Corellium Café
iOS Scenario Guide
Mobile App Pen Testing with Corellium and Corellium Café
Many mobile security pen testers enjoy using Corellium to perform mobile app pen testing. Corellium offers access to virtualized iOS device models from iPhone 6 up to the latest iPhone models, every iOS version ever supported on each model and instant access to jailbroken or non-jailbroken versions.
Corellium not only offers access to these devices and operating systems, but also has many built-in tools that make pen testing quicker and easier than traditional physical techniques.
Virtual device models can easily replace physical devices in many types of security testing and research. Combined with the efficiencies of virtualization - such as quickly creating new devices and powering them up, to snapshotting and nearly instantly restoring to a known good state - Corellium can drastically cut the effort currently spent in obtaining and managing physical devices.
Corellium is also a multi user platform, allowing users from around the world to collaborate on testing projects all through a web interface rather than shipping physical devices.
Overview
During the course of this guide, you will utilize your knowledge of pen testing techniques to find the many vulnerabilities designed into the Corellium Café mobile app.
This guide is broken into multiple sections. You will be challenged to find local storage, network, misconfiguration and runtime vulnerabilities.
Each section will introduce you to the concept and possibly give a hint, but you will use your knowledge and Corellium to uncover them. You will use built-in Corellium features as well as your own local tools to perform each task.
Tools Used or Required
To accomplish all the challenges, you will be required to have a few tools at your disposal. Some are included with Corellium and some are running locally on your computer. The tools below are suggestions, you may also use functional equivalents. For Corellium included tools, you can alternatively use your own if you wish.
Local Tools
Objection - https://github.com/sensepost/objection
Apple Xcode
Burp Suite - https://portswigger.net/burp - Can be used as an alternative to Corellium's Network Monitor (but NOT required for this guide)
DB Browser for SQLite (or other SQLite viewer) - https://sqlitebrowser.org/
Corellium Included Features/Tools
Network Monitor
Frida
File Browser
App Installer
Serial Console
VPN and USBFlux
Step 1: Creating Your First Virtual iOS Device
You can use an existing Corellium account, or you can request a new trial. After requesting a trial from Corellium, you should have received several emails providing you instructions on how to access the platform.
***IMPORTANT***
Your trial has a LIMITED number of "device hours" included. Keep in mind that when your device is powered on (or paused) the device hours timer is running. If you need to step away from your trial for any extended period of time (~20-30 minutes or more) you should POWER OFF the virtual iPhone to save your device hours.
1) Begin by logging into the Corellium platform using the credentials you created during your trial setup.

2) After logging in click on the Create Device, if you are already a Corellium customer, feel free to skip down to the beginning testing section.
3) Corellium Trials offer limited device runtime (hours) as well as a limited number of cores (for devices). Running a modern iPhone (like the iPhone 14 Pro) consumes 6 CPU cores and may limit your trial, especially if you want to test multiple devices and/or platforms. For this reason, this trial guide uses an older iPhone 7 as it only consumes 2 CPU cores.
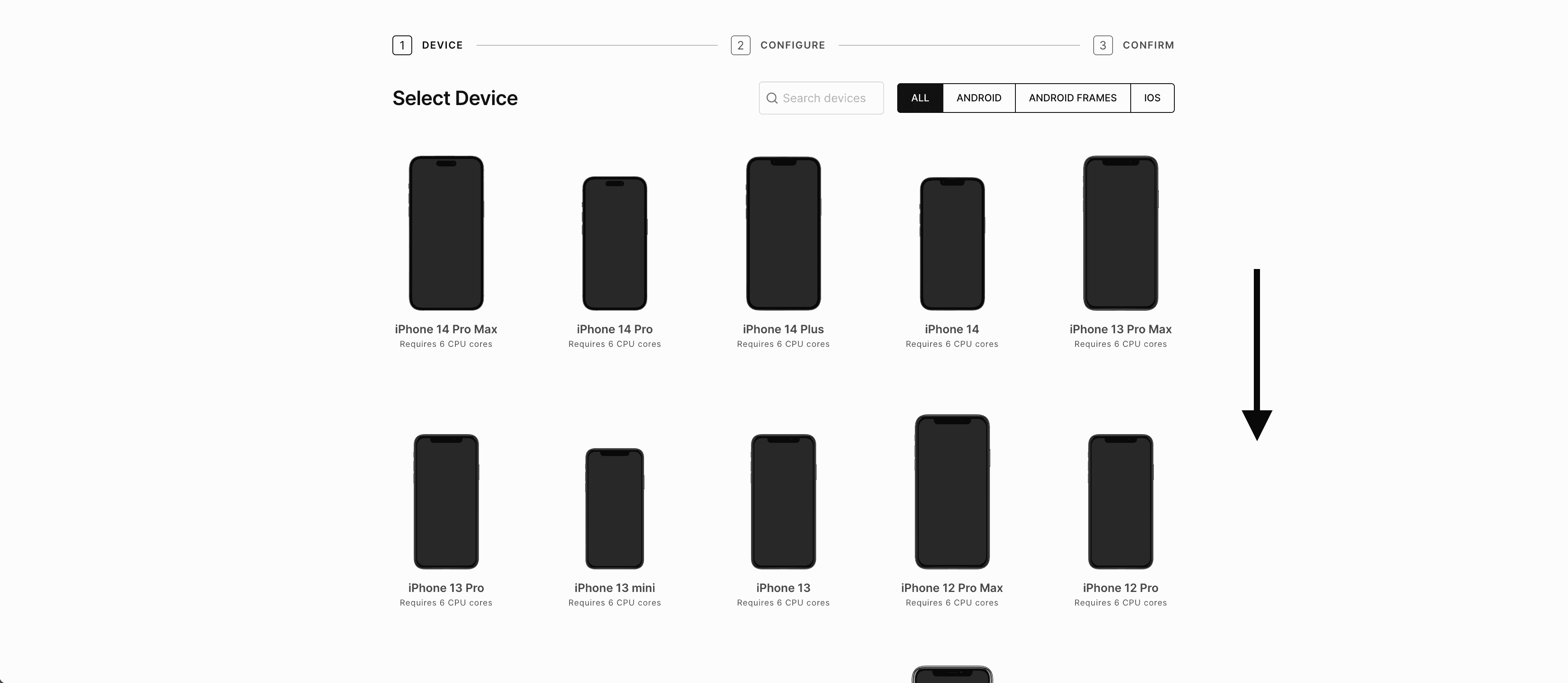
For this scenario, scroll down and choose an iPhone 7 (you are free to choose a different device, however, this guide uses an iPhone 7).

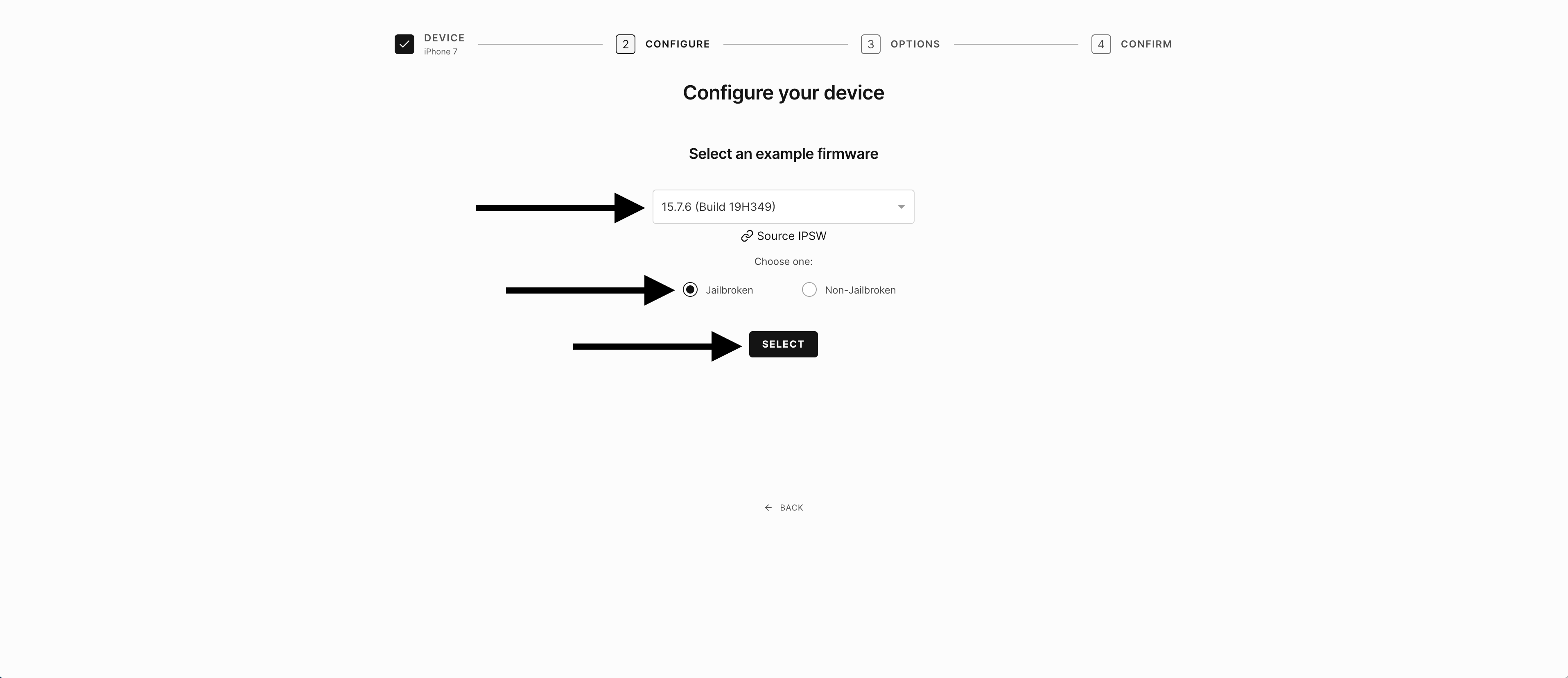
4) Select the version of iOS you wish to test and make sure that jailbroken is chosen - then click on Select.
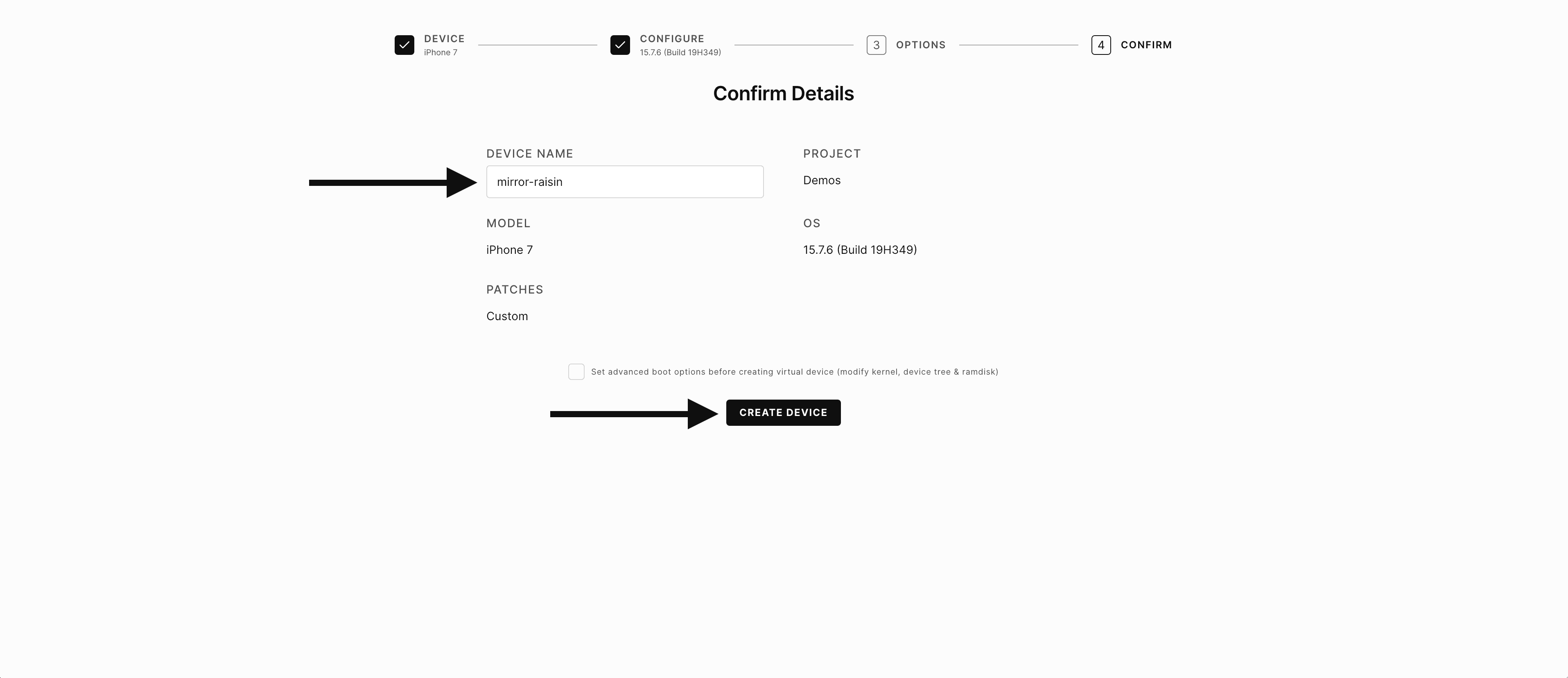
5) Confirm the choices and name the device (any name you wish) or accept the randomly created name and click Create Device.
6) The device will now be created in Corellium by downloading the chose IPSW directly from Apple, the virtual model will be built and the IPSW will be restored to the device in a process that is very similar to a real device. This step can take 10-15 minutes initially. Feel free to watch the debug log as the device powers on and performs it's restore.
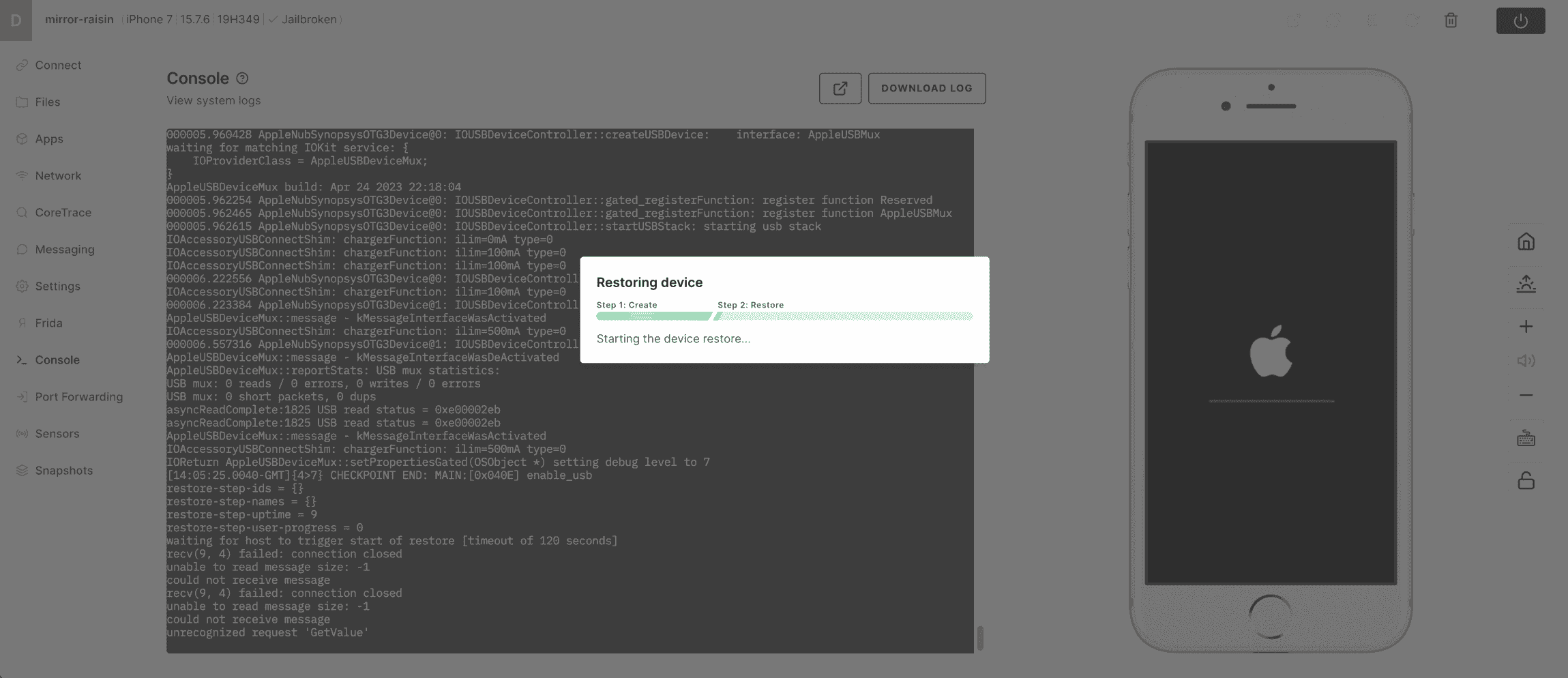
7) You have now successfully created your first virtual device!
Taking your First Snapshot
Before you begin to make changes to your device (like installing software or tools), it is a good idea to create a snapshot of the virtual phone. This will allow you to restore back to a perfectly clean device at any time without rebuilding from scratch. Feel free to take snapshots throughout your trial use if you wish.
1) Click on the Snapshots tool in the tool bar.
2) Click Take New Snapshot - virtual iOS devices can be snapshot while powered on (items in memory are restored as is). This process will take a few minutes. Alternatively, you can power-off your device and take a snapshot.

3) Give your snapshot a meaningful name. Click on the generic name (auto created) to edit.
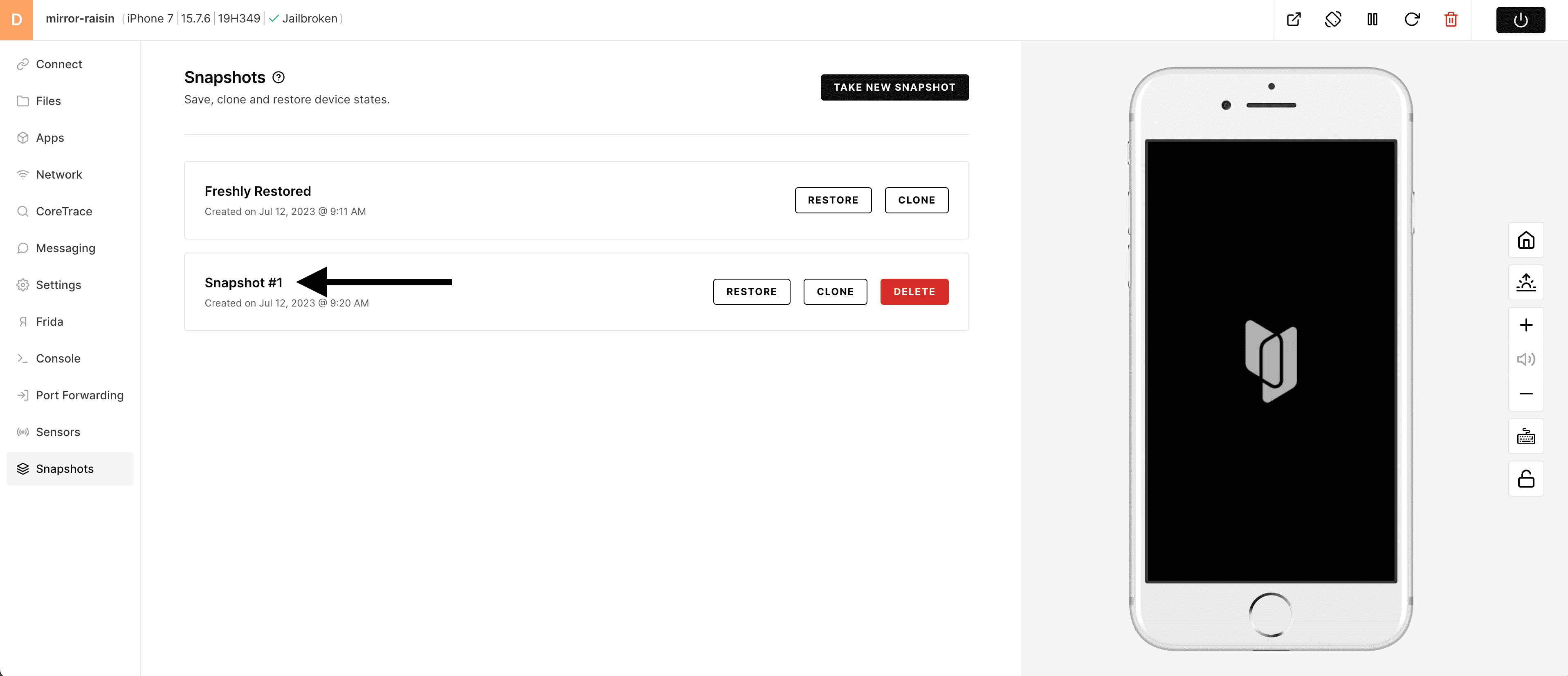
4) Type the desired name and press enter/return - if you "click" outside the name, it will revert back to the auto generated name.
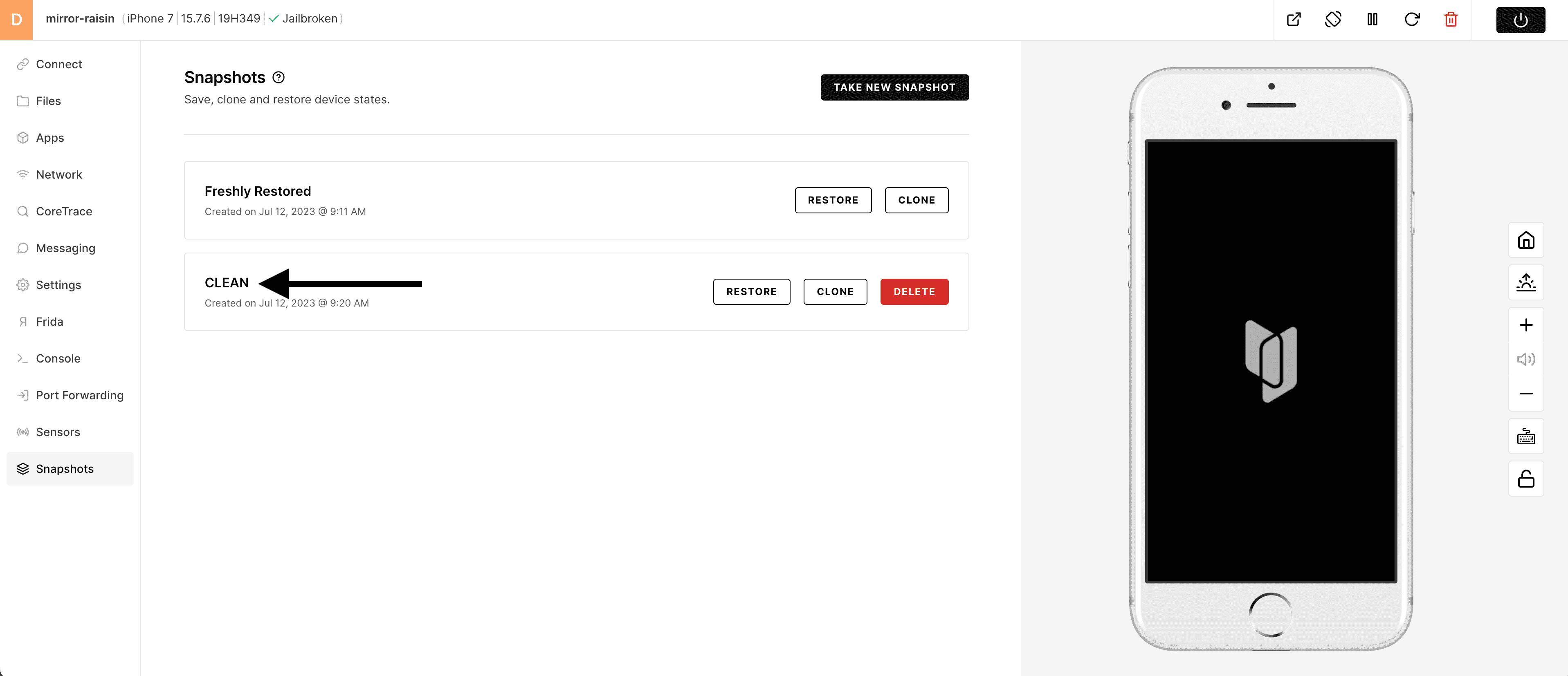
5) You've now successfully taken your first snapshot - you can come back here and restore the device to this state at any time.
Step 2: Downloading Corellium Café
While the virtual device is being built and restored, you need to download a copy of Corellium Café so that you can install it on the device you just created.
This is also a great time to explore the .ipa package locally on your machine and begin examining the contents of app with tools like IDA Pro or Hopper.
Download the latest Corellium Café mobile app using this link.
Step 3: Installing Corellium Café
Corellium includes a built-in side-loading tool that make installing mobile apps very easy. No developer mobile profiles or anything is required to use the side-loader.
1) After your device has finished building, restoring and you've taken your first snapshot - you can begin using it just as you would a real device. You can either click the Home button at the bottom or click the Unlock button.
2) Once the device is unlocked, you can swipe the springboard (use the mouse, press and drag to simulate your finger). When you are ready to install Corellium Café, choose the Apps tool in the tool selector on the left.
3) To install Corellium Café (or other .ipa file), choose the Install App button.
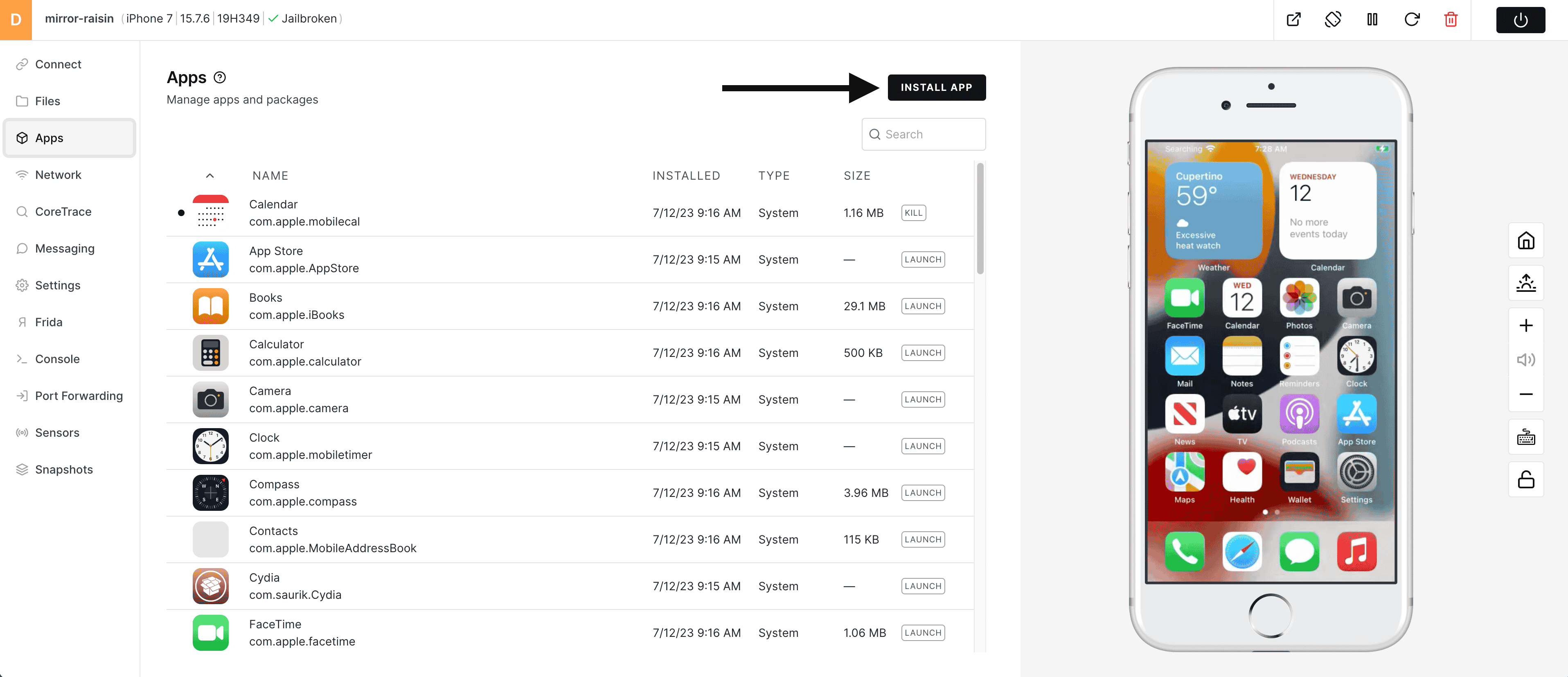
4) Choose the Corellium Café .ipa file you downloaded above.
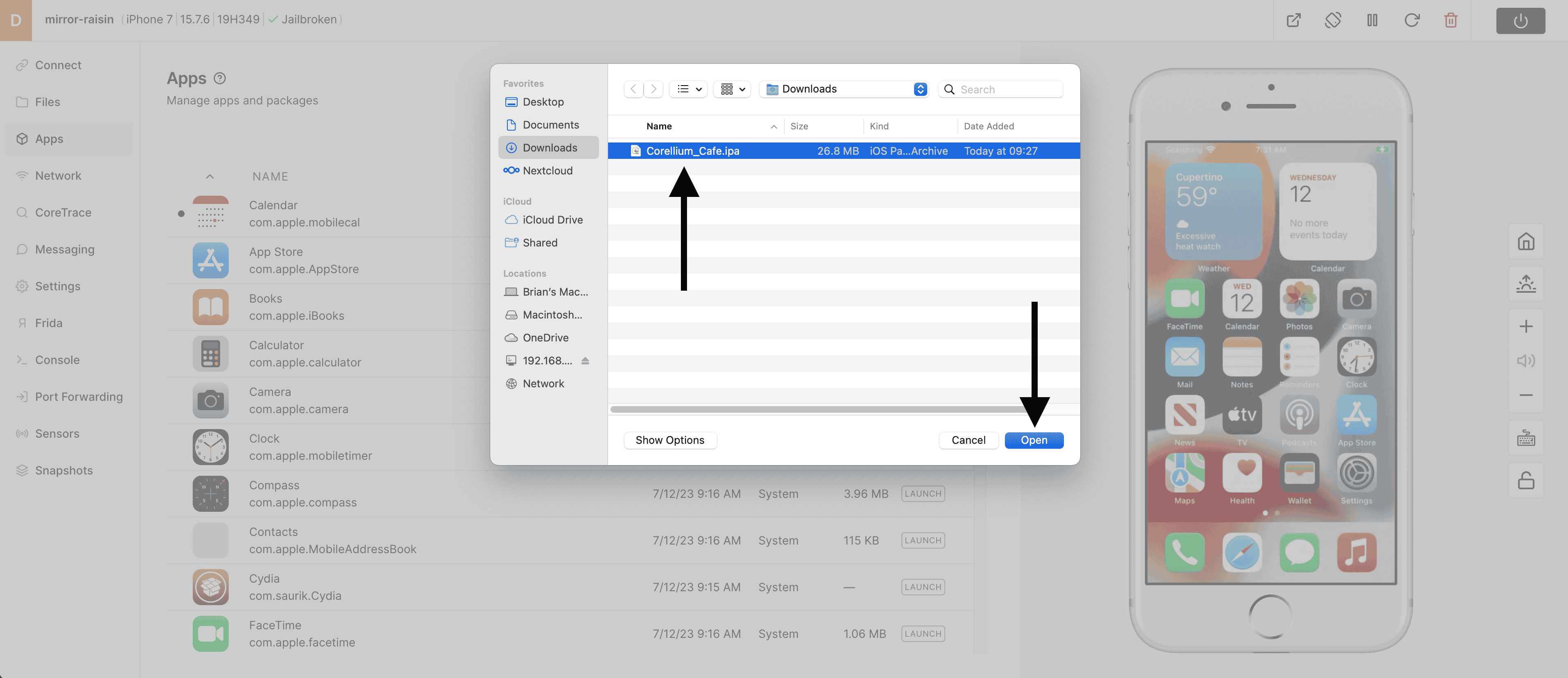
5) Corellium Café has been successfully installed on the device. You may now begin your pen testing!
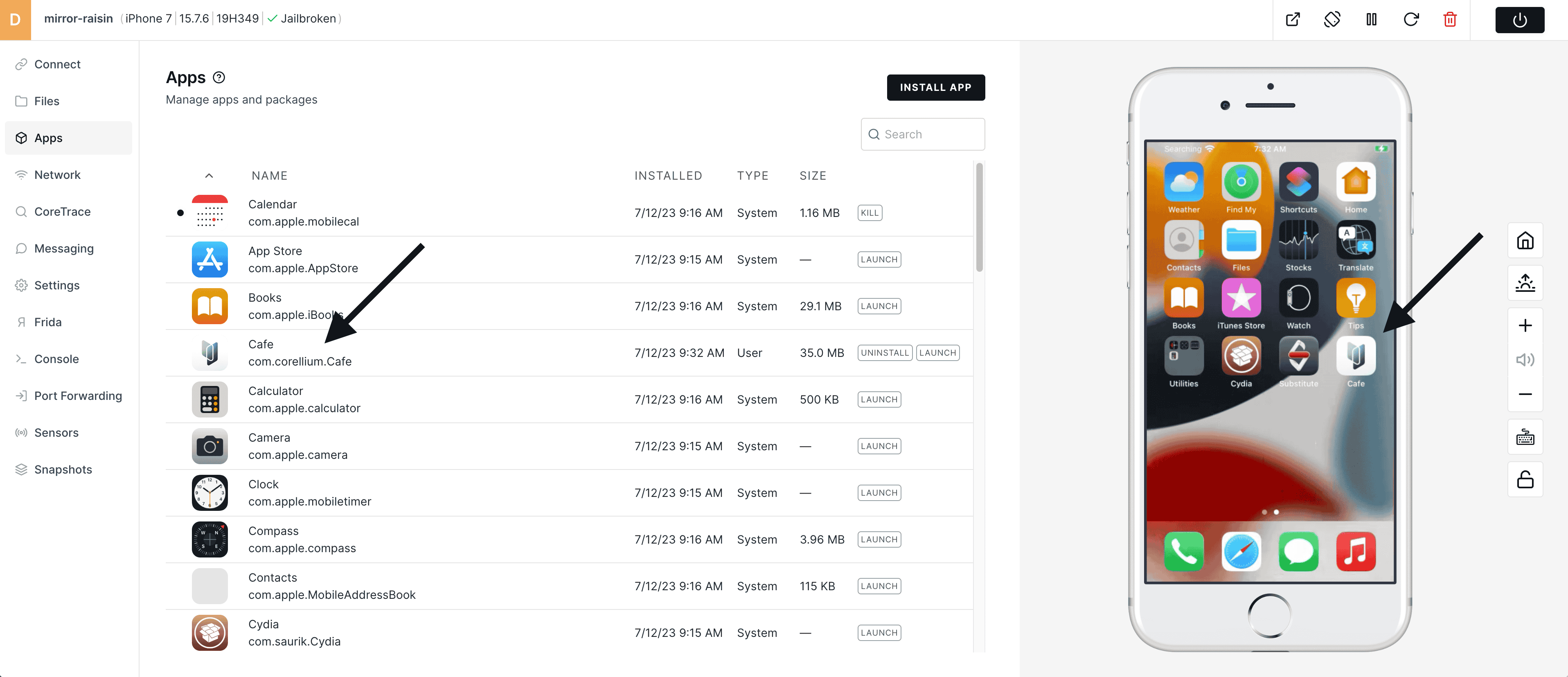
6) Now might be a good time to take another snapshot (if you wish) with the Corellium Café freshly installed, but has not been run yet - meaning its data container is completely clean.
If you would like to read more information about installing mobile apps visit the Apps section of our Support Center.
Step 4: Connecting to Your Virtual iPhone
As you perform app pen testing with Corellium, you may choose (or need) to use locally installed tools. Many of these tools, such as Xcode and Objection, require a physical USB connection to the iPhone. Other tools like Burp Suite require network connectivity.
If you are a Corellium customer and have one of our on-premises appliances, you can skip this section. This section only applies for customers or trial users who are utilizing the Corellium cloud solution.
Corellium offers the ability to connect to the virtual devices via network and physical USB. Connecting to the VPN is required to allow the virtual iPhone to communicate with your local computer as well as using the virtual USB connection.
Connecting to VPN
The VPN is an OpenVPN compliant connection. There are many OVPN clients you can use depending on your platform. For detailed steps to install/configure for MacOS, Windows and Linux visit our VPN topics on our Support Center.
This guide is going to walk through using TunnelBlick on MacOS. If you have a different OVPN client, you may have to view that documention for instructions on installing the .ovpn profile.
1) Click on the Connect tool in the tool bar on the left.
2) Download the OVPN file and install it into your OpenVPN (or compatible) local client.
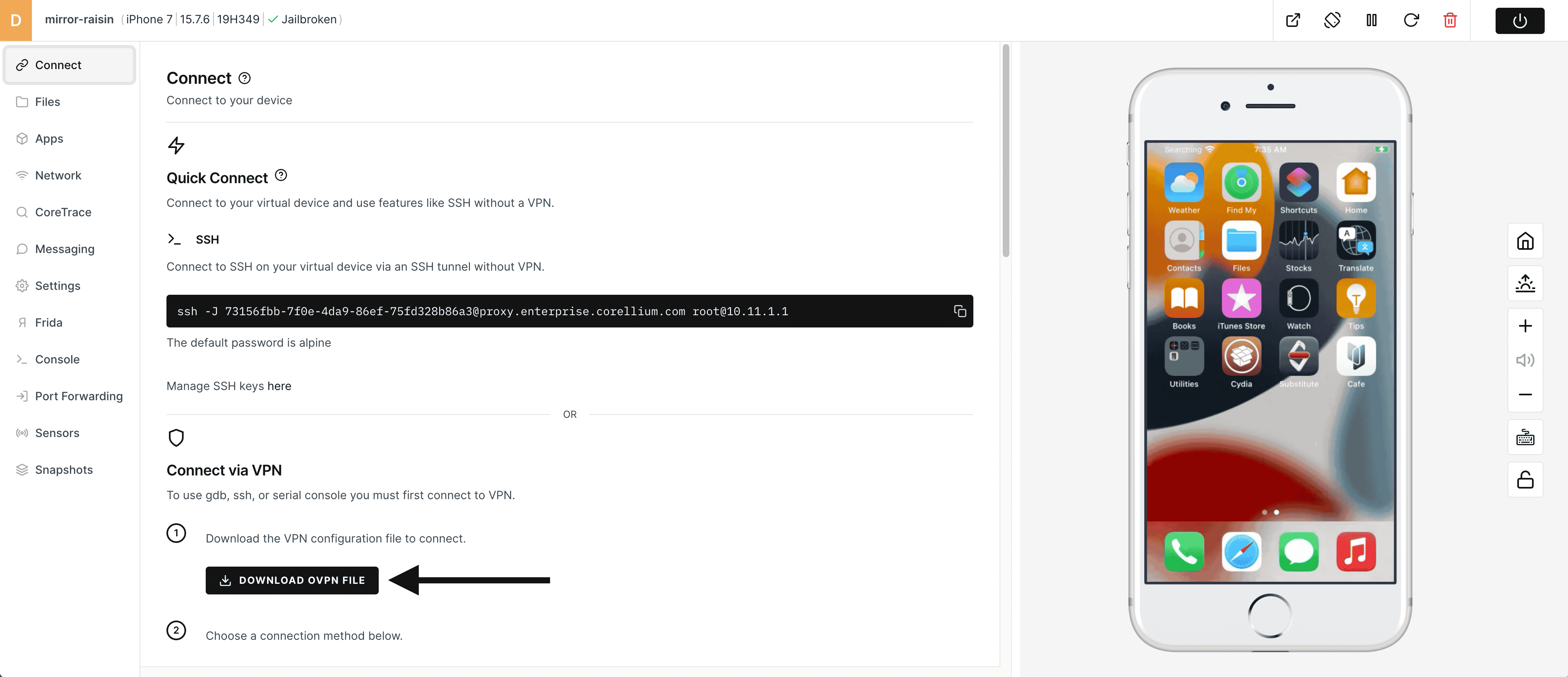
3) Our Support Center has instructions on setting up the VPN for multiple types of clients as well as operating systems. Please follow those guides if you don't already have an OpenVPN client installed.
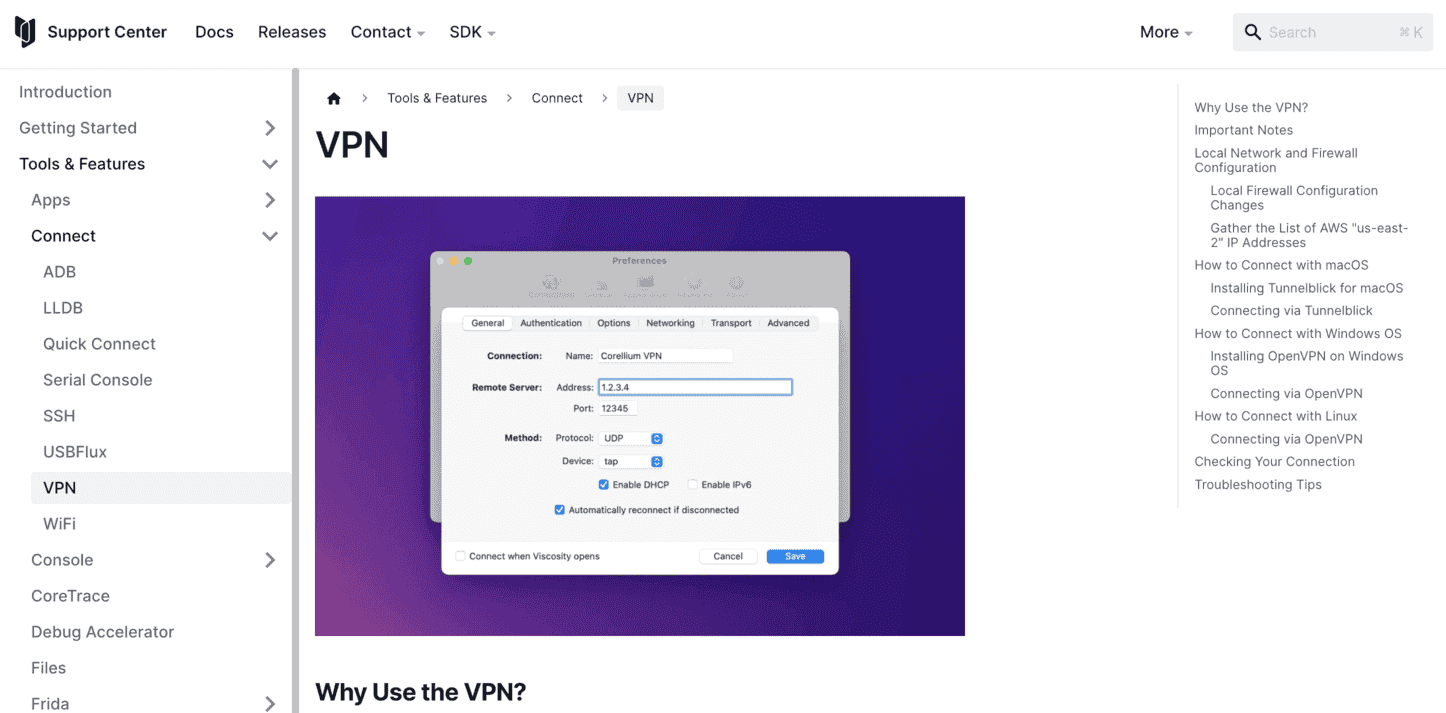
4) After you've installed your VPN client, connect to the VPN (TunnelBlick on MacOS is used in this example)


Test the VPN Connectivity
1) On the Connect tool page, scroll down to get the IP address of the virtual iPhone.
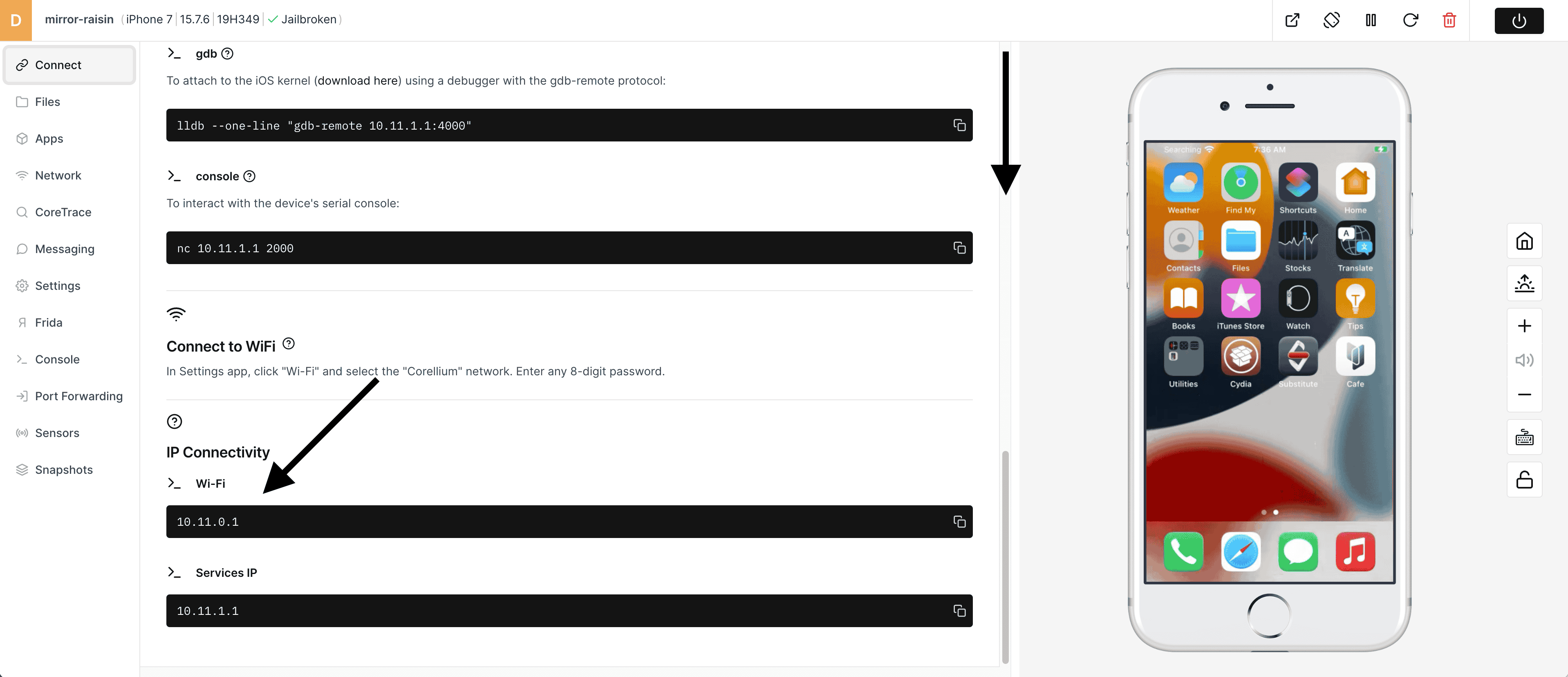
2) Open a Terminal shell and ping the IP address of the iPhone to verify network connectivity.
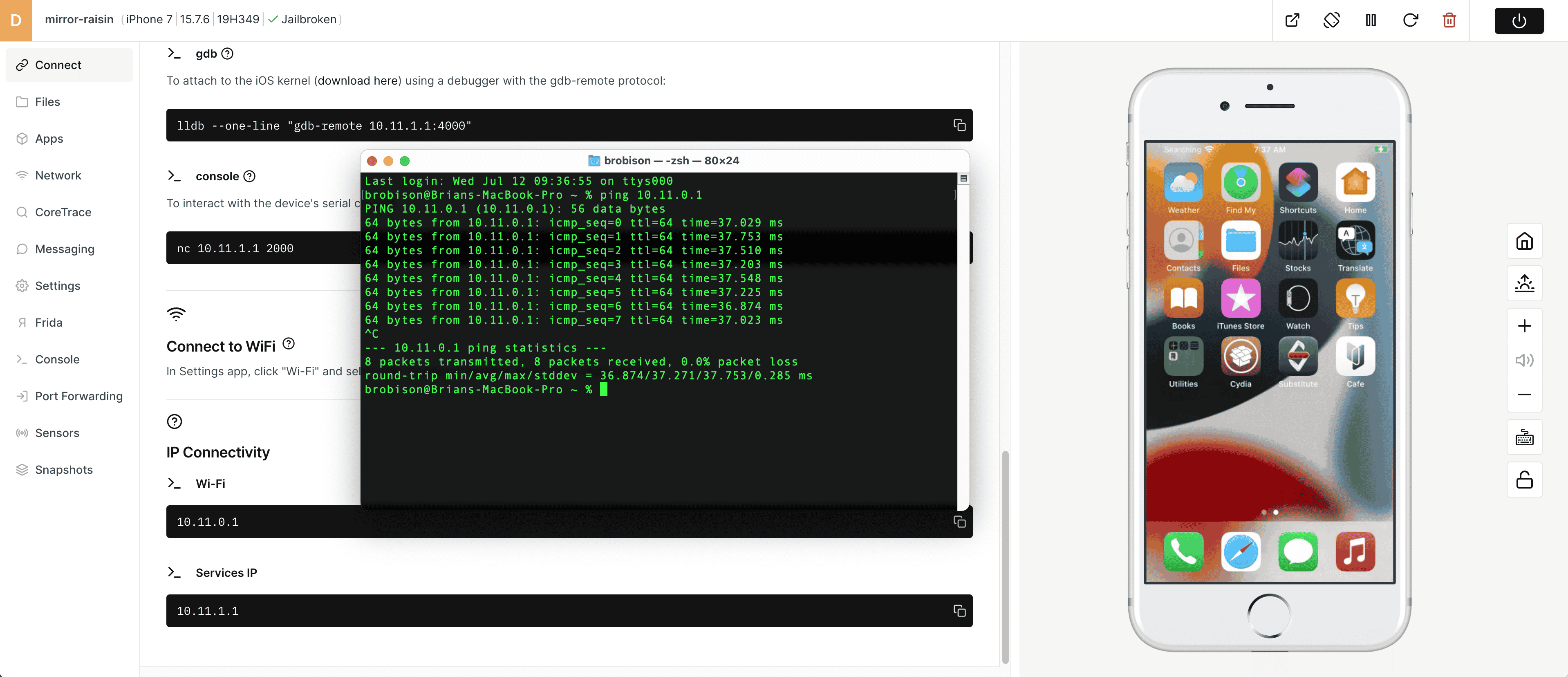
3) You can also check to make sure you can SSH directly to the device. Enter 'ssh root@IPaddress' - the default password is 'alpine.' When you are finished, you can disconnect from the device's SSH server.
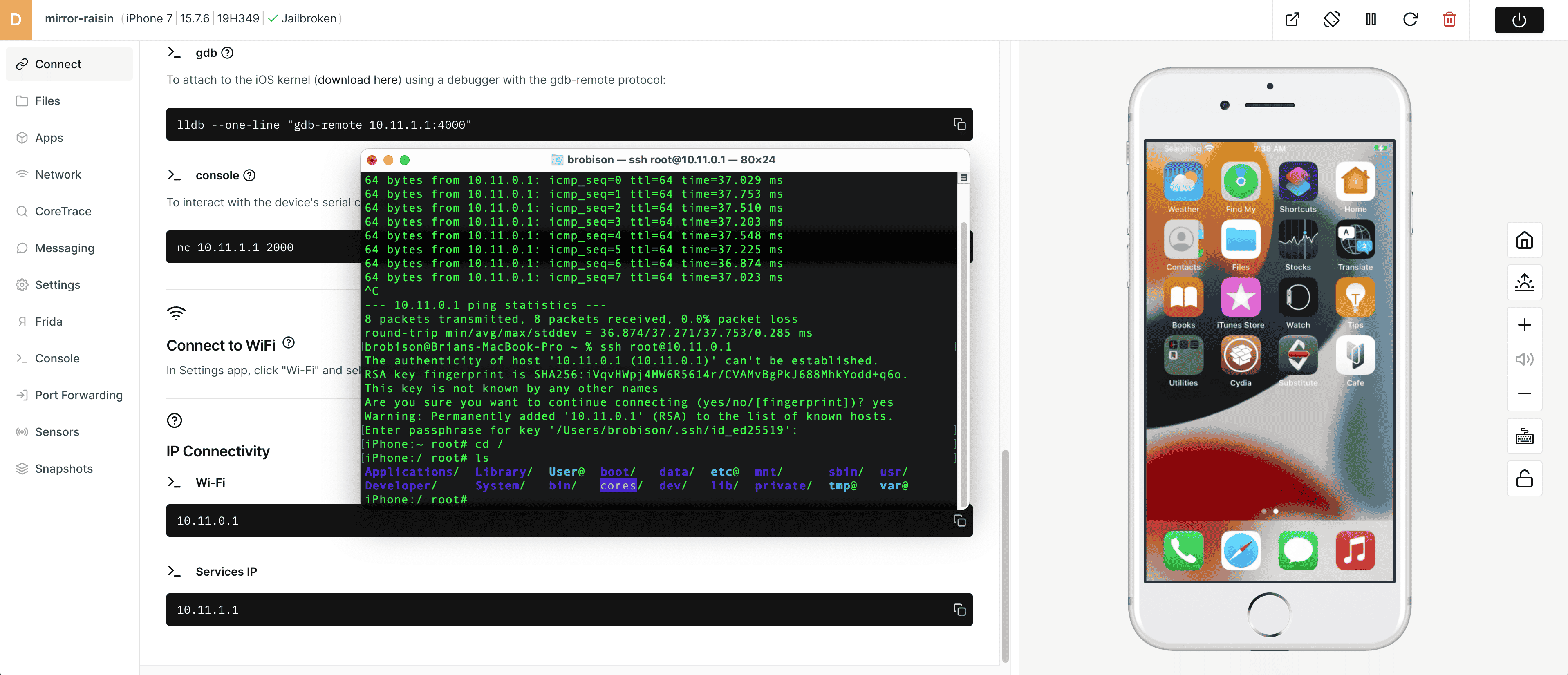
4) Network connectivity to the virtual iPhone is confirmed!
Attaching to USB
Many tools need a direct USB connection on a physical iPhone and this is achieved with your virtual iPhone through a tool called USBFlux. This tool runs locally and creates a faux USB connection over the network (VPN) to the virtual iPhone.
1) To install USBFlux - scroll up (or down) in the Connect tool and download USBFlux for Mac.
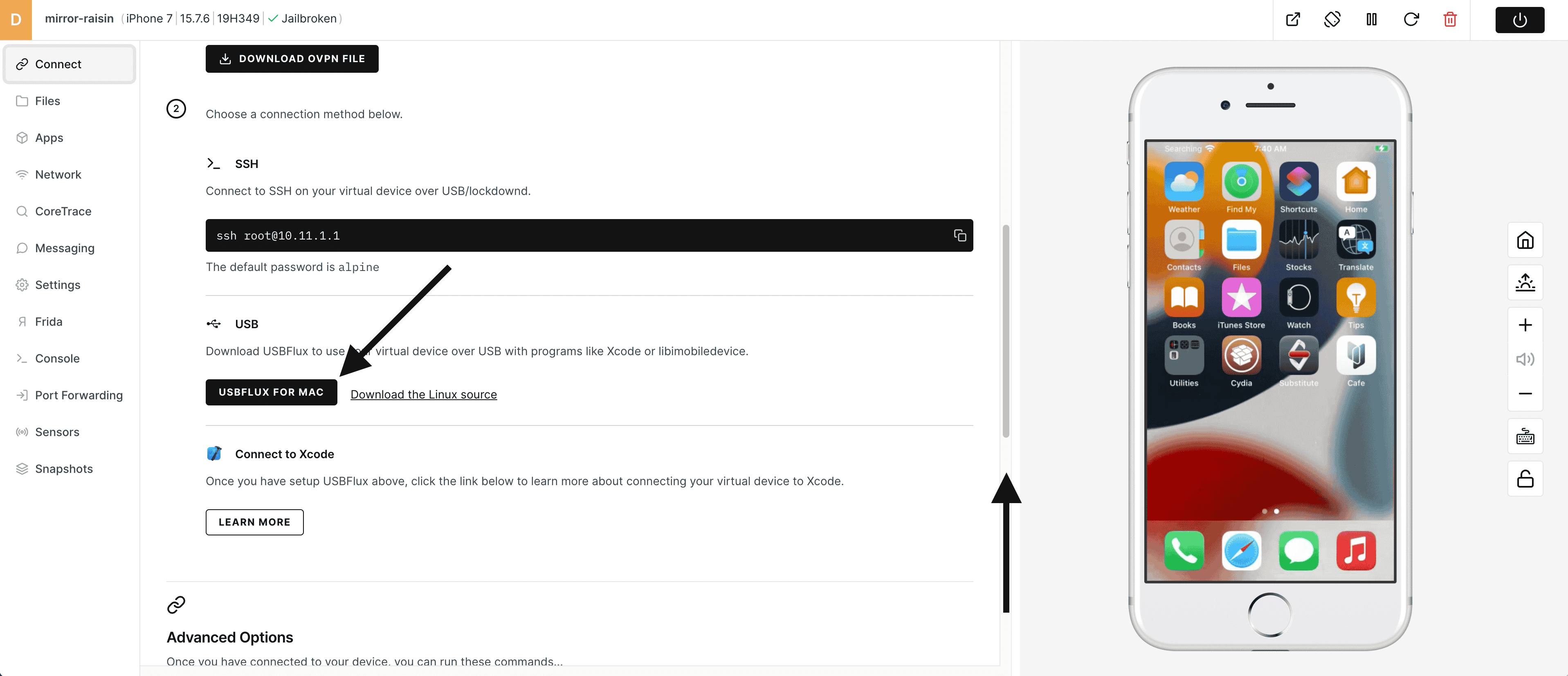
2) Mount the downloaded .dmg file and install USBFlux into the Applications folder. There is a user guide included for more information on the installation process.

3) Upon first run of the USBFlux tool, you will be asked to enter your Corellium platform URL. This is the FULL URL that you use to connect to your Corellium environment. In this example: "https://marketing.enterprise.corellium.com"

4) Enter your Corellium user credentials - this will give you USBFlux to only YOUR running iOS devices. Other users in their environment will have their own USBFlux connections to their devices.

5) After entering credentials, the running virtual iPhones will become available to your local Mac via USBFlux.
6) You now have all the basic connectivity (network and USB) required to begin your testing!
Step 5: Running Corellium Café and Generating Data
Now that you've created your virtual device and have appropriate connectivity, it's time to begin actual testing and discovering of vulnerabilities.
Corellium Café has many vulnerabilities that you can discover.
Local Storage - there are several vulnerabilities in local storage, there may be hard coded credentials, or issues in storing of credit card data.
Network - any app that transmits data over the internet should not rely 100% on SSL/TLS to protect data. You might see some interesting data when you buy a drink.
App Misconfigurations - well behaving and secure apps should follow good hygiene when running on devices like obscuring information when backgrounding and in other places, like debug logs.
Device Integrity - apps should care whether your device has been compromised by jailbreaking. Detecting and bypassing these checks can lead to fruitful data leakage.
To begin finding many of these vulnerabilities, it's important to run the app and generate some data. Some vulnerabilities can only be discovered after data has been created or while sending.
Run Corellium Café
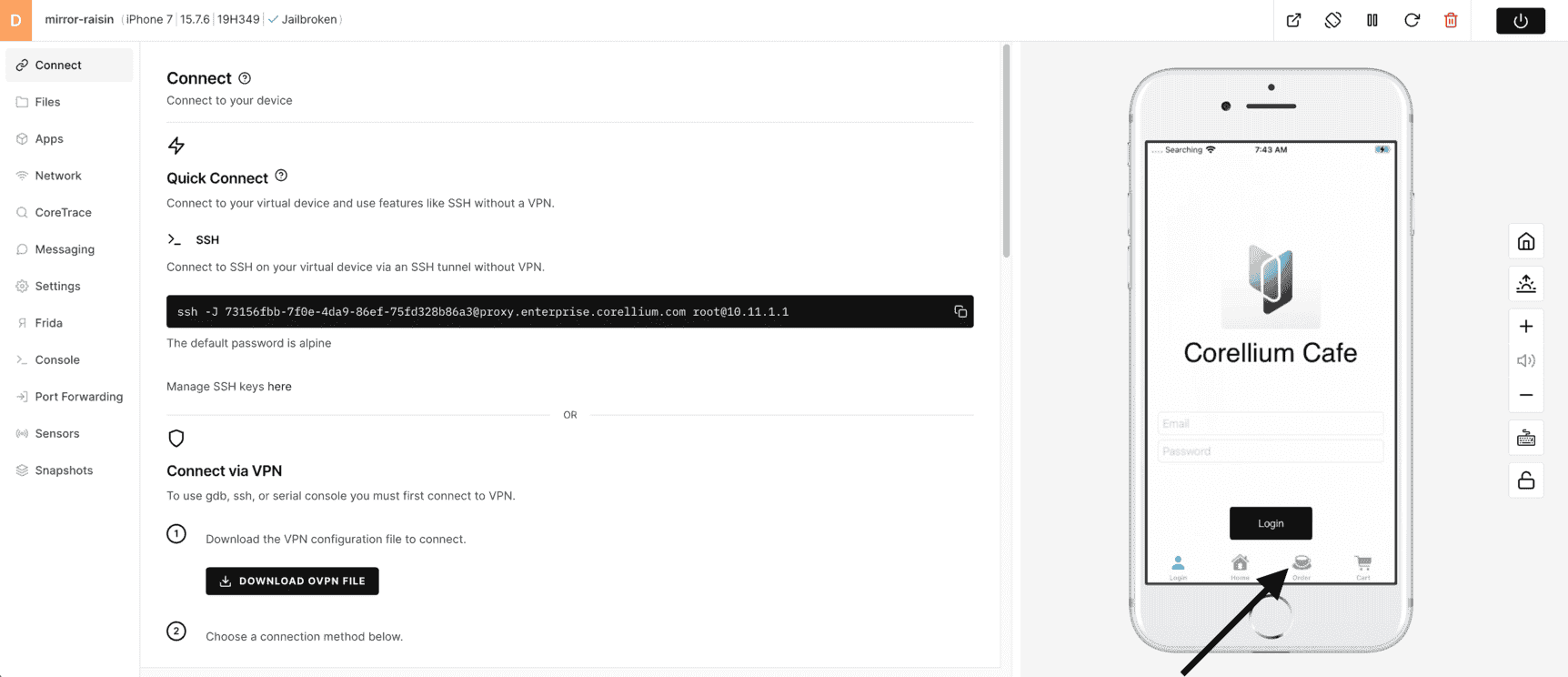
1) Run Corellium Café by clicking on the app.
2) For now, we simply bypass the credentials (HINT - you can look for some credentials during your testing) and go directly into Ordering some beverages.
3) Choose a drink and Add it to your cart.
4) Begin your checkout procedure by selecting the cart.
5) Choose Checkout - notice there's a Promo code field - it might be interesting to see if you could discover what that promo code is... you might be greatly rewarded.
6) Enter your payment information - OBVIOUSLY do not use REAL payment information - this data is sent in a POST to corellium.com, however, there is no system to capture/store this (yet) on our website. Fingers crossed for future versions of Café. Choose Place Order.
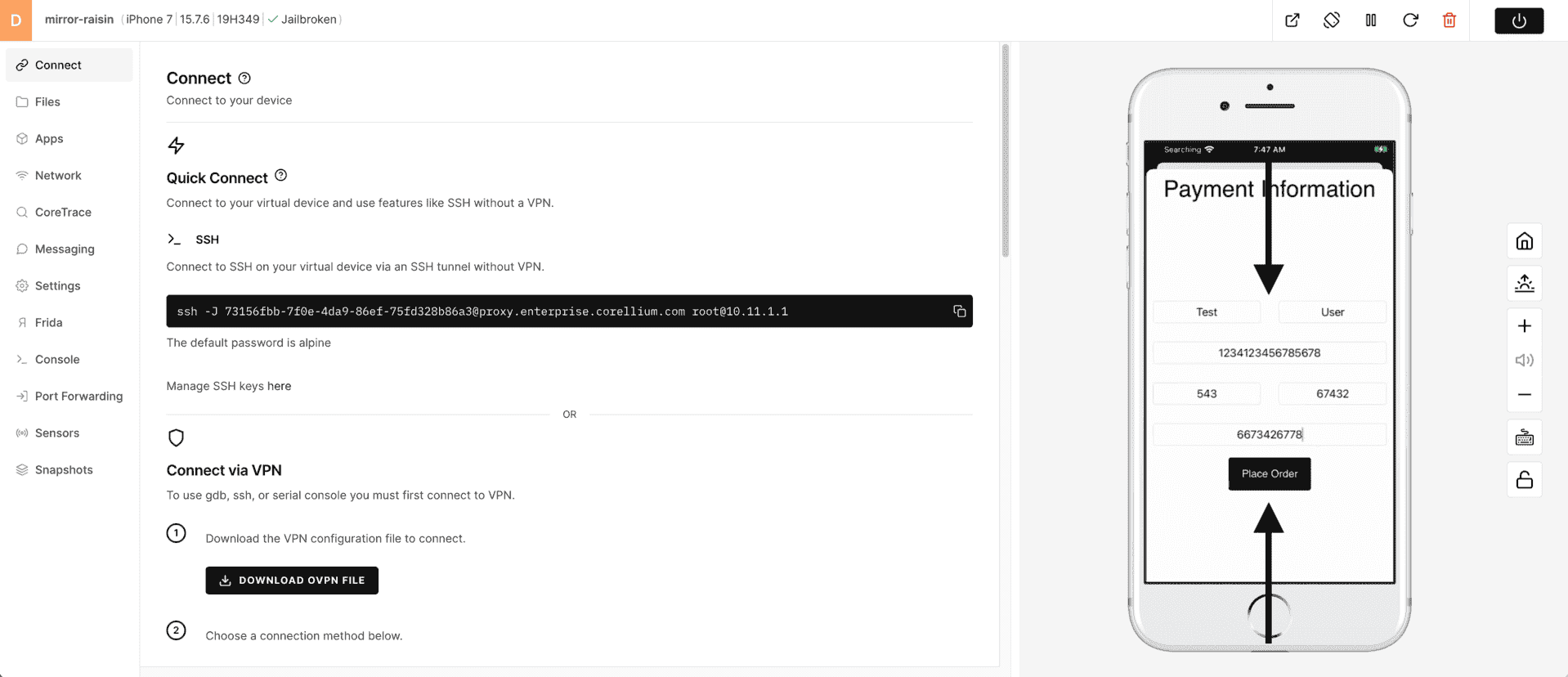
7) Your order has been sent (HINT - there might be some interesting network traffic for later testing). Get ready to enjoy a tasty beverage - if only this actually worked!

8) You've now run through a complete ordering process to create data that has been stored on the device and transmitted over the air. Now you can really dig into the app to find how well the app handled that data.
Step 6: Get to Testing Already!
The goal of this guide and the Corellium Café apps is to introduce you to conducting a mobile app pen test using a virtual Corellium device rather than a physical device. This guide does not "teach" you how to conduct a pen test but rather, helps you navigate the use of Corellium allowing you to use your skills and techniques to find the vulnerabilities in the Corellium Café app.
This guide is broken into several sections. There may be multiple vulnerabilities in each section for you to discover.
If at anytime you would like to jump to the answers - check out the Answer Key at the bottom of this page.
Section 1: Data at Rest - Local Storage Vulnerabilities
Mobile apps often create and store data locally. Sometimes this includes cached data, saved payment information or even hard coded credentials. During the above step, you definitely entered some data in this app to order your first beverage.
Use your skills and tools such as Objection to explore Corellium Café the app and the data it created.
On iOS installing the app creates a data folder that contains the data at rest. This folder is assigned a randomized GUID as the name and can be quite difficult to find. However, Corellium's Files tool makes this VERY easy.
Finding the Corellium Café Data Folder
1) Click on the Files tool in the tool bar.
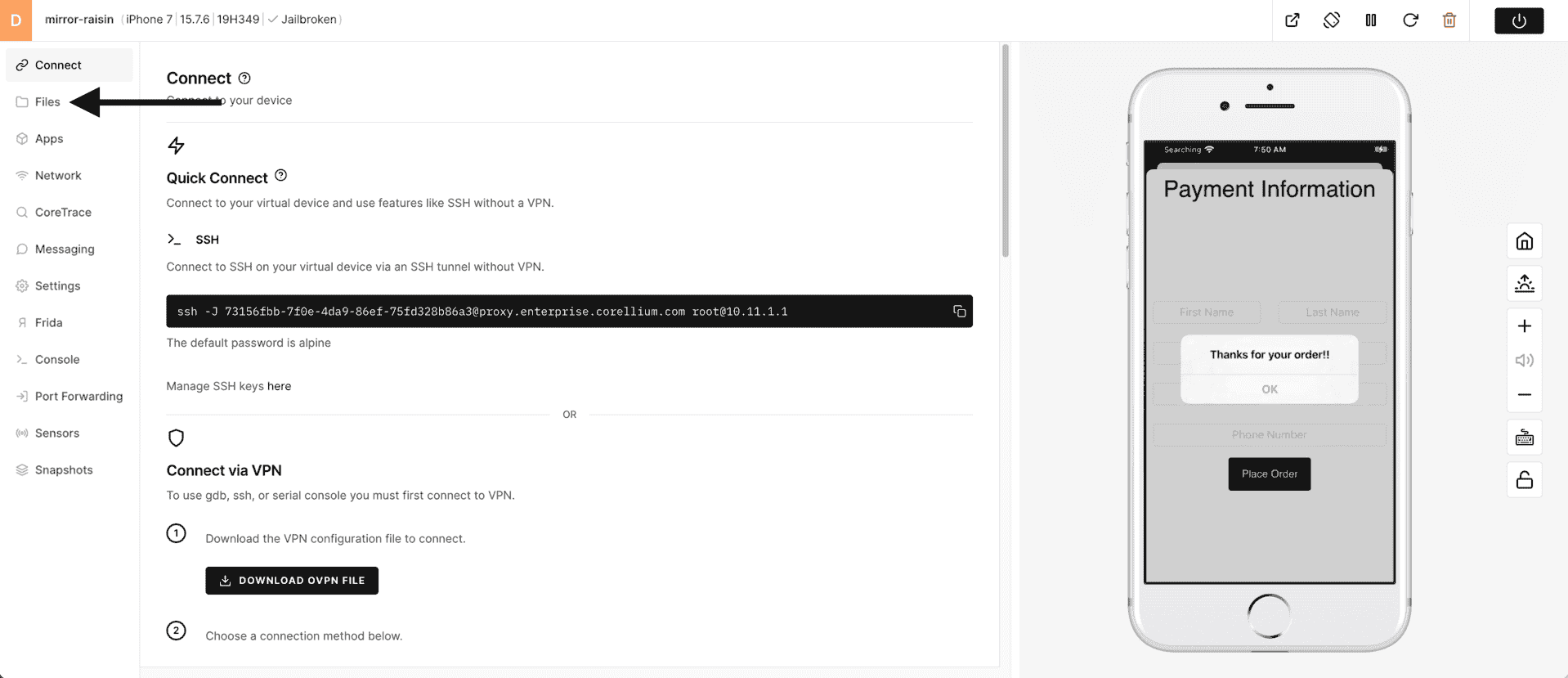
2) Because you have a fully Jailbroken iPhone 7, you are able to see every file on this device and you have full access to download and update files.
Use the Files tools to browse the filesystem to /var/mobile/Containers/Data/Application/ and you will see a LOT of GUID named folders.
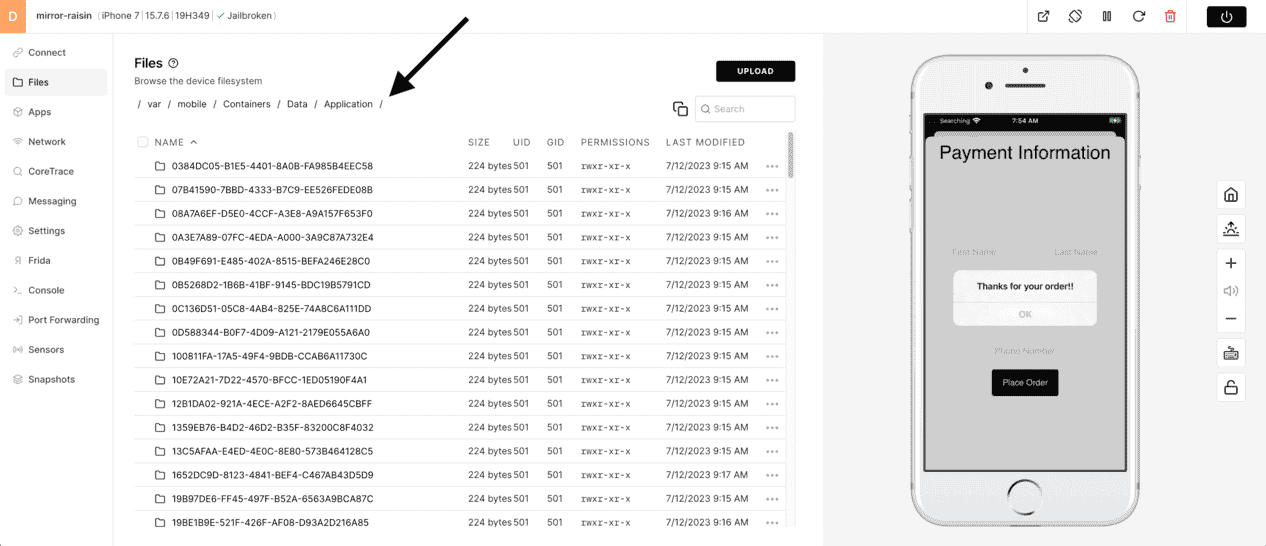
3) The easiest way to find the folder created when Corellium Café was installed is to sort the "LAST MODIFIED" column so the newest folder is at the top.
In this example, the newest folder at the top was the LAST app installed - Corellium Café. It is easy to see when the device was created @9:17AM, but the last app was installed @9:32AM.
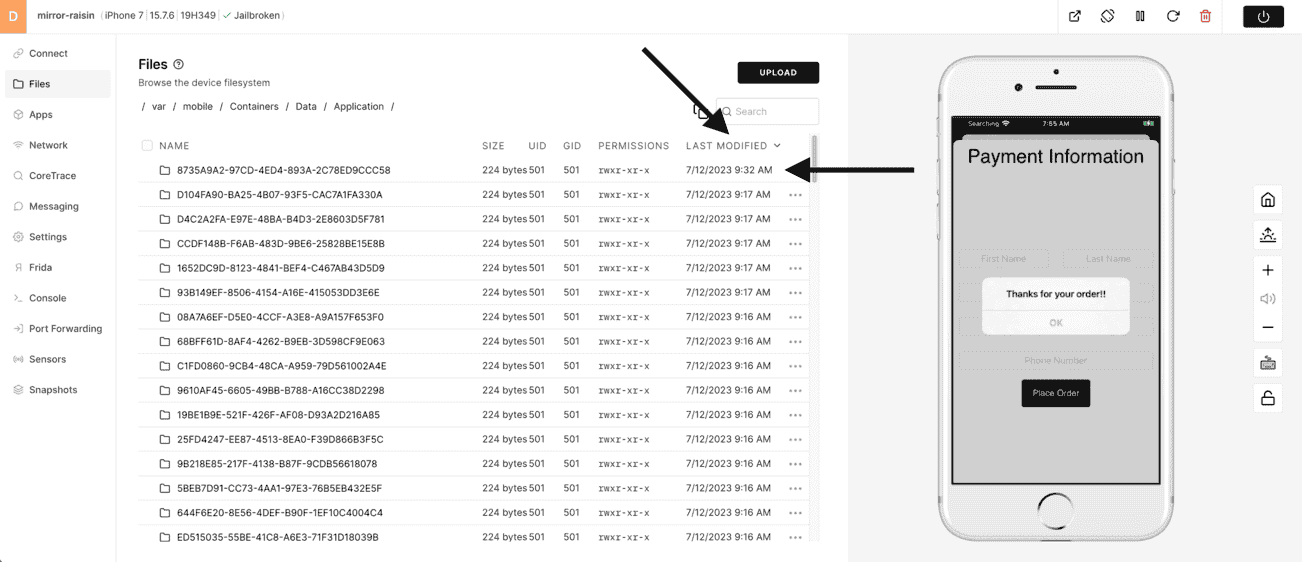
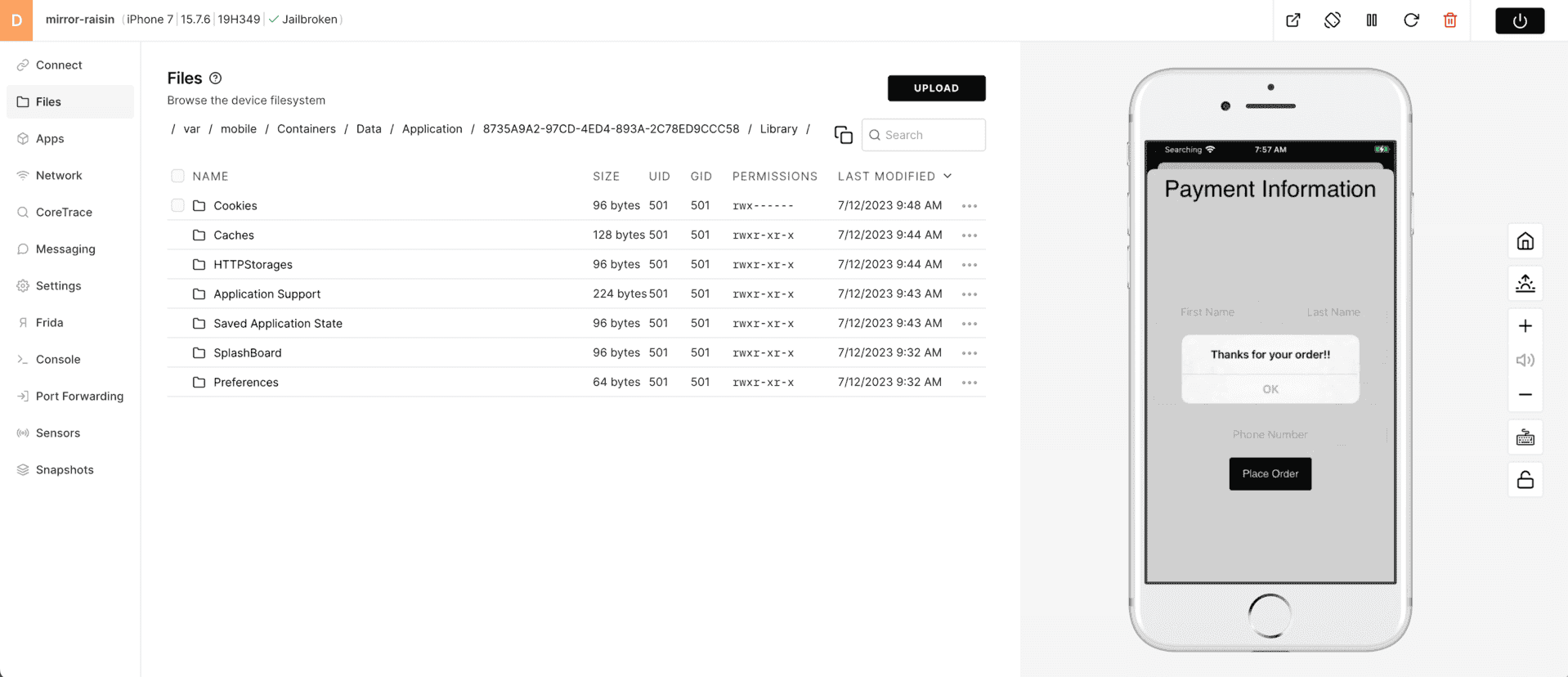
4) This data container folder will contain the data that was cached or saved in a mobile app. HINT - there is GOLD in this directory when looking for data at rest - local storage vulnerabilities.
Section 2: Data in Motion - Network Vulnerabilities
Normally we can trust that SSL/TLS and HTTPS websites/APIs are able to protect sensitive data from introspection. However, it is pretty darn easy for attackers to establish "man-in-the-middle" scenarios that will allow them break the SSL/TLS encryption and then gain access to the data traveling over the network. They could easily see this data in clear text. For any app, it is critical that developers protect this data further than relying solely on HTTPS connections.
To inspect data being transmitted/received to your virtual device, you can use the Network Monitor tool built into Corellium. Alternatively, you can redirect the traffic from the virtual device through a tool (like Burp Suite) running locally on your computer. See this Burp Suite guide to configure your virtual iPhone to redirect its traffic through Burp.
Corellium's Network Monitor performs a built-in man-in-the-middle type of attack by stripping out all SSL/TLS encryption in the network communication. If an application does not obfuscate or encrypt its data separately (from HTTPS), you will be able to see the traffic in clear text.
Use Network Monitor to Capture Traffic
1) Select Network from the tool bar.
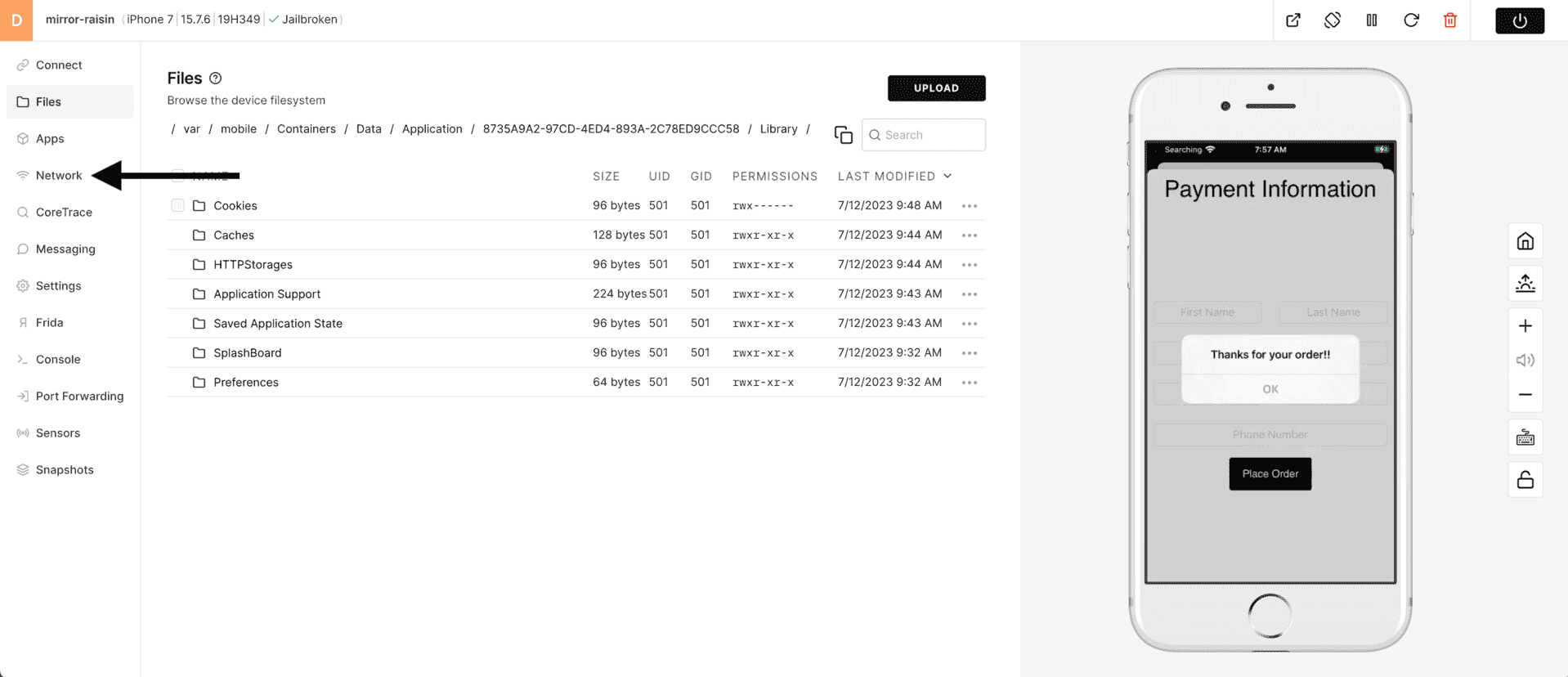
2) Click on Start Monitoring to begin network introspection on HTTP/HTTPS (port 80 and 443).
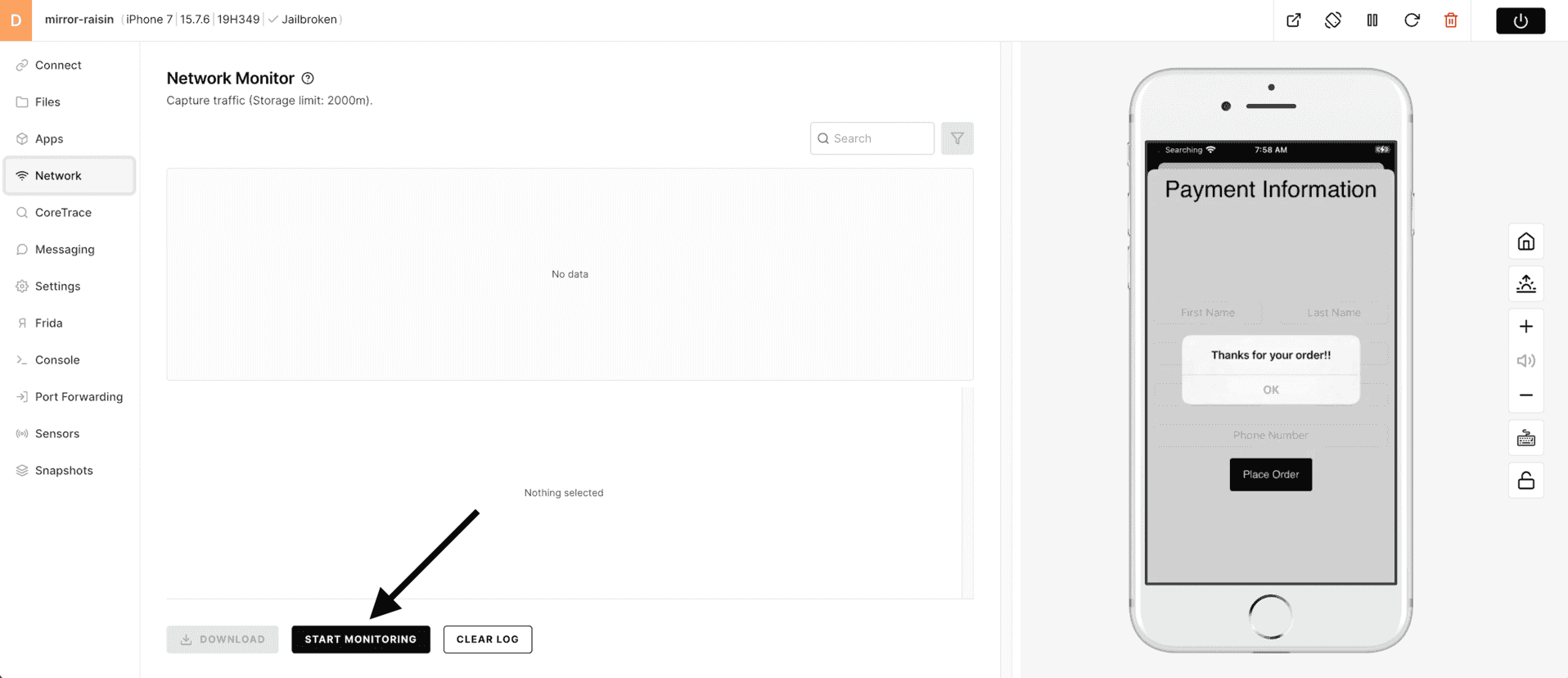
3) When your app sends/receives data (on port 80 or 443), it will be visible in the Network Monitor. You will be able to get Overview information as well as see the Request and Response data in clear text. (HINT - if you were to order another tasty beverage - you might see something valuable here).
4) When you are finished with Network testing, choose Stop Monitoring. You can also clear and/or download a complete log file of the network capture from this page.
Section 3: Application Misconfigurations
Mobile app developers, like all developers, are usually under pressure to deliver apps within short timeframes. While most developers have good intentions and are not malicious, sometimes short cuts or misconfigurations can accidently remain in production builds. In fact, misconfigurations or forgotten hard coded data (like passwords) are extremly common and can lead to massive data breaches.
Misconfigurations can be found in app configuration profile files and can be found by unzipping the .ipa file locally and exploring the many .plist configuration files. Other configuration data or even hard coded credentials can be leaked through cached screenshots or debug logs.
Use Corellium's File browser to look at the data that is saved and contained within the app's data container directories and you can use Xcode to explore debug logs.
Section 4. Runtime Manipulation
Well designed mobile apps should attempt to verify the integrity of the mobile device before allowing access to sensitive portions of the app. This device "checks" can easily bypassed by using runtime manipulation (hooking) to feed false information to the application or change information at run time.
Corellium includes one of the most popular tools, Frida to perform these actions. There are some example Frida scripts that are included - to get a feel for how Frida works.
1) Choose Frida from the tool bar.

2) Some example Frida scripts are built into Corellium to get a feel for how this process works.
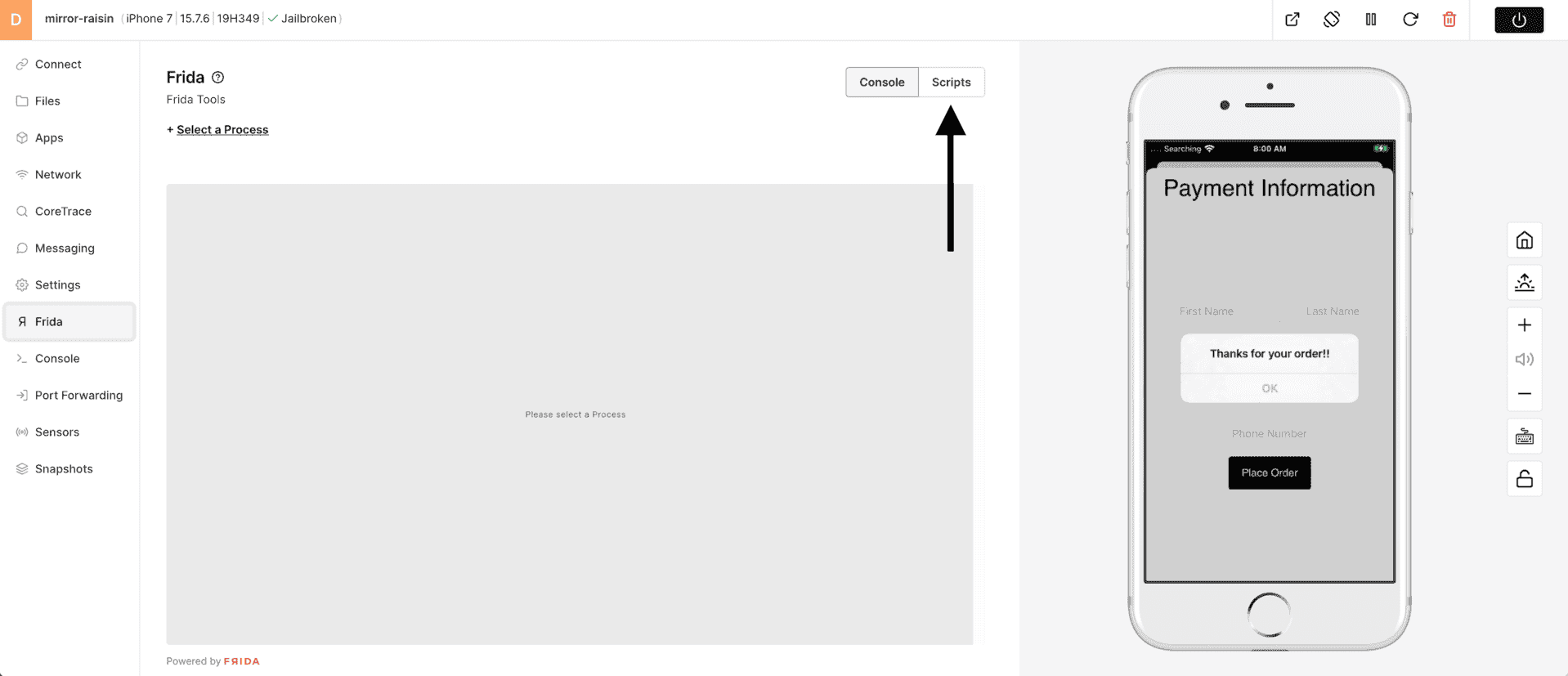
3) This example script is for hooking Safari and replacing a string while the app is running.
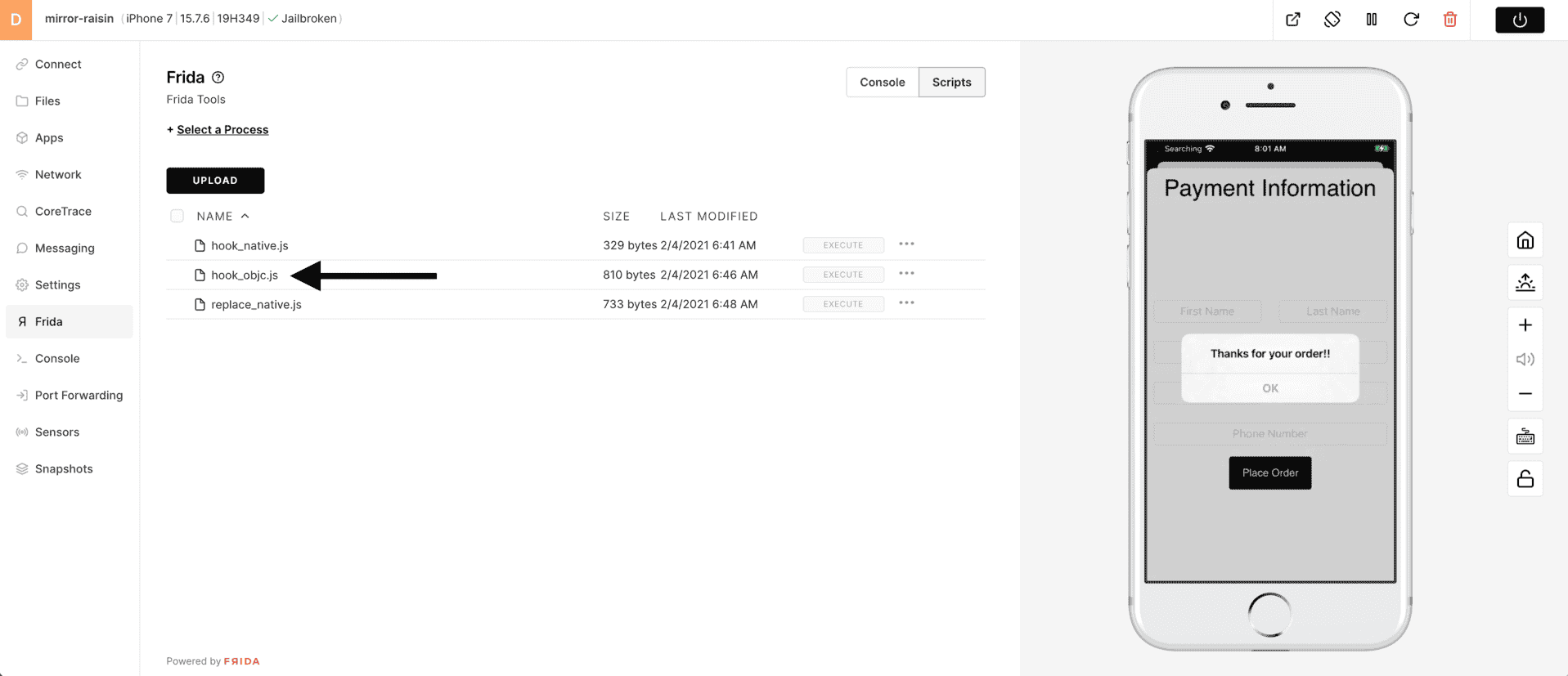
4) To view the script (or to edit) click on the "three dots" and choose Edit.
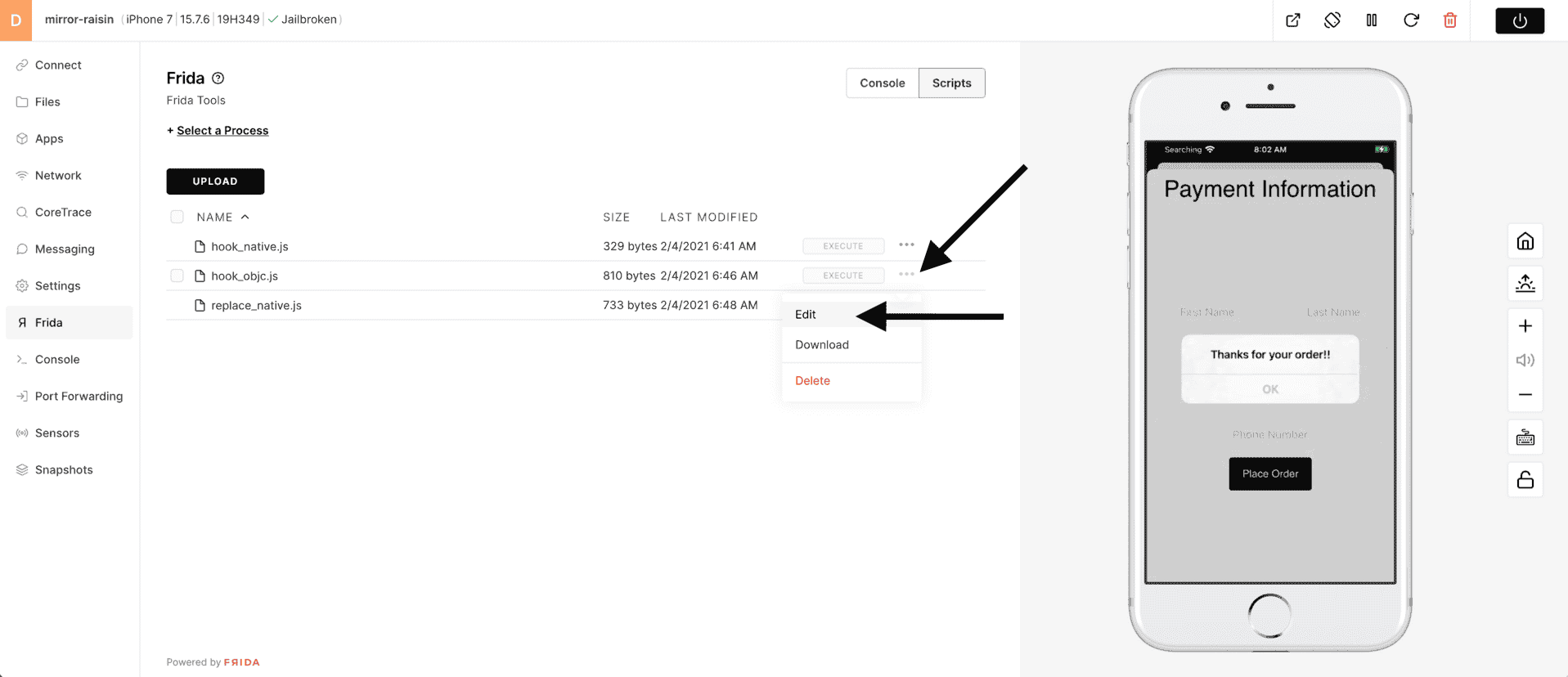
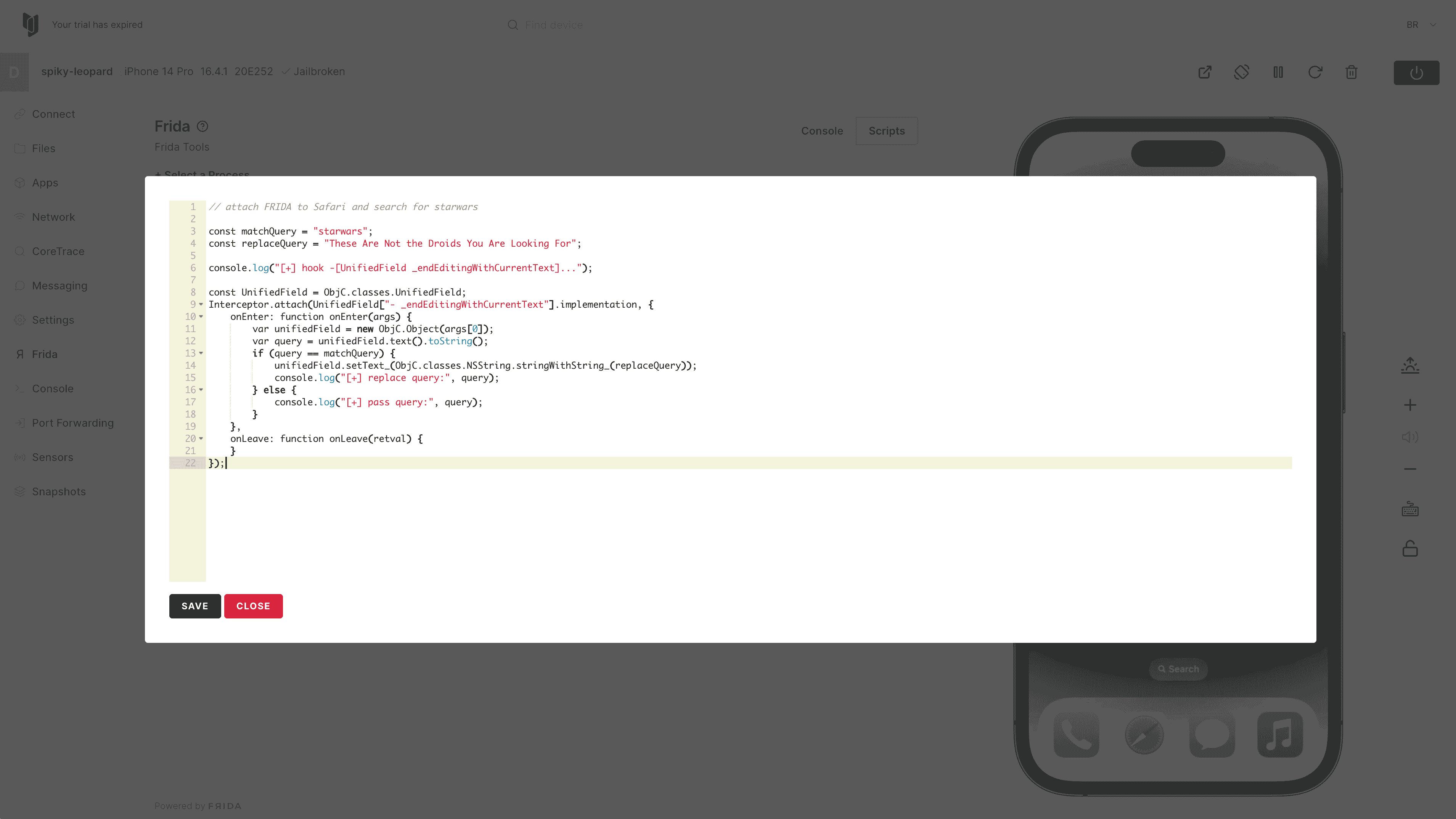
This script is designed to hook Safari and replace the string "starwars" with the string "These Are Not the Droids You Are Looking For" when entered into the app. When you are done reviewing the script, click Close.
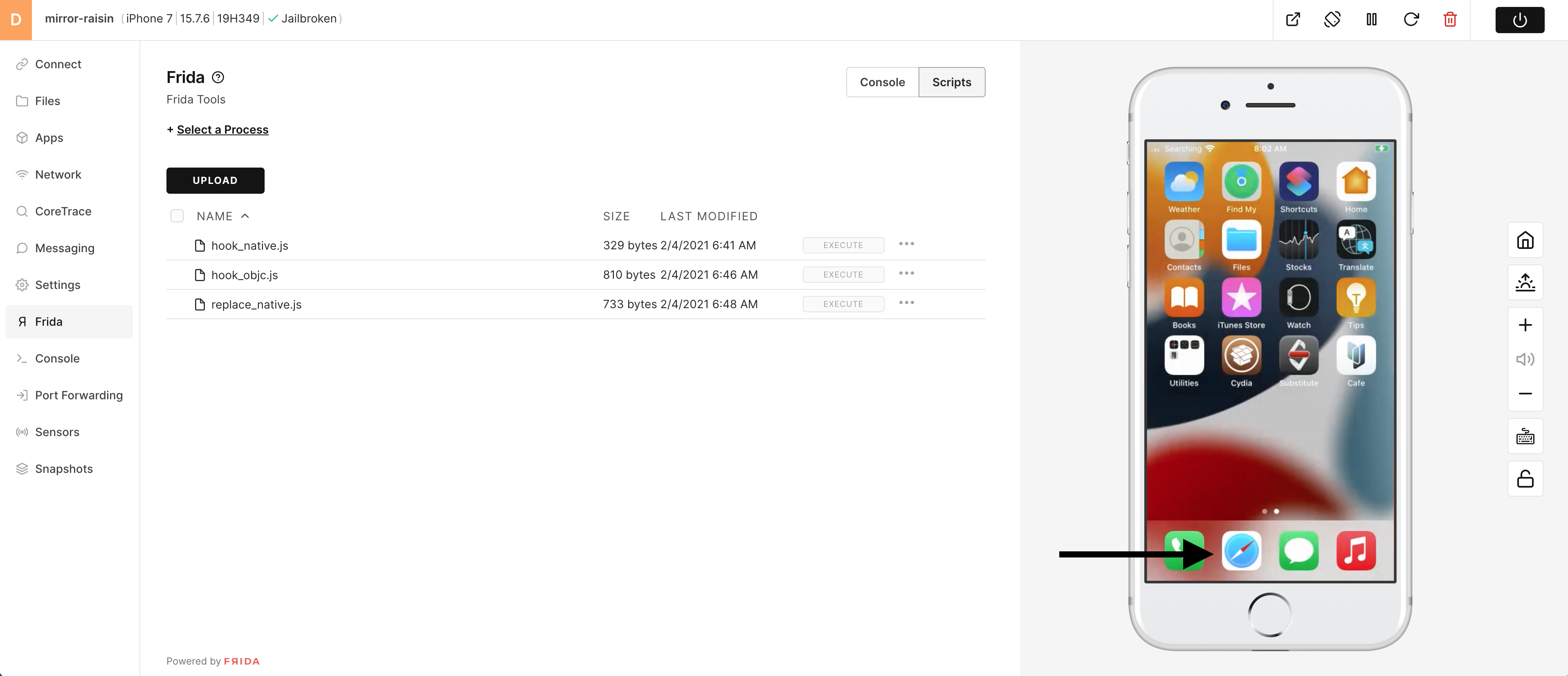
5) To run this example script, launch Safari on the device.
6) Click on Console.
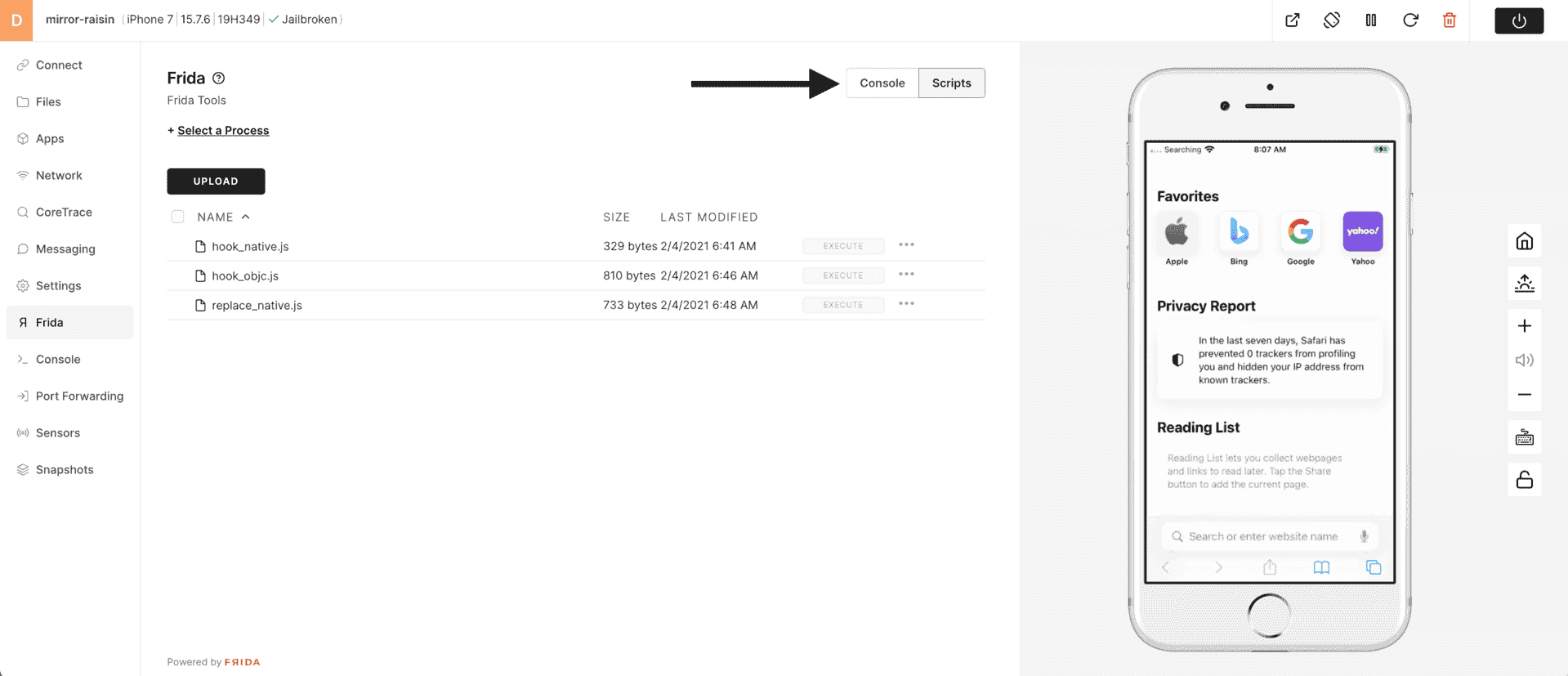
7) Choose Select a Process.
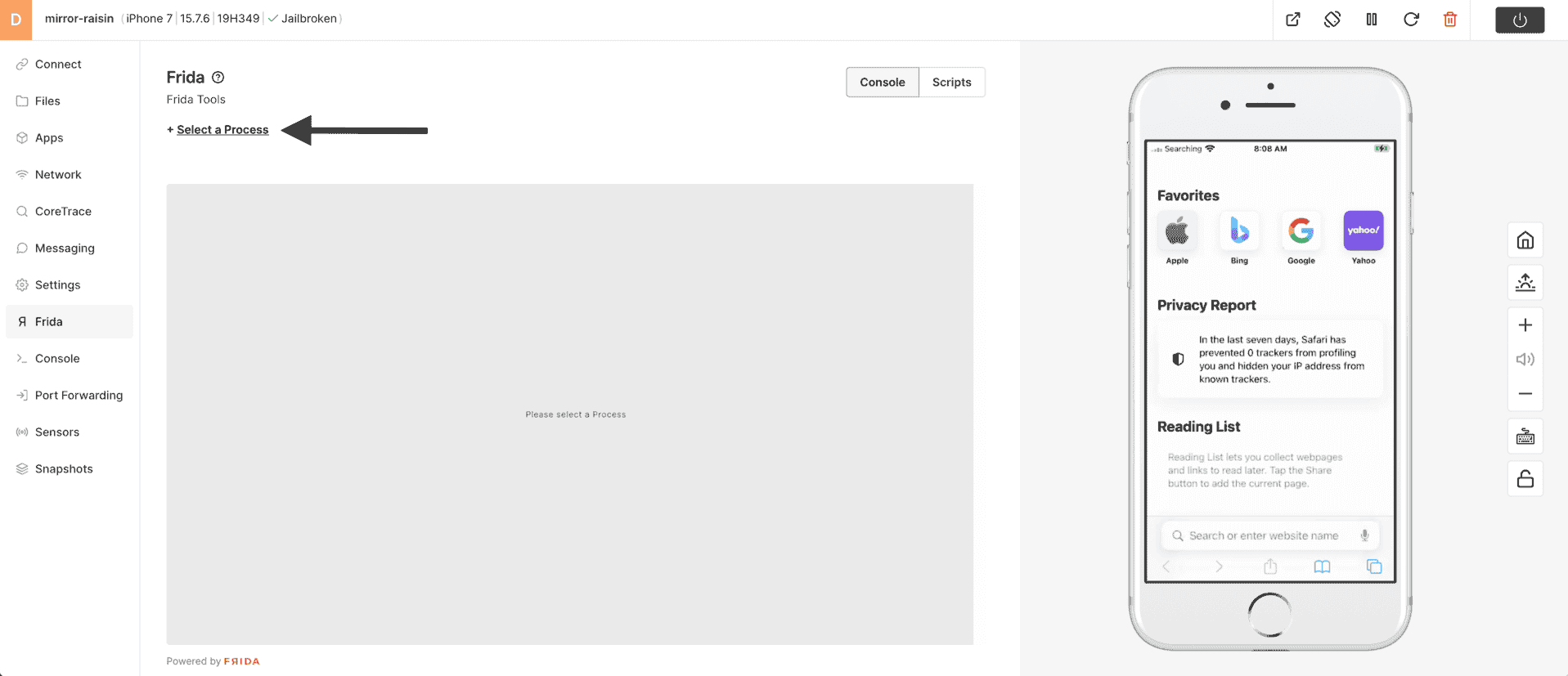
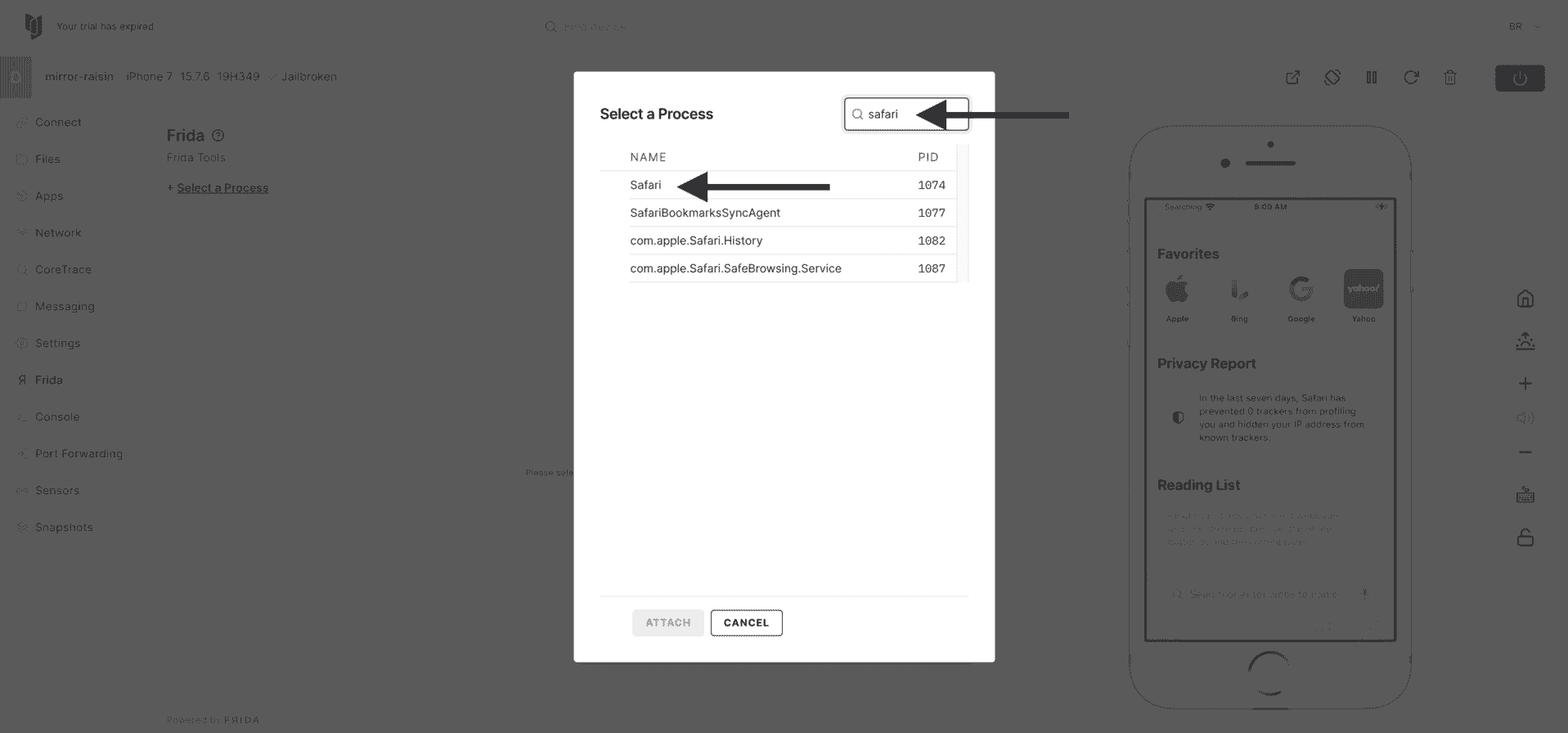
8) Search for and choose Safari.
9) Choose Attach to begin hooking Safari with Frida.
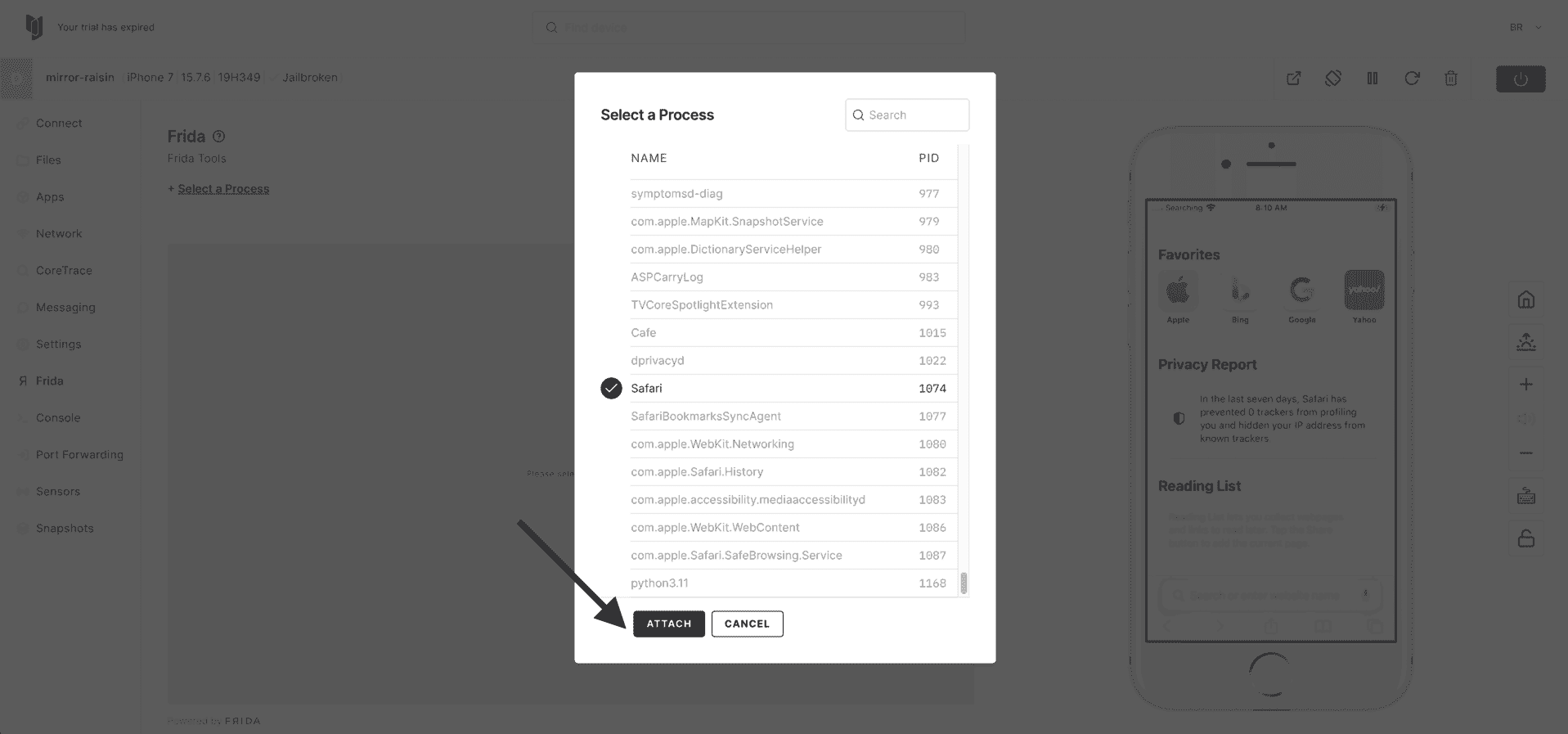
10) Frida should now be running and hooked into Safari (PID) - click on Scripts to choose the example Frida script.
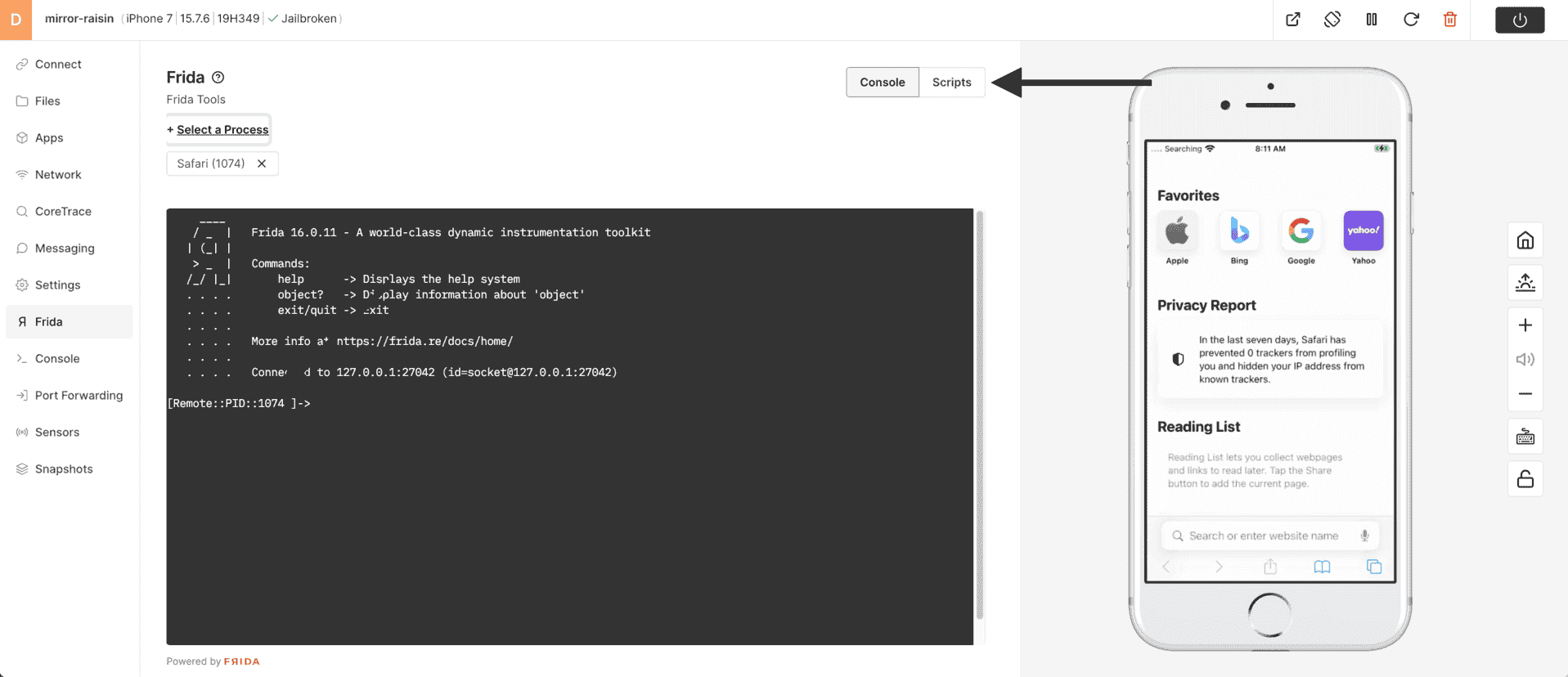
11) Choose Execute.
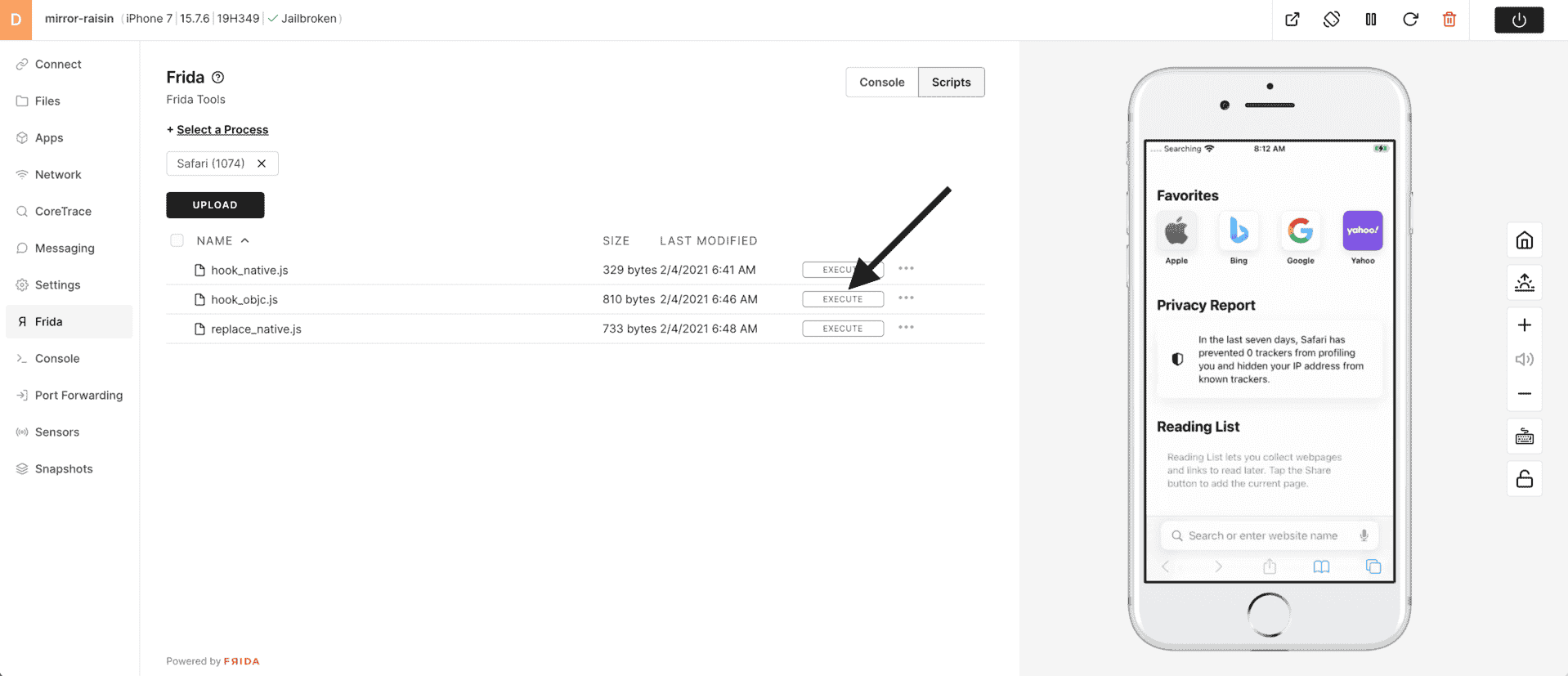
12) Click on Console to go back to the Frida console.

13) Click inside the Frida Console and verify that you do want to load the new script - answer 'y'
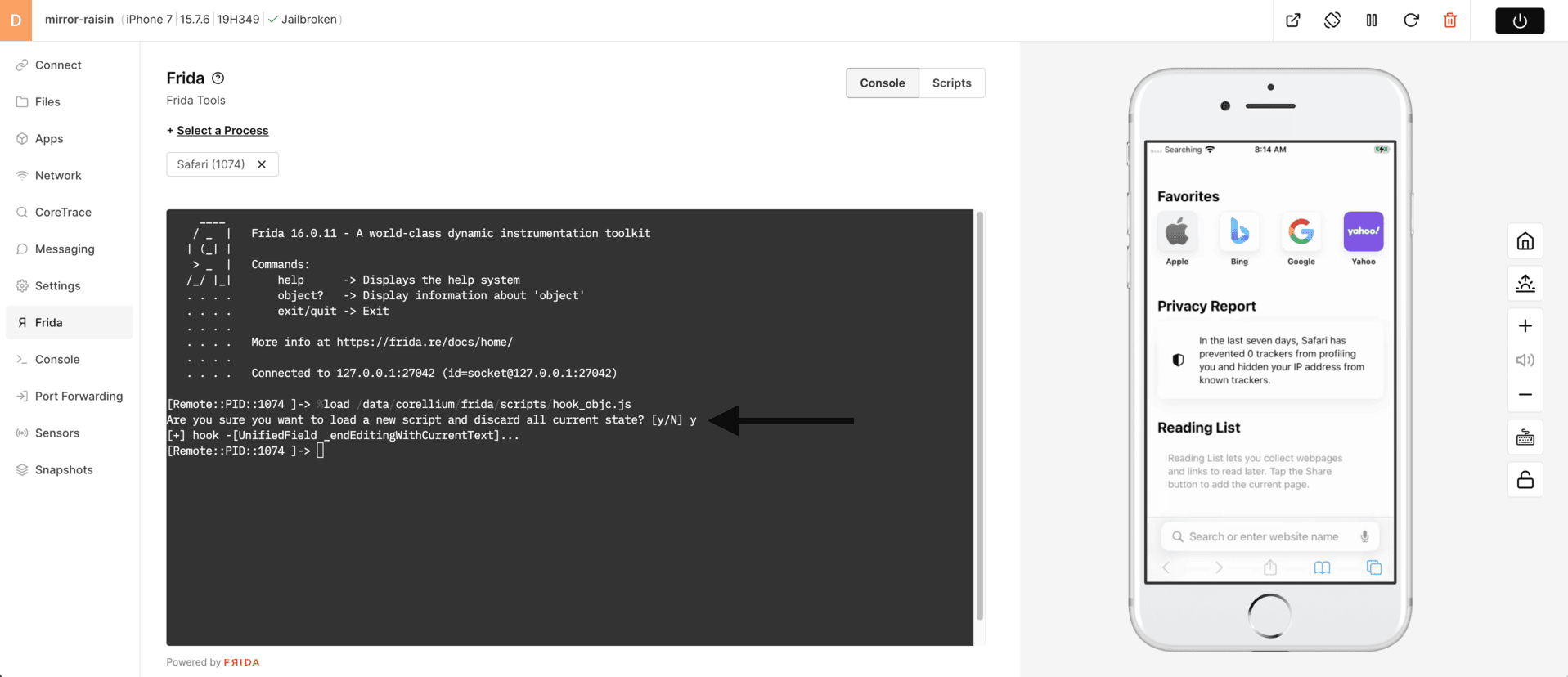
13) Enter 'starwars' into the Safari URL/search field. You might even try other variations like 'STARWARS'
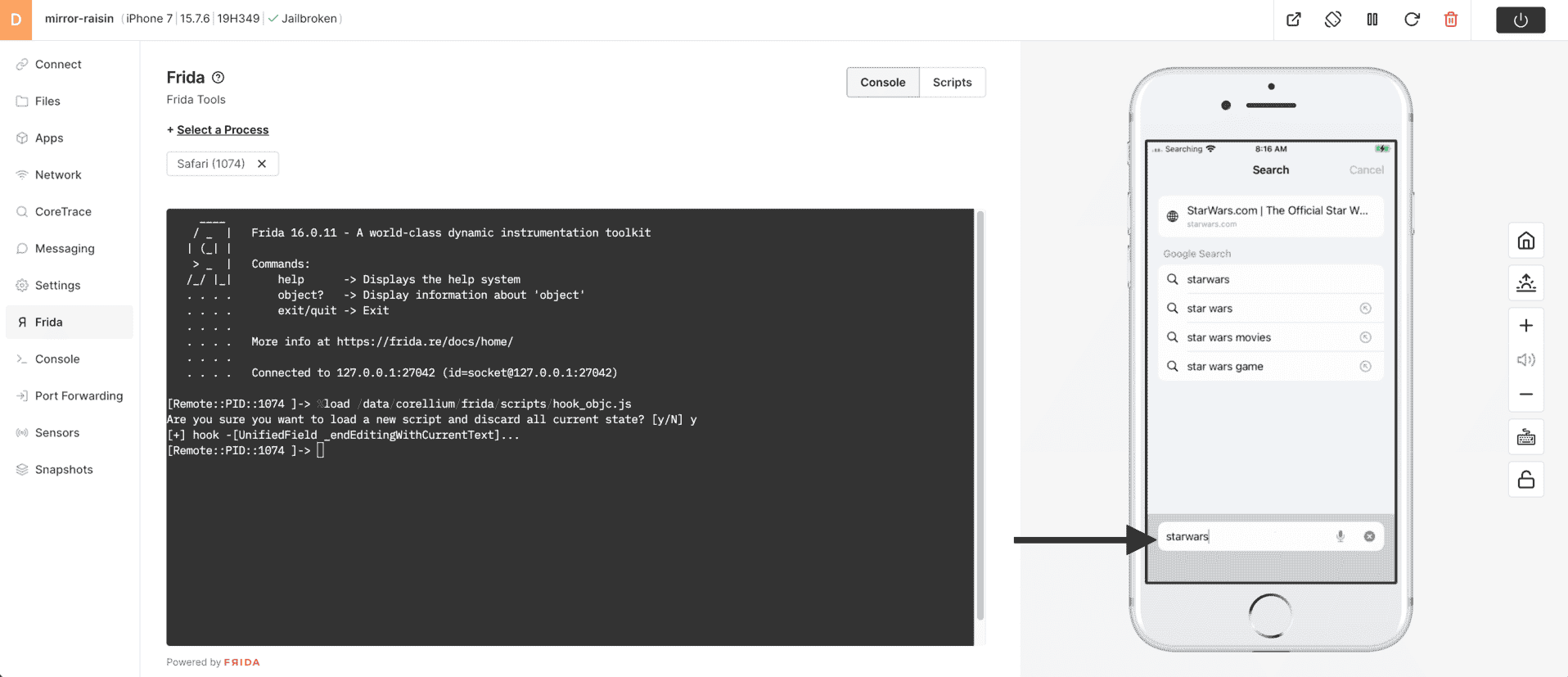
14) You will notice that when the correct string "starwars" is entered, Safari goes to "These Are Not the Droids You Are Looking For" instead of the original search term. You can also see the the result of a non-matching string "STARWARS" and notice how Frida passes the value through unchanged.
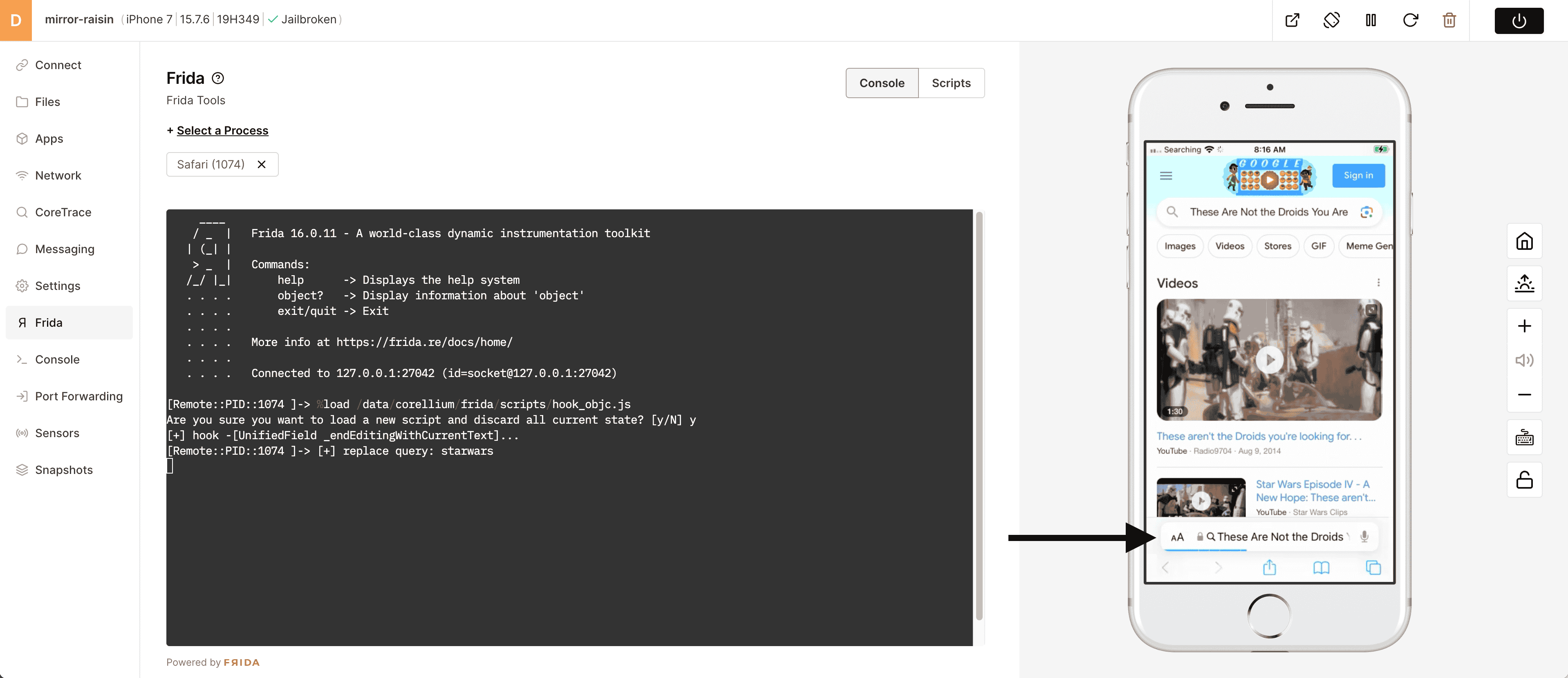
15) You can use Frida to bypass all kinds of runtime checks that mobile apps do. This can be very handy when trying to test or access secure parts of mobile apps.
Continue your Testing
At this point, we have given you some hints as well as shown you how to use some of the built-in tools as well as 3rd party tools.
Now, it is time for you to use your skills and tools to see if you can find ALL of the vulnerabilities built into the Corellium Café app.
GOOD LUCK!!!!!!
Conclusion
Thank you for exploring the depths of Corellium Café and immersing yourself in the world of mobile pentesting and appsec.
By delving into the vulnerabilities, we showcased, you've gained valuable insights into the Corellium platform and honed your skills in uncovering and exploiting mobile app weaknesses.
Your dedication to learning and experimenting is commendable, and we hope this experience has provided you with practical knowledge and a deeper understanding of mobile security.
As Corellium Café continues to evolve, we remain committed to enhancing the app, introducing new vulnerabilities, and delivering an even more immersive and enriching experience.
Together, let's stay at the forefront of mobile pentesting and explore the limitless possibilities of securing mobile applications.
Keep hacking, keep learning, and embrace the exciting journey ahead.
PS
Did you enjoy this guide? Did it help you navigate and learn Corellium while performing tasks?
We really want your feedback on this guide as well as the Corellium Café apps.
If you are working with a sales team, please send your feedback to them. Else, feel free to contact Brian Robison - Chief Evangelist to provide him with your feedback directly. THANK YOU!
OH YEAH - One more thing!
How many vulnerabilities did you find? Would you like to see how you did? Did you get stumped?
We will be happy to supply you with the answer key!
