Mobile Vulnerability Research
The Corellium virtual hardware platform enables never-before-possible security vulnerability research for iOS and Android phones with deep forensics and introspection tools. Its high accuracy, Arm-native models enable real platform vulnerability discovery and exploit validation.
Advanced mobile security tools
Perform vulnerability and exploit research with powerful OS kernel, file system, and network layer tools.
On-demand access
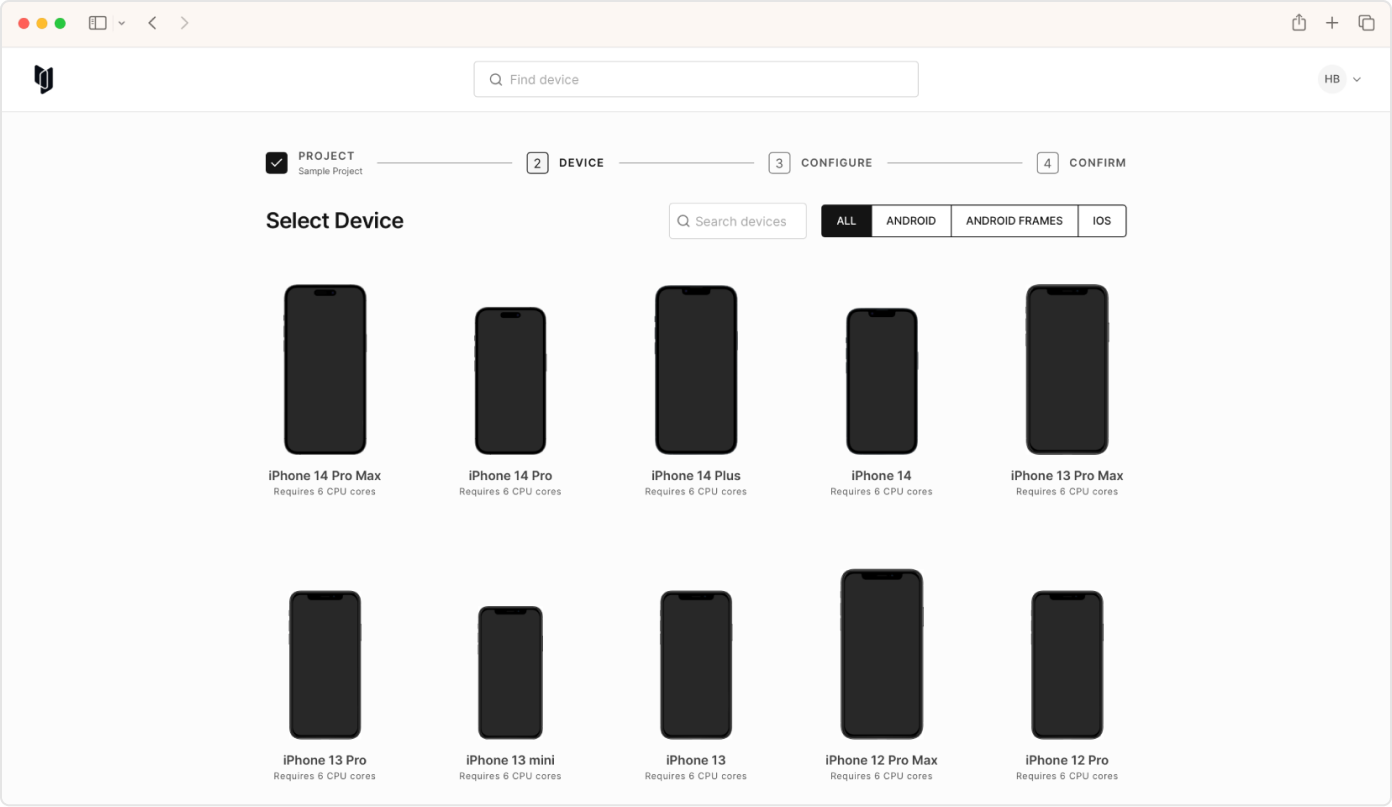
Spin up devices in no time and integrate them with your security tooling.
-
Select from the most comprehensive list of device and OS combos available, including betas.
-
Run, research, and test production code without modifications and recompiles.
-
Integrate other security tools and your workflows through our robust APIs.
-
Perform full-stack security research of mobile devices, OS and apps on a single platform.
Discovery and research
Gain visibility into the OS kernel, firmware functions, activity and subsystem I/O.
-
Seamlessly jailbreak or root any device, no need to rely on security vulnerabilities.
-
View system and kernel logs, and inspect file systems, system calls and network traffic - all in real time.
-
Easily install and run apps in our UI, run scripts and use debug tools like GDB and IDA through our pre-integrated Frida console.
-
Connect to your favorite HTTP proxy/monitor, forward ports, and enable and disable GPU acceleration.
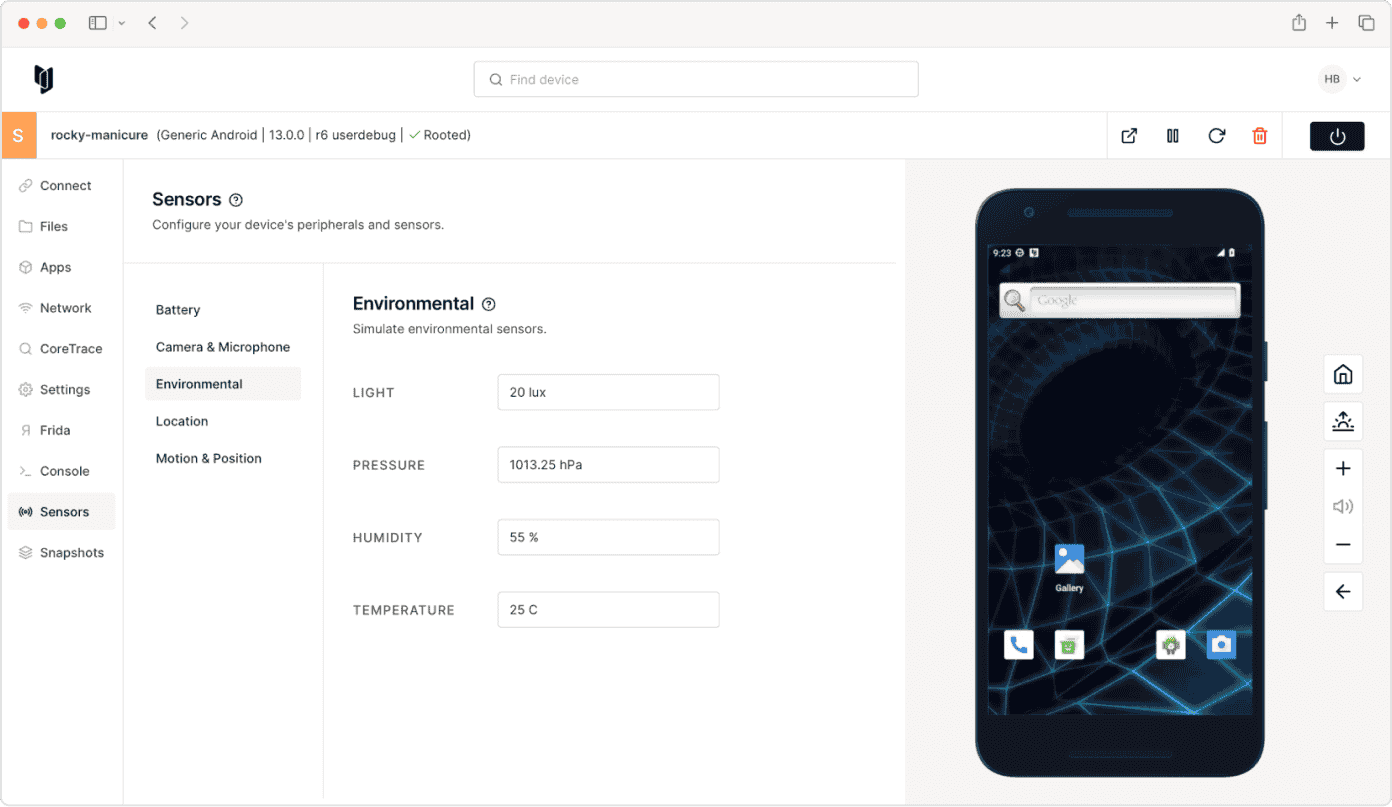
Configuration and control
Set up ephemeral device states to replicate real-world environments.
-
Set battery charge level, health, connection type and status.
-
Set environment temperature, lighting, pressure and humidity.
-
Configure GPS location coordinates, altitude and time offset.
-
Modify acceleration, gyroscope, magnetic and orientation settings.
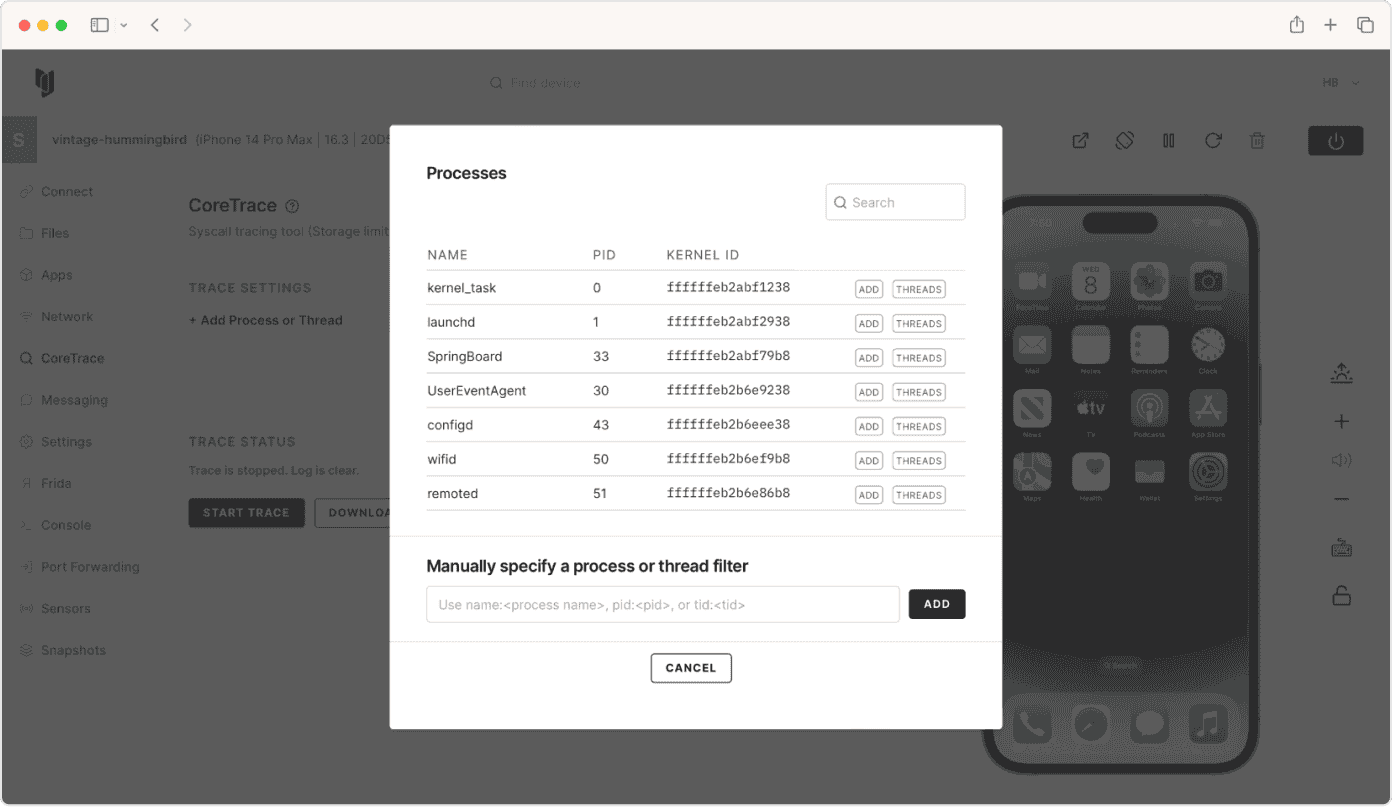
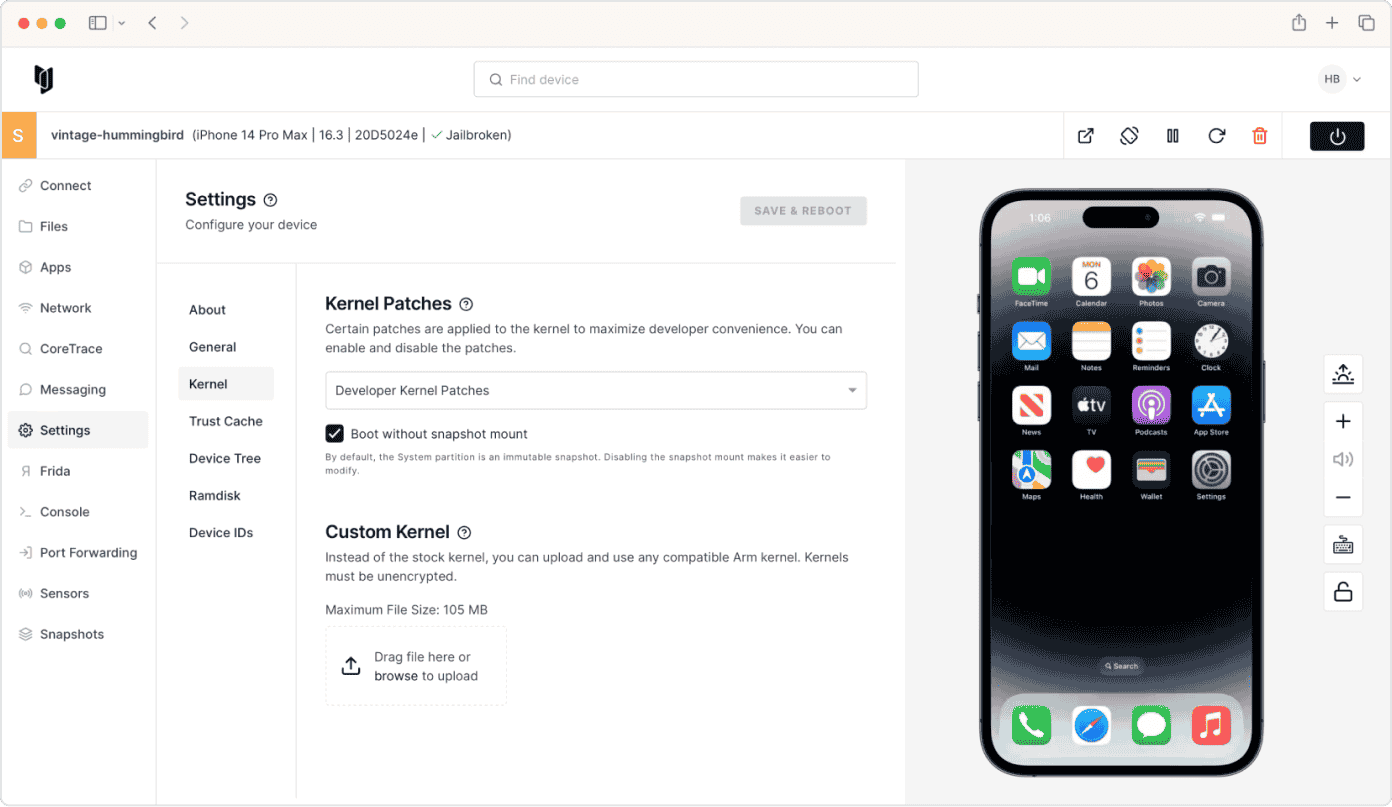
Kernel research
Use advanced tooling purpose-built for advanced security research and kernel debugging.
-
Upload custom kernels and device trees, and enable/disable kernel patches.
-
Pass boot arguments or boot from a custom ramdisk instead of from NAND.
-
Use iBoot to start the application processor instead of booting from the kernel.
-
Modify trust caches, set Device IDs, simulate PAC instructions and more.
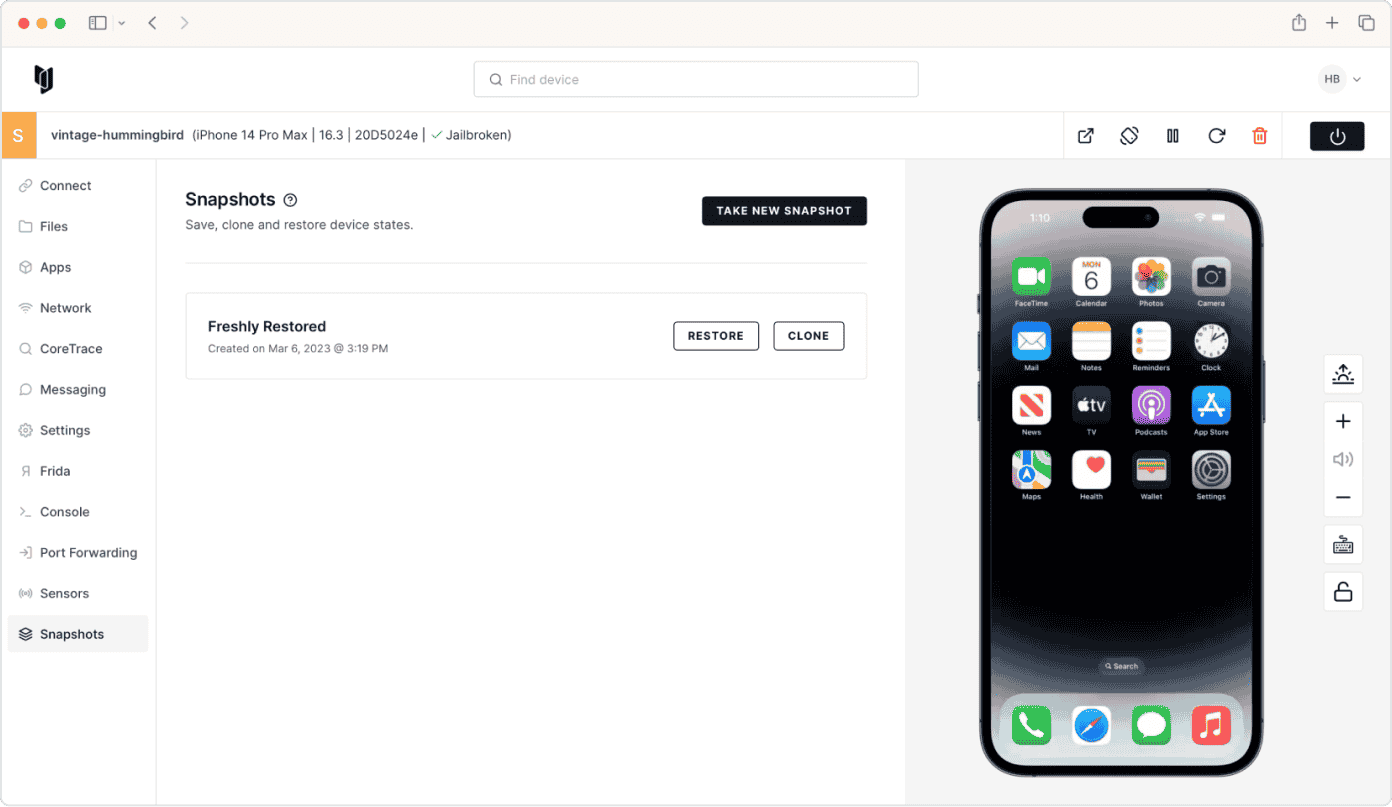
Auditing and collaboration
Easily snapshot and clone device environments.
-
Pause and resume firmware and app operations to facilitate security research.
-
Save and restore device states to simplify reproducibility, record mobile vulnerabilities, and perform audits.
-
Accelerate cross-team research, compliance testing, and researcher training.