Exploiting iOS local storage with Corellium

Storing data is essential to many mobile applications. What data is being stored? How is the data being stored? How is my data being protected? These are all great questions. In this blog post, we are going to demonstrate how to examine, detect and exploit sensitive information being stored in iOS app local storage. So, Let’s get this party started.
When it comes to an iOS device, the following are some common ways of storing data:
- Keychain
- NSUserDefaults
- iOS Application Databases
- Plist Files (Property Files)
We will use the intentionally vulnerable iOS application known as DVIA-2, which can be accessed here. Utilizing Corellium virtualized devices along with the DVIA-2 application. We will check frequent iOS local file storage locations and how easily that data can be compromised.
What Is iOS Keychain data storage
iOS Keychain is a repository for application data, passwords, keys and certificates. While keychain is used to store entries that iOS applications require, when misused can pose a great security risk. In an iOS device, these entries are kept in a local encrypted database. However, open-source tools that can dump the iOS keychain in plain text are now available. Objection (Runtime Mobile Exploration Toolkit) along with Keychain Dumper are excellent examples of how easy it can be to retrieve this data.
Keychain-Dumper is a great tool if you want to dump the entire device keychain, and I recommend taking a look at using it with your Corellium device in the future. For this blog post, we are going to focus more specifically on pulling keychain data from a specific running application (DVIA-2), in this case, Objection will be a quicker option.
From your virtual iOS Corellium device, install and launch the DVIA-2 application.
Navigate to the Local Data Storage menu and select Keychain:
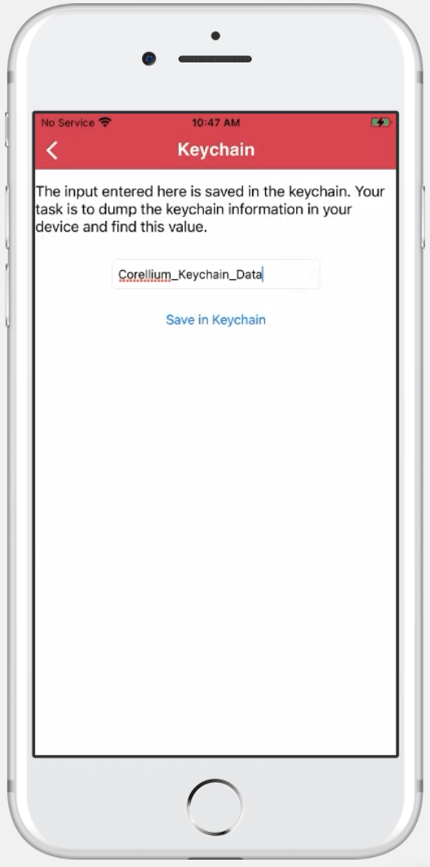
Once data has been saved in the application Keychain challenge, we will set up the environment to connect your local machine to the Corellium virtualized devices.
For the Cloud version of Corellium, ensure you have the VPN installed and running along with USBFlux to interact with the virtual device over USB.
In order to use Objection, you will need to know the package name of the application you are attempting to hook into. This can easily be retrieved within the Apps tab of the Corellium platform.

Once you have the package name of the target application, you can use the following command with Objection to hook the running process from your Corellium device.
objection -g com.highaltitudehacks.DVIAswiftv2 explore
When hooked into the running application (DVIA-2), you can use the following command to dump the keychain for the associated application:
ios keychain dump
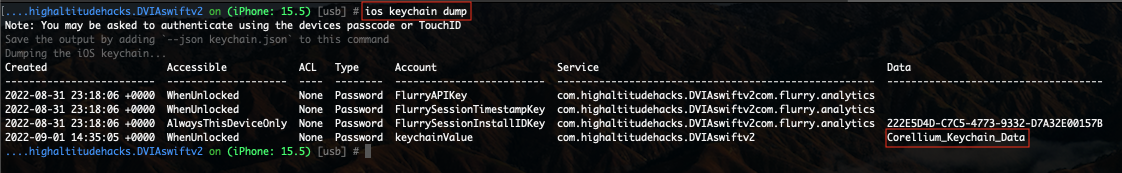
As we discussed at the beginning of this section, objection is used to dump the keychain items that are accessible only by the running application. This method is typically used in mobile pen testing activities. Keychain dumper is an alternative option if you want to dump the entire device keychain for analysis.
NSUserDefaults data storage
The iOS NSUserDefaults system allows an application to customize its behavior to match a user’s preferences. For example, an application can store a user’s preference of theme, unit of measurement, or general application customization. When used insecurely, NSUserDefaults can store sensitive data in plain text, making it easily accessible to attackers.
From your virtual iOS Corellium device, install and launch the DVIA-2 application.
Navigate to the Local Data Storage menu and select UserDefaults:
Fill in the required textbox and Save the data to the NSUserDefaults.
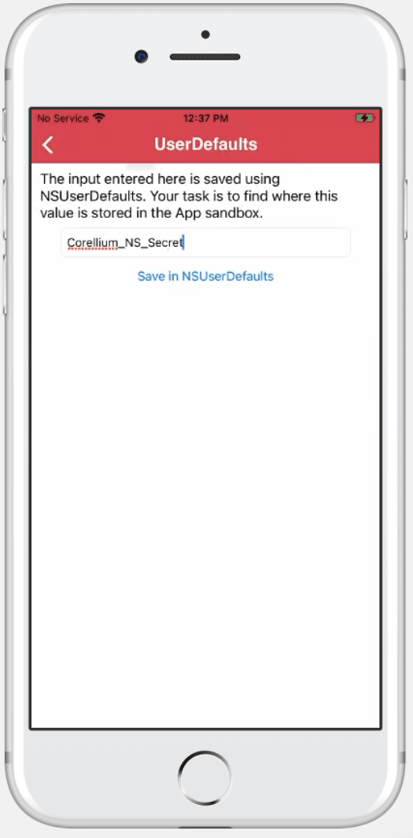
In order to pull the NSUserDefaults for an application, we will be once again using Objection. For detailed steps, see the process above.
objection -g com.highaltitudehacks.DVIAswiftv2 explore
When hooked into the running application (DVIA-2), you can use the following command to dump the NSUserDefaults:
ios nsuserdefaults get
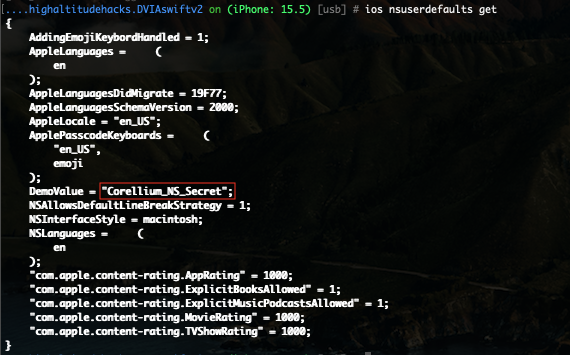
While the NSUserDefaults can be an excellent location to store preferences to enhance the user experience for an application, using it incorrectly to store potentially sensitive data can greatly increase the overall risk of your application and user data.
iOS application databases
iOS applications tend to store all sorts of data. This data typically ranges from public information to susceptible information. Every iOS application has its data directory, which by default, is only accessible by that same application. This is known as sandboxing.
With a jailbroken iOS device, the entire iOS filesystem is available to be accessed. The ability to access the root iOS file system poses a risk to applications that store sensitive data in plain text within their local data directories. Databases are one common way data is stored. Below using Corellium, we will show you how to access those databases and retrieve stored sensitive data easily.
There are two main ways to identify where the iOS data directory is for any given application. The first is by using Objection, as we have in the previous two steps, to check the application's paths.
objection -g com.highaltitudehacks.DVIAswiftv2 explore
Once you are hooked into the application, you can run the following command to show the environment paths
env
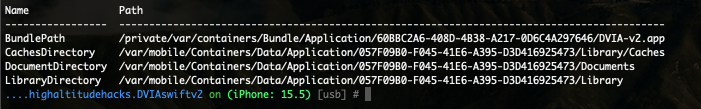
Alternatively, if you want to avoid using Objection to search for local databases, you can use the Files tab within the Corellium interface and navigate to the following directory:
/var/mobile/Containers/Data/Application/
Once you are here, there are unique IDs for every application. One way you can identify which ID is related to the application you want is based on the Last Modified column; using that date to match when you installed the application on the device can easily help identify which ID folder you require.
Now that we are in the applications data directory, we can look for Databases and search those for potentially sensitive information. This can involve searching manually through the files or searching for file extensions relating to databases (.sqlite, .sqlite3, .cblite2, .realm, etc).
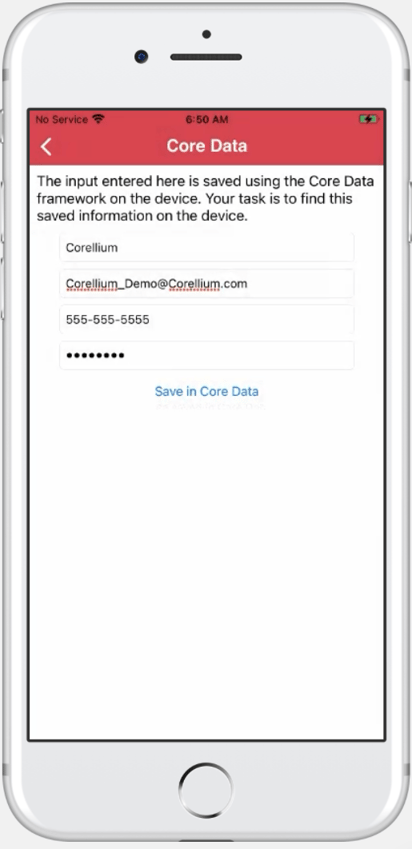
Navigate to the Local Data Storage menu within the DVIA-2 application and select Core Data.
Fill in the required textboxes and Save the data to a local database.
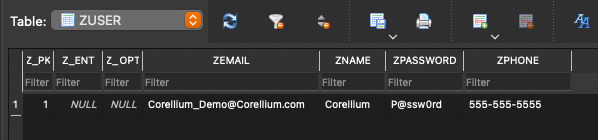
The saved Core Data database is within the application's data directory under the following path.
<Application ID>/Library/Application Support/
From the Corellium interface, you can easily download that file to view on your local machine, either using a DB viewer or command line operations.
iOS property list files
iOS applications contain property files (PLIST) both within the application bundle (IPA) and, in some cases, within the applications data directory. PLIST files contain various settings, configurations and properties for the given application. In some cases, they can also contain data stored by the application similar to the database above.
From your virtual iOS Corellium device, install and launch the DVIA-2 application.
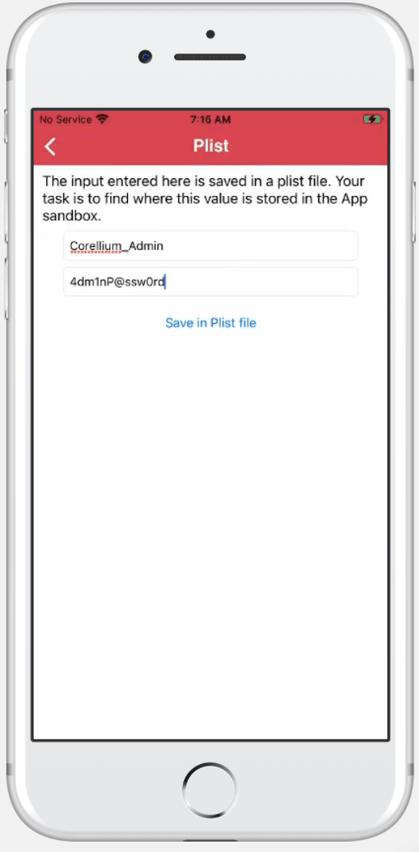
Navigate to the Local Data Storage menu and select PLIST.
Fill in the required textbox and Save the data to a local PLIST file.
Once you have filled in the information within the challenge screen you can navigate back to the application data directory as we did in the last step and then into the Library directory.
/var/mobile/Containers/Data/Application/<Application ID>/Library
Remember, if you don’t know the ID to get into the specific application, you can use the Last Modified date column within Corellium or use Objection as we did above to identify that ID.
Within this directory you will see a userinfo.plist file that can be downloaded from the Corellium platform and then reviewed on your local machine.
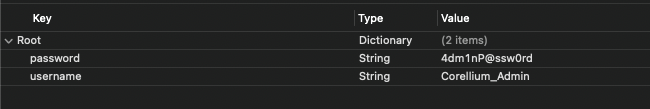
While a PLIST file is especially an XML file, it can be difficult to read with your standard text editor. There are a couple of additional options to read these files if you are having difficulty easily.
- Xcode – If you have a Mac, Xcode by default can open and read PLIST files
- Plutil and plistbuddy – These are built-in tools on Mac for not only reading PLIST files but modifying them if required
- Objection – As we used above on multiple occasions, Objection has a command to read PLIST files; see below for the command
ios plist cat <userInfo.plist>
Unlock Superior Mobile Security Testing with Corellium
Equip your security teams with unprecedented tools for both manual and automated testing, freeing up valuable engineering time and saving money. Discover the power of Corellium’s high-fidelity virtual devices and spin-up near limitless combinations of device and OS with one-click jailbreak/root access. Book a meeting today to see how we can streamline your processes and reduce costs.
Keep reading

Corellium Introduces Unparalleled Support for iOS 26 and Newest Mobile Device Models, Dynamic Risk Scoring for Mobile Applications, and Expanded Global Coverage

Apple's MIE Framework Makes Jailbreak-Dependent Testing Obsolete

