Checking Suspicious Links in Corellium

Imagine being on vacation and receiving this SMS shortly before your flight home:

But you didn’t check in online… You’re not flying Southwest… And what’s up with that URL? We can inspect the link using an Android or a jailbroken iOS device, along with some of Corellium's built-in tools.
We’ll start by using the built-in Network Monitor. Using a virtual device with a proxy, such as Burp or Charles, will be covered in a later post.
You will need a virtual device. If you haven't already, check out our Quickstart for Android article.
Part 1: Start the Network Monitor
Before loading the browser, make sure you enable the Network Monitor to capture the traffic.
- Click “Network” to the right of your virtual device.
- Click “Start Monitoring.”
Captured HTTP and HTTPS traffic will appear in the Overview panel next to the device. Click on any of the captured packets to view more information, including the request and the response.
Part 2: Load the Suspicious URL
- Open the browser, type in the suspicious URL, and hit enter.
- The URL sends you to accounts.google.com, what’s going on?
- Let’s use the Network Monitor to investigate!
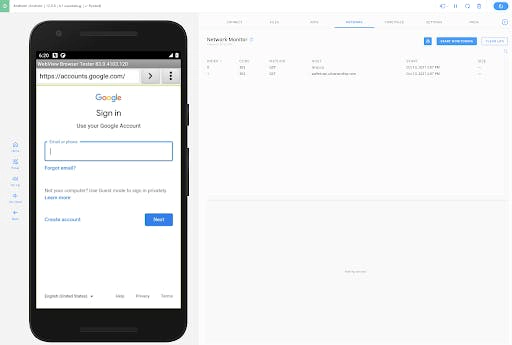
Part 3: Review Captured Packets
The Network Monitor captures two packets when loading the URL. (Note: starting the browser resulted in the Monitor capturing a handful of packets before we entered our URL. We cleared the log first to create the screenshot below.)

Entry #1 looks pretty interesting! Click on the packet to view the request.
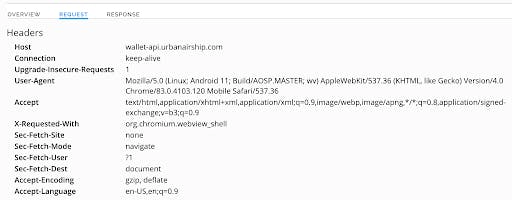
The request goes to “wallet-api.urbanairship.com” and takes us to a Google sign-in page. The response includes “pay.google.com”, which belongs to Google’s digital wallet platform.
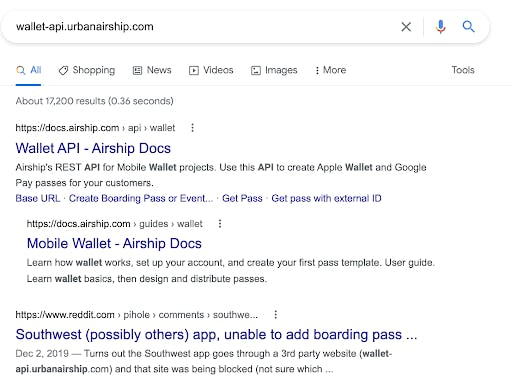
If we Google “wallet-api.urbanairship.com”, we find a link to Airship's Wallet API. There’s also a Reddit post stating Southwest Airlines uses a third party to deliver mobile boarding passes. And Airship confirmed on Twitter that the airsp.co link is legitimate.
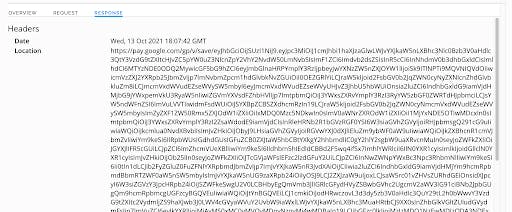
If we load the URL on a jailbroken iOS device (just to compare), Safari says it “cannot download this file.” Here’s the response:
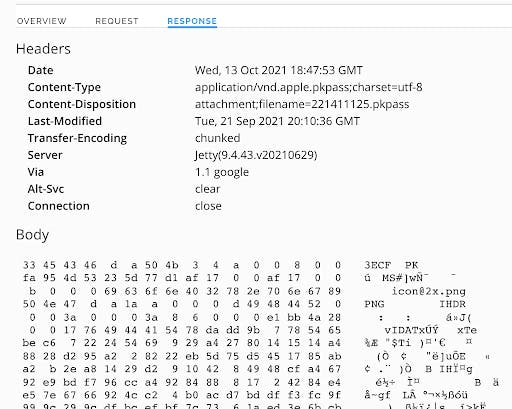
If we Google vnd.apple.pkpass, we find a link to Apple’s Wallet Developer Guide.
All these different breadcrumbs point to the SMS and link containing a legitimate Southwest boarding pass… It’s not ours, but probably the result of someone mistyping their phone number. At least it wasn’t something nefarious!
Note about Virtual iOS Devices
Certain applications, including Apple Wallet, aren’t supported on our virtual iOS devices. This is why Safari could not “download this file.” On a physical iOS device, clicking the link causes Apple Wallet to load the boarding pass.
Explore the power of safe link investigation with Corellium. Book a meeting now and learn how to enhance your app security efforts!
Advance Your Mobile Security Research with Corellium
Experience Corellium’s groundbreaking virtualization technology for mobile devices and discover never-before-possible mobile vulnerability and threat research for iOS and Android phones. Book a meeting today to explore how our platform can optimize mobile security research and malware analysis.
Keep reading
Corellium Unleashes Atlas, Redefines ARM Virtualization and Future of Software Defined Vehicles

Are You Wasting Two Thirds of Your Mobile Application Security Testing Efforts?

