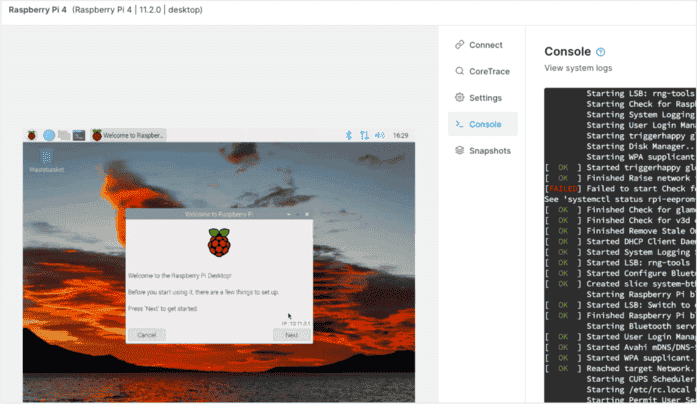
IoT Device DevOps
Revolutionize the development of your IoT embedded software and companion mobile apps by integrating virtual devices into your SDLC. Say goodbye to restrictive device farms or slow and inadequate emulators.
We run on Arm, others don’t
We pioneered the CHARM hypervisor for Arm device virtualization.
Smart device R&D is full of challenges
IoT devices are powered by Arm processors. You can’t run and test IoT firmware on a laptop and maintaining device labs is costly.
- Devices get broken, lost, and bricked.
- Batteries are not made to run constantly, posing a safety risk.
- Inefficient to ship for remote work.
- Difficult to attach tools and automate, complicating testing and security work.
- Hardware is needed before software work can begin; delays the time to market while teams wait.

Virtualize IoT devices & companion mobile apps
Corellium accelerates software development lifecycles with Arm-native virtual models and powerful tools and APIs.
- Easily spin-up endless combinations of device models and firmware versions.
- A single platform for both IoT device software and mobile app development and testing.
- Integrate with your existing developer, security, and IoT DevOps tools.
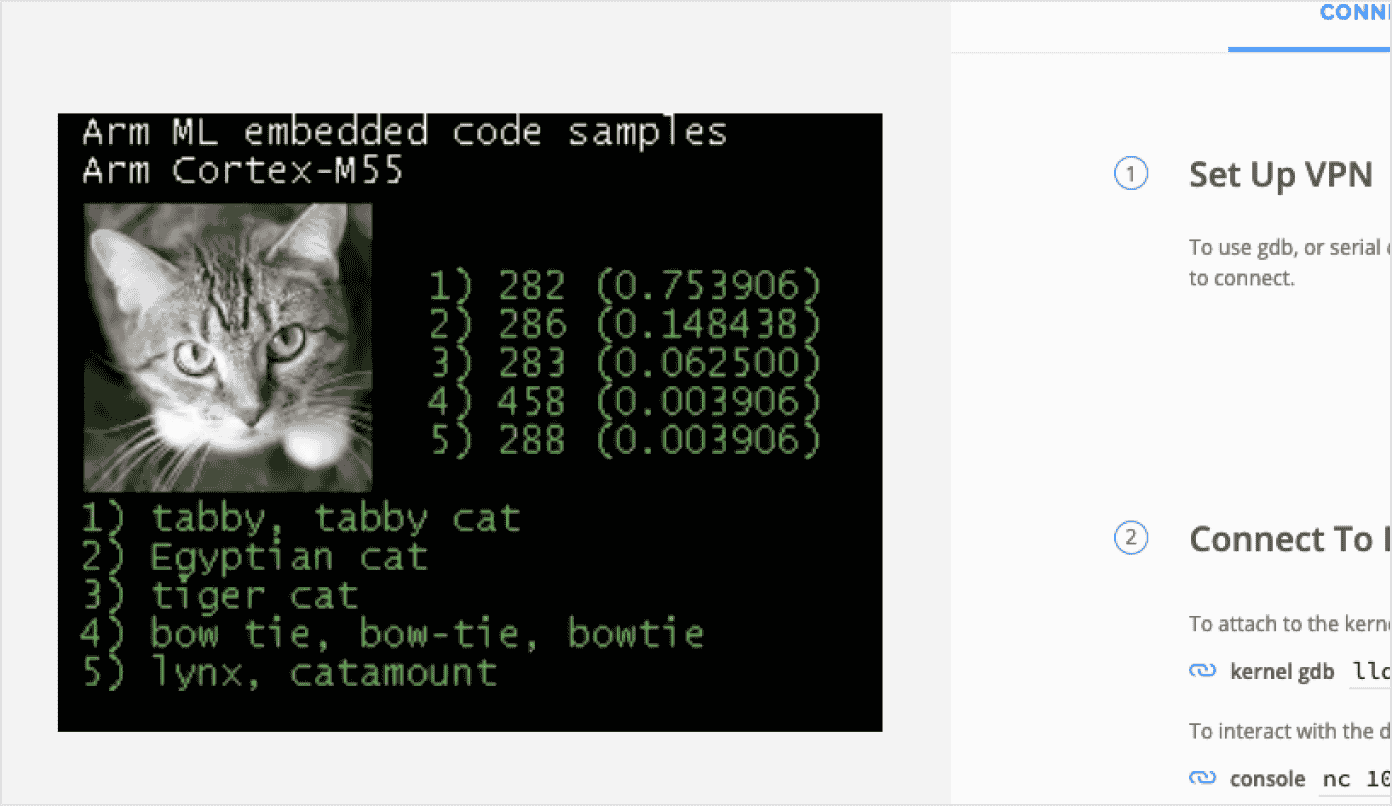
Ditch device labs and emulators
Stop asking your customers and app developers to manage endless physical device and OS version combinations.
- Replace costly, incomplete, and undependable physical device labs or cloud farms.
- Achieve Arm-native performance, accuracy and device behavior that emulators can’t. Virtualized IoT devices often run much faster than the physical devices they represent!
- Run production code and eliminate code modifications and recompiles.
- Enable testing with the kind of scale that only the cloud can offer.
Streamline DevOps to accelerate software R&D
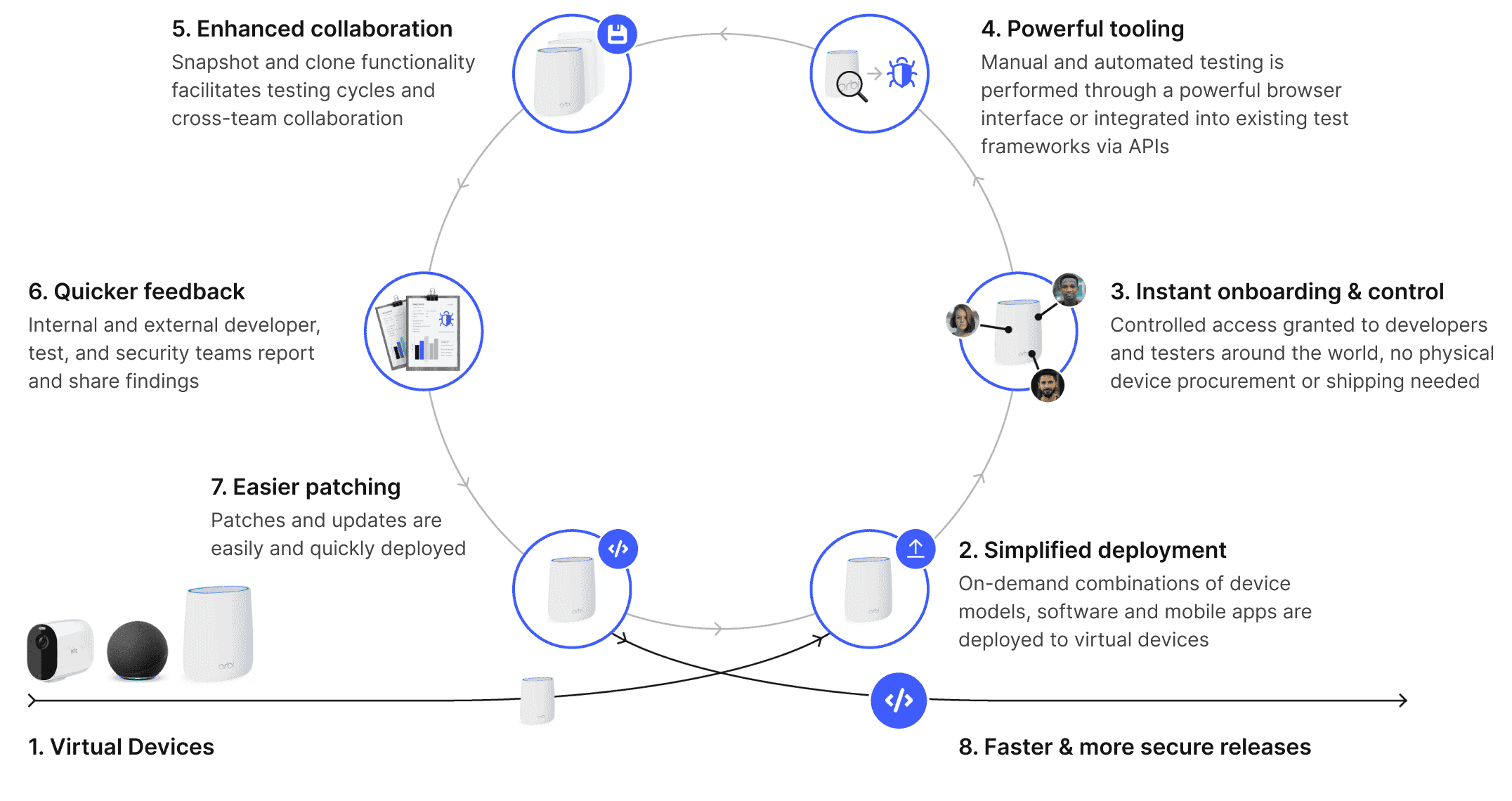
Create virtual device models
Our extensive library includes hundreds of peripherals and support for nearly every Arm processor. A virtualized model of your Arm device may be easier than you'd think.
-
Virtualization for most Cortex A, R and M processors
-
Peripheral and sensor models for most popular interfaces and integration needs
-
Ability to incorporate existing models for non-Arm processors and compute elements
- Experienced modeling team to add new models or create and customize devices