The Corellium Resource Library
The latest articles and news on mobile app security testing, IoT and research from Corellium and community contributors.
Brian Robison •
Jan 29, 2025
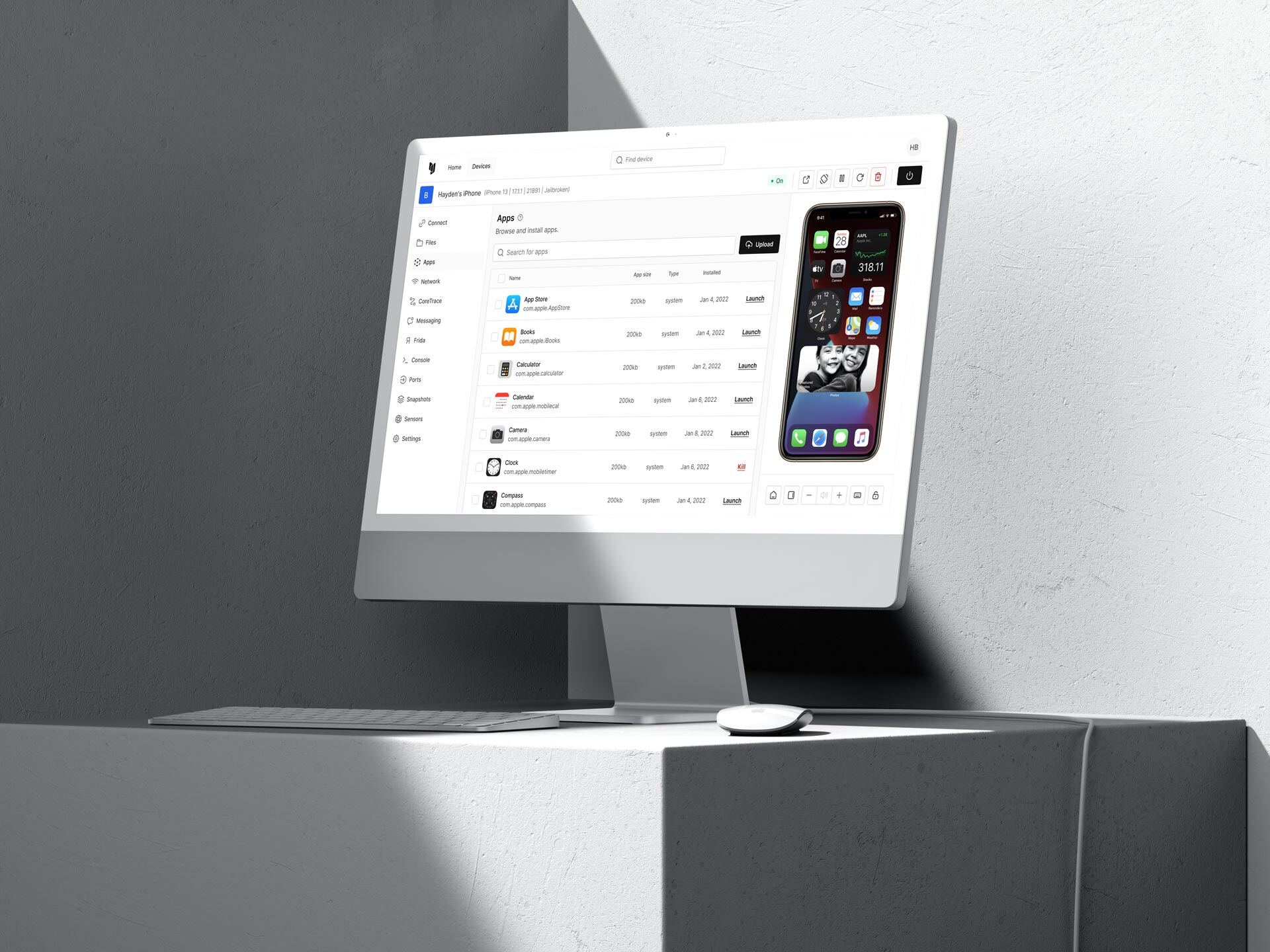
Corellium Virtual iOS Devices vs. Apple’s iOS Simulator and Physical Devices: The Ultimate Tool for Penetration Testing
Discover the advantages of Corellium’s virtual iOS devices for penetration testing. From instant access to jailbroken versions of any iOS release to the elimination of logistical challenges associated with physical devices, Corellium is revolutionizing mobile app security testing.

Brian Robison •
Jan 13, 2025
Wrestling the Mobile Security Hydra: Tackling Data Leaks, Zero-Days, and Jailbreak Challenges
Key takeaways from mobile security trends to strengthen your strategy—addressing data leaks, zero-days, and the challenges of disappearing public jailbreaks.

Brian Robison •
Nov 08, 2024
Complete Guide: The Ins and Outs of Automated Mobile Application Security Testing
Optimize your mobile app security testing with automation. Automate vulnerability assessments across Android & iOS to safeguard every release.

Brian Robison •
Oct 25, 2024
Potential Impact of iOS 18 and Apple Intelligence Features on Data Privacy
What developers in highly-regulated industries should consider.
Brian Robison •
Oct 16, 2024
Corellium Releases Support for iOS 18: A New Frontier for Mobile App Penetration Testers
The Corellium Virtual Hardware platform now supports iOS 18, including fully jailbroken iOS 18.

Brian Robison •
Jun 24, 2024
Mobile App Vulnerabilities Exposed: Getting Our Hands Dirty Part 2
Learn how to use the Corellium Café mobile app to uncover mobile app vulnerabilities in Corellium’s virtualized environment. Watch our webinar.
Brian Robison •
Oct 30, 2023
Mobile Malware and Threat Research Without Limits
In this article, we look at several types of mobile malware — of increasing sophistication — and discuss opportunities for research and analysis using virtual devices.

Brian Robison •
Sep 14, 2023
Deep Dive into Reverse Engineering on Android
Learn the tools and tactics needed to optimize your approach to Android reverse engineering. Watch our expert webinar or read the recap and case study.

Brian Robison •
Aug 02, 2023
Testing Third-Party iOS Apps: Why Independent Investigative Research Is Crucial
Testing third-party iOS apps helps you identify unknown vulnerabilities. Learn more about how Corellium can help revolutionize your AppSec testing.
Brian Robison •
Jun 27, 2023
Investigating iOS Phishing Using Virtualization Technology
By taking advantage of virtualization technology, security engineers can actively engage with iPhone phishing scams directly from a virtual iOS device. Here’s how.

Brian Robison •
Jun 09, 2023
Mastering Mobile Malware Detection: Essential Tools, Tactics, and Research Procedures
Discover how Corellium’s advanced mobile malware detection tools enable threat researchers to streamline testing, analyze threats & strengthen mobile security.
Brian Robison •
Jun 08, 2023
Mobile App Reverse Engineering: Tools, Tactics, and Procedures Unveiled
Learn about the tools, tactics, and procedures employed in reverse engineering iOS and Android apps, including an overview of the process and responsible practices.
Subscribe to Stay Connected
Keep up to date with emails for the latest product news and technical articles.
