis on it, and through investigations, continue to exploit and find additional vulnerabilities within an application.
Keep an eye out for future blog posts where we will dig deeper into code modification after reversing dynamic code changes using Frida and discuss how to leverage Corellium even more to speed up the process.
Unlock Superior Mobile Security Testing with Corellium
Equip your security teams with unprecedented tools for both manual and automated testing, freeing up valuable engineering time and saving money. Discover the power of Corellium’s high-fidelity virtual devices and spin-up near limitless combinations of device and OS with one-click jailbreak/root access. Set up a meeting today to see how we can streamline your processes and reduce costs.
Keep reading

Corellium Expands iOS 26 Testing with Risk Scoring and iPhone 17 Support

Apple's MIE Framework Makes Jailbreak-Dependent Testing Obsolete

