The Corellium Resource Library
The latest articles and news on mobile app security testing, IoT and research from Corellium and community contributors.

David Backer •
Feb 29, 2024
MediaPipe Computer Vision on Arm Virtual Hardware
How to download and run several ML examples and run them on the virtual Raspberry Pi 4b board available from Arm Virtual Hardware (AVH).

David Manouchehri •
Feb 09, 2024
Corellium with AI
Automate Complex Tasks by Giving GPT-4 Control over Corellium’s API.
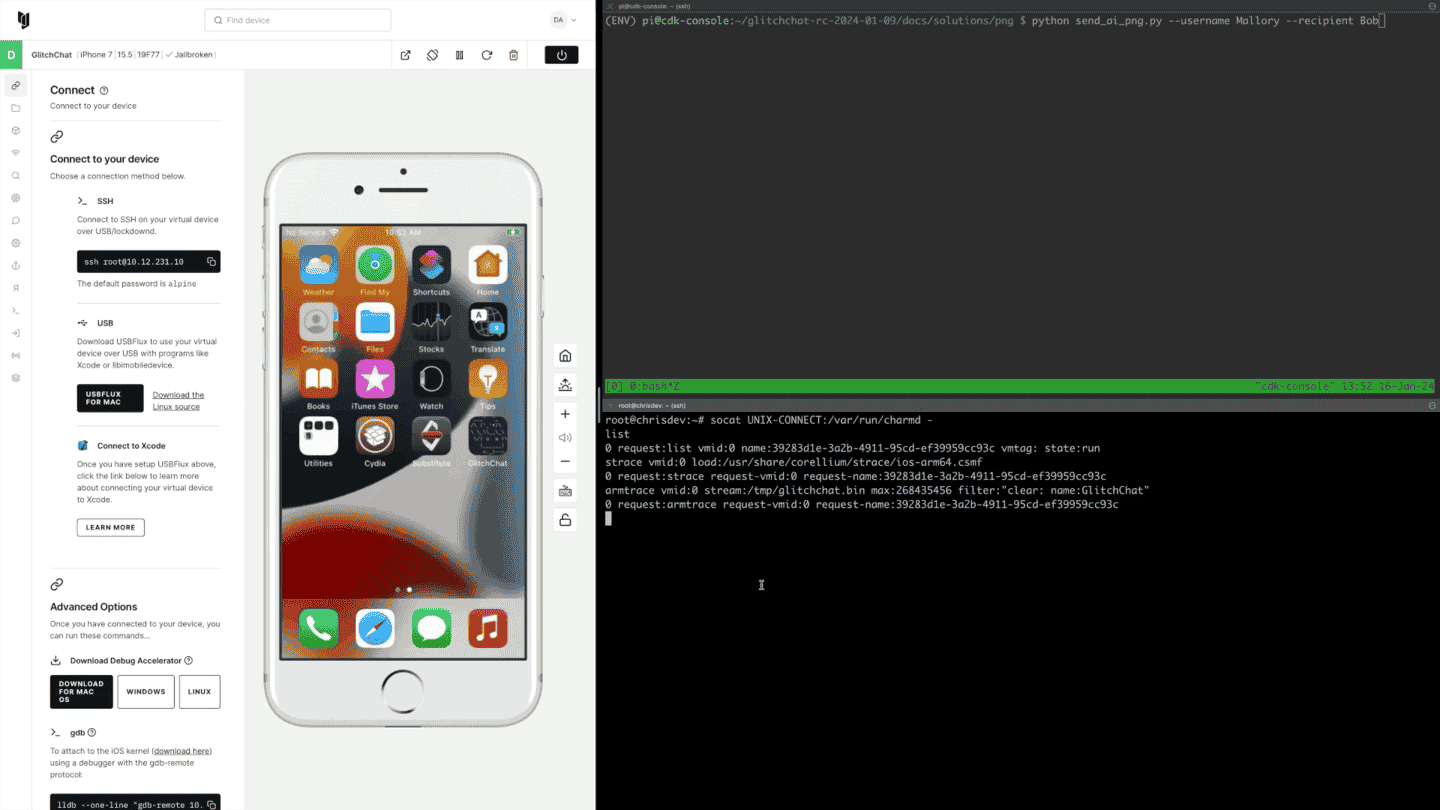
Chris Williams •
Feb 05, 2024
Corellium CoreSight Tracing Demo
Join Corellium for a CoreSight Tracing demo. Explore capabilities that provide insightful analysis on program flow/coverage, system calls, and more for user space processes.
Andrew Sooy •
Feb 02, 2024
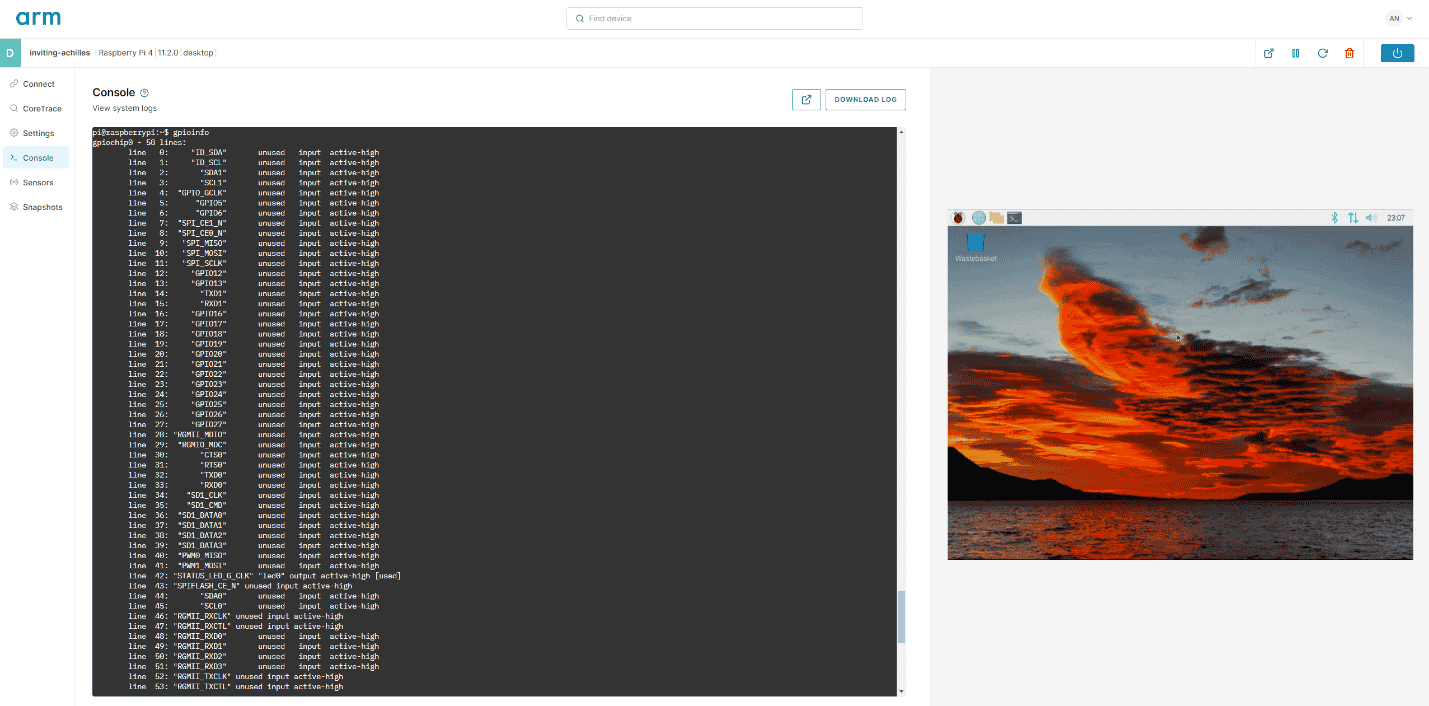
CoreModel GPIO and you!
This technical article will guide you through setting up a virtual RPI4B with gpiod and CoreModel to monitor and interact with its GPIO controller via a virtual device with buttons and an LED.
Dan Thagard •
Dec 20, 2023
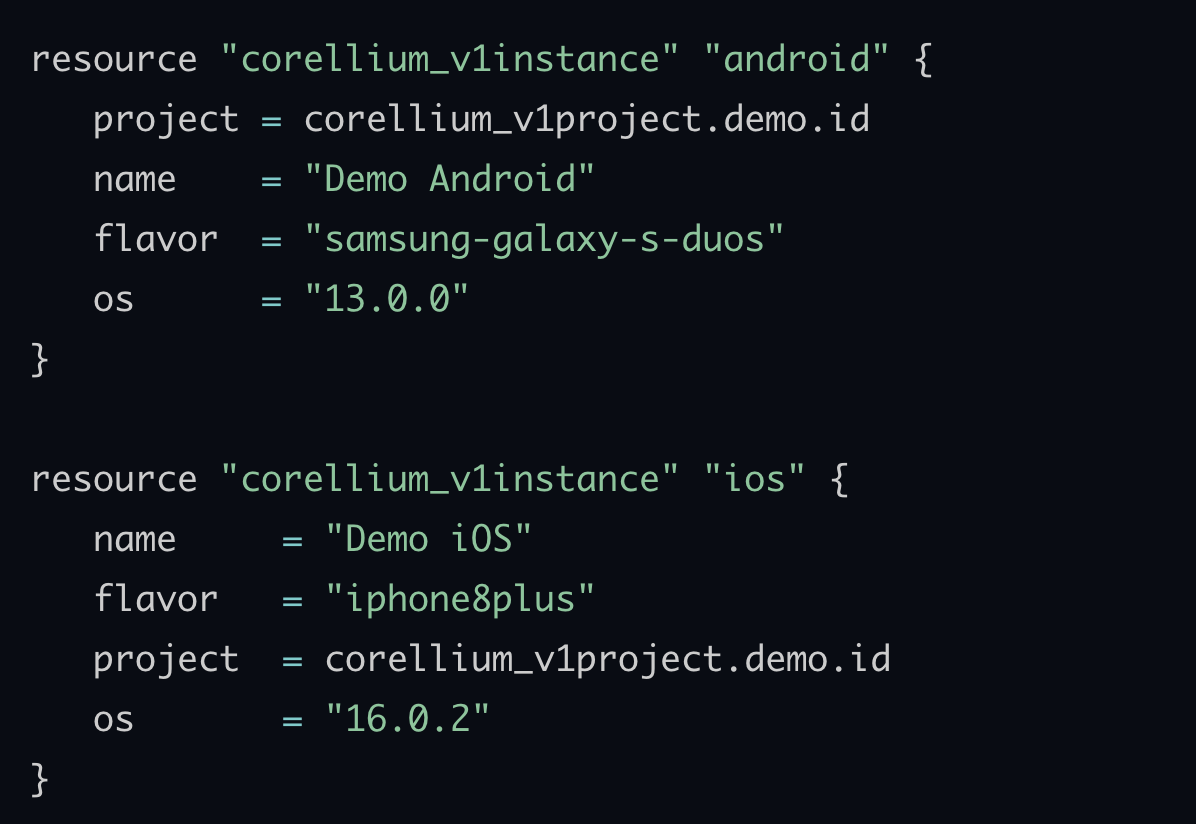
Understanding Terraform and Corellium: A Perfect Match for Virtual Device Management
Discover how combining Corellium with the power and flexibility of Terraform can streamline virtual device management for development and testing teams.

Corellium •
Dec 14, 2023
Introduction to IoT Custom Device Modeling for Embedded Developers and Security Teams
Transform your app development strategy with accurate device modeling. Explore the features of the CHARM Developer Kit in Corellium’s latest webinar.
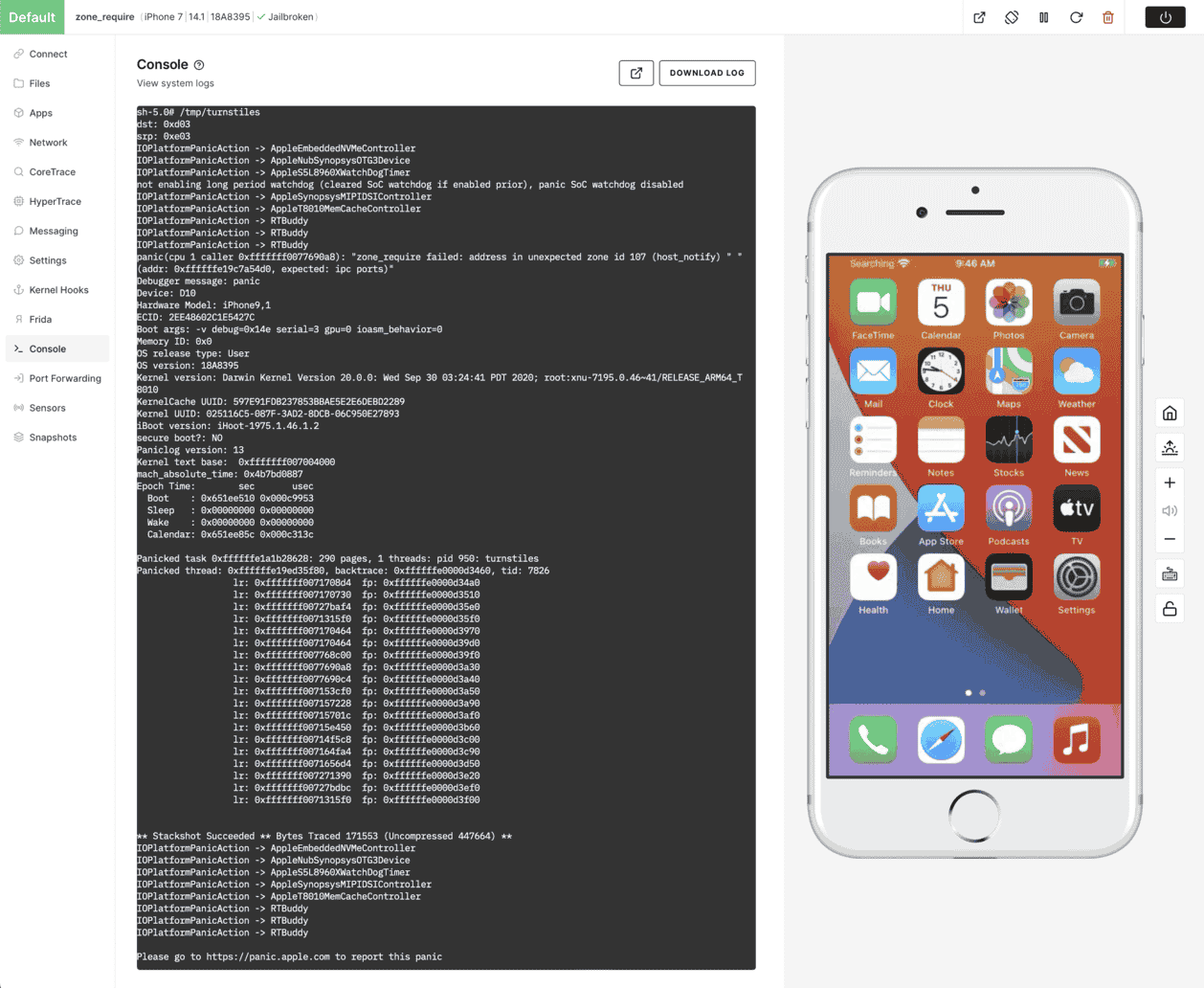
Chris Williams •
Nov 06, 2023
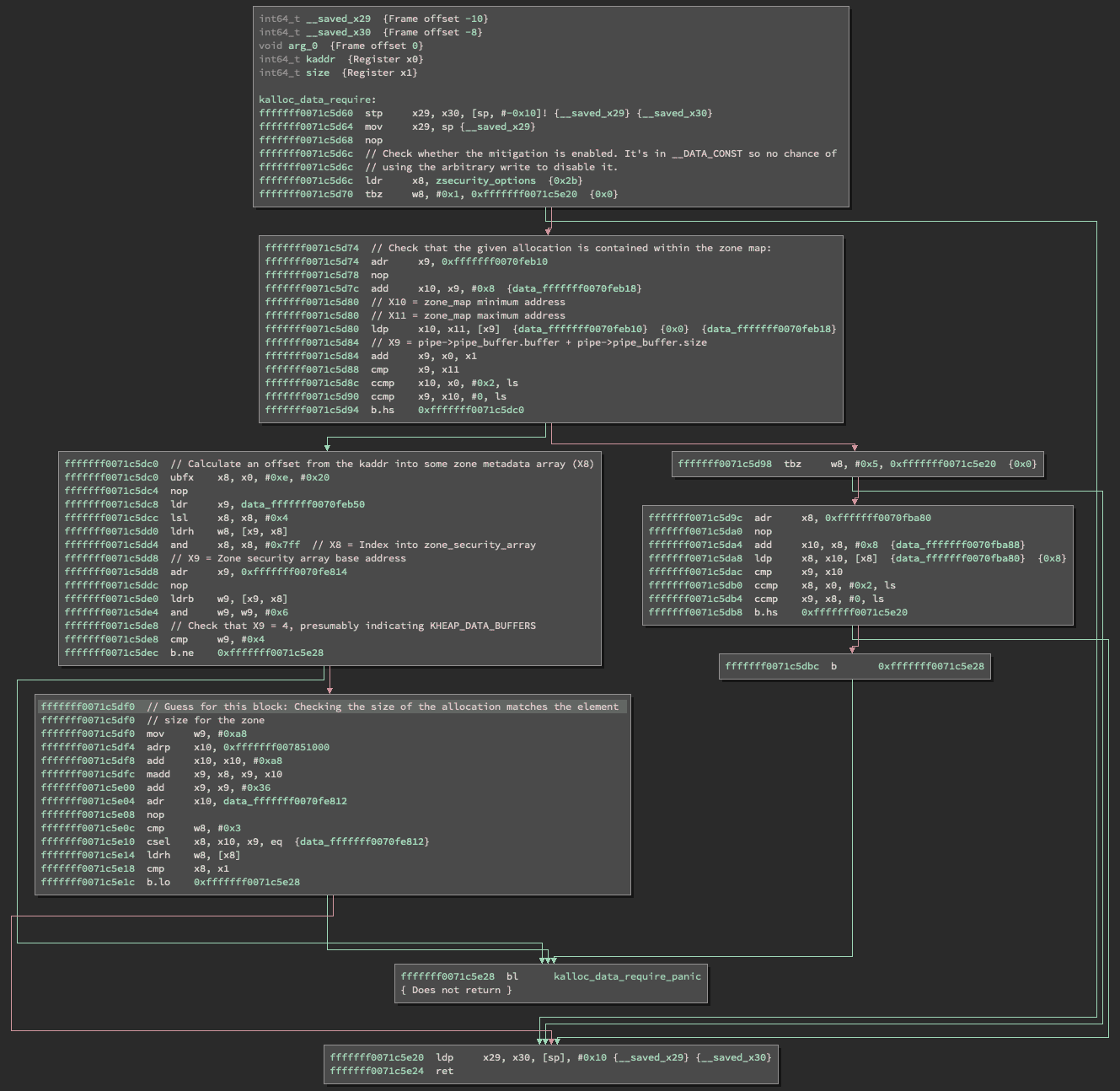
Using Corellium Kernel Hooks to Disable Exploit Mitigations
In this technical article, we'll take a look at a vulnerability in XNU, the kernel used by iOS and macOS, and explore how Corellium kernel hooks can help to disable exploit mitigations.
Chris Williams •
Nov 06, 2023
Exploring UNIX pipes for iOS kernel exploit primitives
Explore the use of UNIX pipes for iOS kernel exploit primitives in this insightful technical article. Learn how Corellium's magic can be used to practice and develop exploits without relying on vulnerabilities.

Corellium •
Nov 01, 2023
iOS Reverse Engineering Tactics and Techniques in Practice
Dive into iOS reverse engineering tools and techniques with experts from Corellium. Discover techniques, live demonstrations, and insights for mobile app security.
Brian Robison •
Oct 30, 2023
Mobile Malware and Threat Research Without Limits
In this article, we look at several types of mobile malware — of increasing sophistication — and discuss opportunities for research and analysis using virtual devices.

Amanda Gorton •
Oct 04, 2023
Corellium support for iOS 17
Supporting mobile security testing and research in a world without jailbreaks.

Brian Robison •
Sep 14, 2023
Deep Dive into Reverse Engineering on Android
Learn the tools and tactics needed to optimize your approach to Android reverse engineering. Watch our expert webinar or read the recap and case study.
Subscribe to Stay Connected
Keep up to date with emails for the latest product news and technical articles.
